Kentik Blog
























The entire reason we have monitoring is to understand what users are experiencing with an application. Full stop. If the user experience is impacted, sound the alarm and get people out of bed if necessary. All the other telemetry can be used to understand the details of the impact. But lower-level data points no longer have to be the trigger point for alerts.
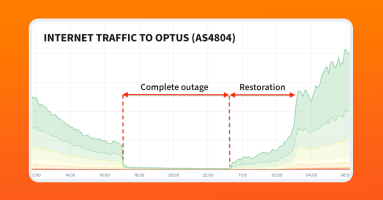
Last week a major internet outage took out one of Australia’s biggest telecoms. In a statement out yesterday, Optus blames the hours-long outage, which left millions of Aussies without telephone and internet, on a route leak from a sibling company. In this post, we discuss the outage and how it compares to the historic outage suffered by Canadian telecom Rogers in July 2022.
Kentik Kube provides network insight into Kubernetes workloads, revealing K8s traffic routes through an organization’s data centers, clouds, and the internet.
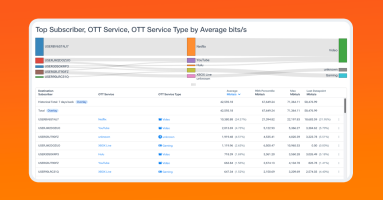
Broadband subscriber behavior analysis is the process of collecting and analyzing data on how broadband subscribers use the internet. This data can be used to gain insights into subscriber needs and preferences, as well as to identify potential problems with the broadband service.
The most noticeable takeaway from All Things Open 2023 was how visibly and demonstrably people were there for the event itself. Not to check a box or browse the swag but to be together, show their support of open source, and glean every last bit of knowledge they could.
If there’s anything I’ve learned, monitoring data is the lifeblood of the business and a superpower for any IT practitioner. Monitoring allows organizations to react to changes, identify and recover, and understand the true health of the business.
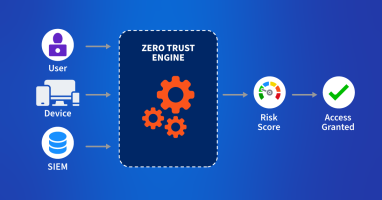
Zero trust in the cloud is no longer a luxury in the modern digital age but an absolute necessity. Learn how Kentik secures cloud workloads with actionable views of inbound, outbound, and denied traffic.
Managing modern networks means taking on the complexity of downtime, config errors, and vulnerabilities that hackers can exploit. Learn how BGP Flow Specification (Flowspec) can help to mitigate DDoS attacks through disseminating traffic flow specification rules throughout a network.
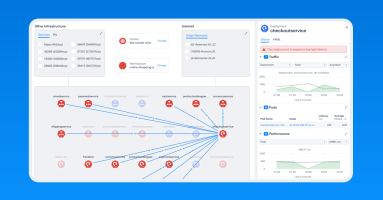
Let me tell you something you already know: Networks are more complex than ever. They are massive. They are confounding. Modern networks are obtuse superorganisms of switches, routers, containers, and overlays; a hodgepodge of telemetry from AWS, Azure, GCP, OCI, and sprawling infrastructure that spans more than a dozen timezones.
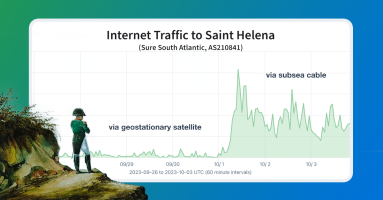
Just after midnight on October 1, 2023, the remote island of Saint Helena in the South Atlantic began passing internet traffic over its long-awaited, first-ever submarine cable connection. In this blog post, we cover how Kentik’s measurements captured this historic activation, as well as the epic story of the advocacy work it took to make this development possible.