Kentik Blog
























In the old days, we used a combination of several data types, help desk tickets, and spreadsheets to figure out what was going on with our network. Today, that’s just not good enough. The next evolution of network visibility goes beyond collecting data and presenting it on pretty graphs. Network observability augments the engineer and finds meaning in the huge amount of data we collect today to solve problems faster and ensure service delivery.
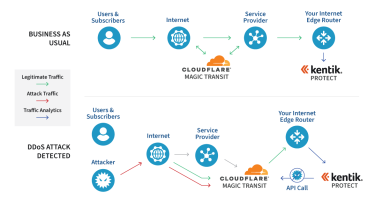
Kentik and Cloudflare have a new integration. Read why and how we’ve expanded our partnership for on-demand DDoS protection.
In this episode of the Network AF podcast, Avi Freedman connects with Ilissa Miller, network whisperer and PR industry veteran.
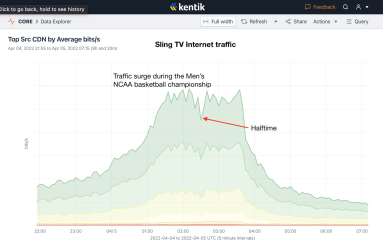
Last night, Kansas topped the University of North Carolina in a thrilling come-from-behind victory to win their fourth championship in men’s college basketball. It was also notable in how viewers saw the game. Instead of being aired on network television like in the past, the game was carried on TBS requiring viewers to have either a cable TV package or use a streaming service to watch the game. Here’s what we saw.
In the second post of this multi-part series, Kentik’s Anil Murty will share how Kentik Synthetics helps you proactively monitor applications and services and troubleshoot the root cause of issues faster.
Jezzibell Gillmore is co-founder and chief commercial officer of PacketFabric. She’s also an expert at learning by doing and connecting by keeping it simple. Hear her story from the Network AF podcast.
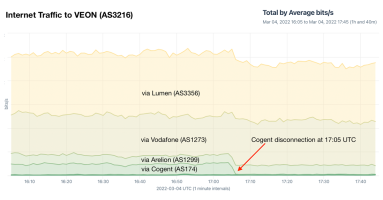
In our updated blog post, read why international telcos Cogent and Lumen say they are taking action against Russia.
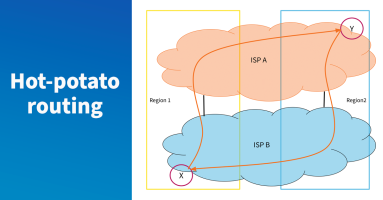
In part four of our series, you’ll learn how to find the right transit provider for your peering needs.
What fun is network observability if you can’t share what you see? Now you can with public link sharing from Kentik. See what’s new.
Alan Cohen, partner at venture capital firm DCVC, sits down with Avi to talk about his experience working in networking and security, the advent of virtualization and multi-cloud, and strategies he has learned throughout his venture capital days to reach and grow entrepreneurs’ businesses.