Kentik Blog
























Maximize your network’s performance with a reliable packet loss monitor. Learn how to proactively identify lost data packets and latency within the cloud.
In our employee spotlight series, we highlight members of the Kentik team, what they’re working on, and their most memorable moments within the company. In this Q&A, meet Solutions Engineer Akshay Dhawale.
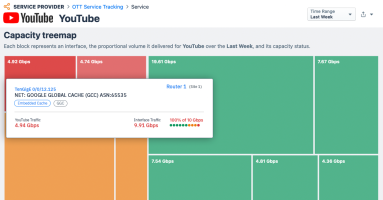
Today we’re introducing the most important update to OTT Service Tracking for ISPs since its inception. To understand the power of this workflow, we’ll review the basics of OTT service monitoring and explain why our capability is so popular with our broadband provider customers.
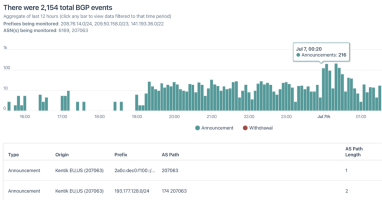
BGP is a critical network protocol, and yet, BGP is often not monitored. BGP issues that go unchecked can turn into major problems. This post explains how Kentik can help you to easily monitor BGP and catch critical issues quickly.
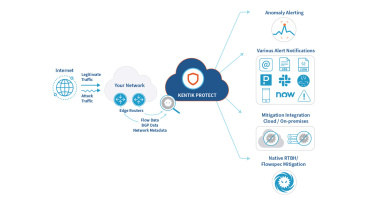
From a threat actor’s side, launching a DDoS attack is both easy and cheap. For a business, it’s costly, disruptive and comes with big hurdles for effective detection and mitigation. Kentik Protect can help.
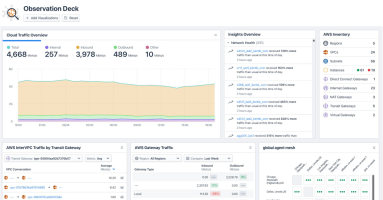
In this post, we offer insight into how to monitor traffic through transit gateways by understanding routing dynamics and cloud architecture. Learn more.
In our employee spotlight series, we highlight members of the Kentik team, what they’re working on, and their most memorable moments within the company. In this Q&A, meet Steven Reynolds, a Kentik UI engineer.
Networking in the cloud can be like a black box. In this blog we discuss five essential properties of network observability for cloud, giving you the ability to answer any question about your cloud network.