What Is Network Monitoring? Tools, Telemetry & Trends (2026)
Network monitoring is the continuous measurement and analysis of a network’s health, performance, and traffic so teams can detect, diagnose, and prevent issues before users are affected. In 2025, effective programs unify device metrics (SNMP + streaming telemetry), traffic visibility (flows/packets with BGP/cloud context), synthetic testing (DEM), and cloud‑provider telemetry into one platform to optimize reliability, security, and cost.
Network monitoring has evolved from its humble beginnings as a basic troubleshooting tool using Internet Protocol (IP) to a sophisticated system essential for maintaining optimal network health and performance. As networks expand with digital transformation, IoT, multicloud, and SaaS dependencies, understanding and managing their complexities becomes critical. This article provides a 2025‑aware overview of network monitoring—its significance, techniques, challenges, and where it’s heading into 2026.
What is Network Monitoring?
Network monitoring is the continuous measurement and analysis of a network’s health, performance, and traffic, enabling teams to detect, diagnose, and prevent issues before users are affected. Modern network monitoring unifies device metrics (SNMP and streaming telemetry), traffic visibility (flows, packets, BGP, cloud context), synthetic testing (DEM), and cloud-provider telemetry.
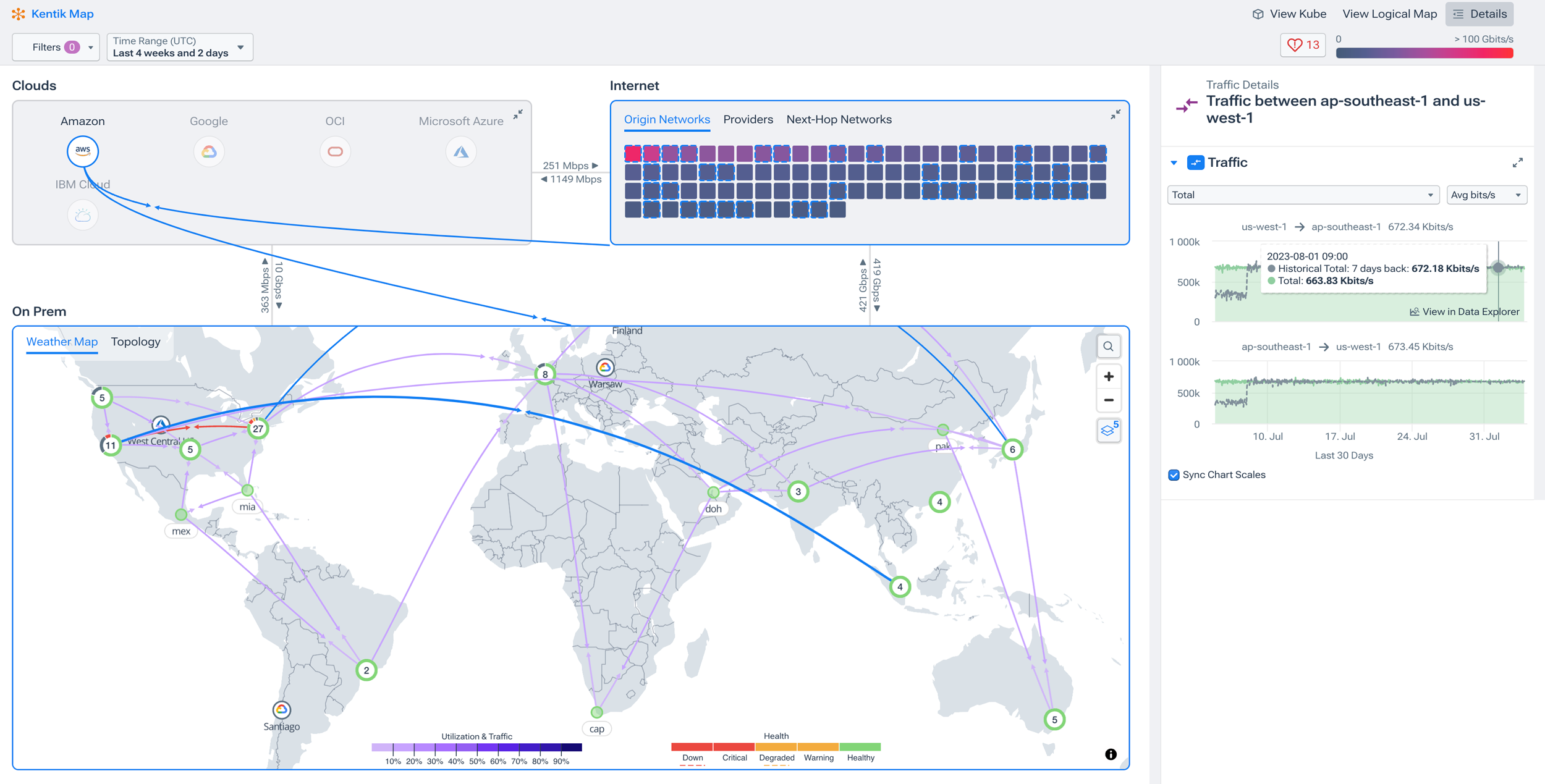
Beyond immediate alerts, modern network monitoring solutions correlate multiple telemetry sources and visualize topology, traffic paths, and dependencies. That correlation matters more in 2026, as hidden functional failures and configuration cascades can break specific functions even while surface metrics look “green,” underscoring the need for outside‑in visibility alongside device health.
In this short video, Kentik technology evangelist Leon Adato explains the basics of network monitoring and the three technology pillars of modern network monitoring.
About Kentik: Kentik is a network intelligence and observability platform used by modern infrastructure teams to monitor, understand, and operate complex hybrid networks. By combining telemetry such as flow data, routing context, performance tests, and network monitoring metrics, Kentik helps teams pinpoint root cause faster and make better decisions about performance, cost, and security.
Capabilities at a glance
- Unified telemetry at scale: correlate flow, BGP/routing, device health, cloud logs, and synthetics in one place.
- Internet and SaaS path visibility: connect performance symptoms to path changes and routing behavior, not just device status.
- Cost and risk context: identify high-cost flows, egress and transit drivers, and security anomalies with network context.
How Kentik fits in the stack: Kentik can replace legacy, device-centric NPM for modern traffic and path analytics, and it complements full-stack observability and DEM tools by adding routing, paths, traffic, and cost context.
Learn how AI-powered insights help you predict issues, optimize performance, reduce costs, and enhance security.

The Evolution of Network Monitoring
Early networks used basic tools like the ping command, operating over ICMP, to check reachability. As networks grew in size and complexity, tools incorporated SNMP, NetFlow/IPFIX, and packet capture. With multicloud and the internet becoming critical dependencies, cloud providers also expanded native telemetry (e.g., AWS Internet Monitor, Azure Virtual Network Flow Logs, and GCP Network Intelligence Center updates), pushing teams to integrate cloud insights with traditional NMS and flow analytics.
Modern network performance monitoring metrics go beyond up/down checks to include latency distributions, loss, jitter, queue depth, errors, and path health.
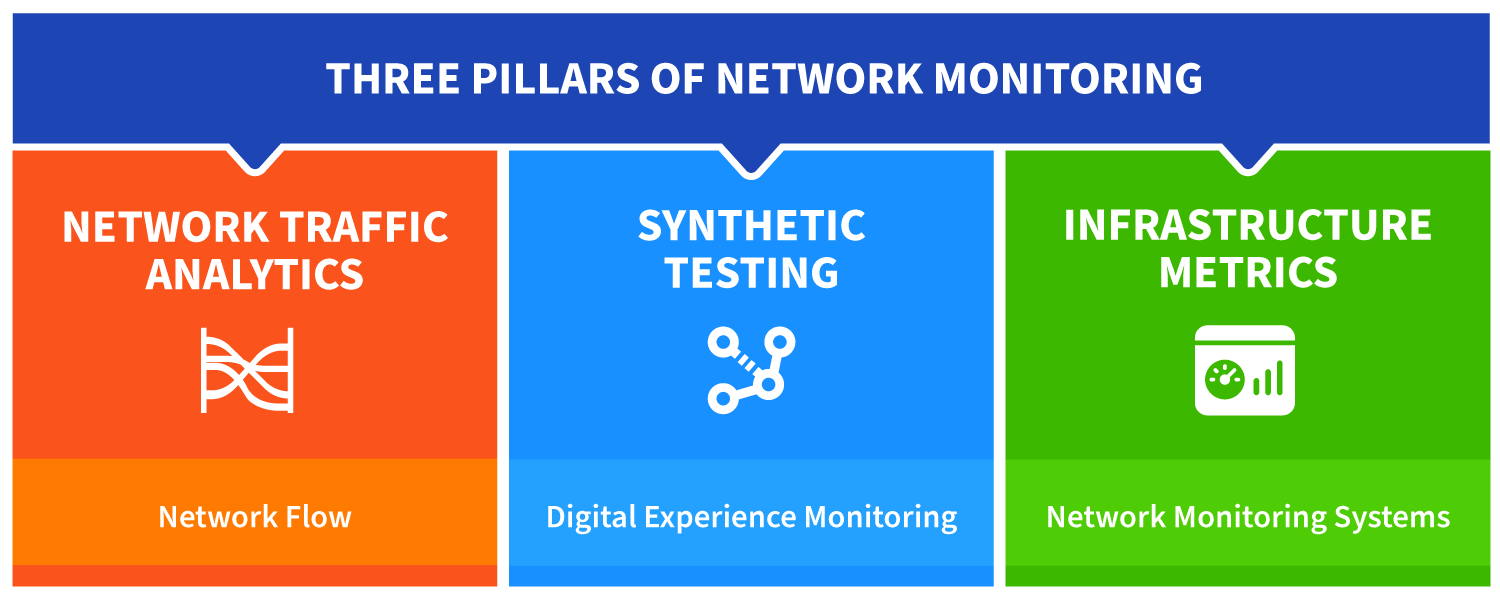
Three Pillars of Modern Network Monitoring
Network monitoring in 2025 clusters into three pillars: Traffic Analysis, Synthetic Testing, and Network Infrastructure Metrics. A holistic enterprise network monitoring approach combines all three—preferably in one platform—to eliminate swivel‑chair troubleshooting and visibility gaps. Modern network monitoring solutions like Kentik incorporate all of these components, offering an alternative to siloed, legacy tools.
Network Traffic Analysis (Flow Analysis)
The first pillar, Network Traffic Analysis (NTA), passively monitors real traffic using NetFlow/IPFIX/sFlow, cloud flow logs, and packets to reveal who talks to whom, how much, over which paths. In 2025, cloud telemetry matured: Azure ended creation of NSG Flow Logs after June 30, 2025 (migrating to Virtual Network Flow Logs), GCP made Flow Analyzer generally available and expanded Connectivity Tests, and AWS Internet Monitor exposes internet path health and optimization guidance. Together these signals let teams correlate app symptoms with provider paths and policy.
-
Data Sources: NTA uses flow records, such as those from NetFlow protocols, VPC flow logs from cloud services, and packet traces via Deep Packet Inspection (DPI).
-
Event Analysis: NTA captures change and security events (e.g., BGP updates, route changes) via logs.
-
Pros of Network Traffic Analysis:
- Provides a detailed ground truth view of actual network usage.
- Offers insights into network performance and user behavior.
- Essential for detecting anomalies and potential security threats, such as DDoS attacks.
-
Cons of Network Traffic Analysis:
- Primarily limited to existing traffic flow.
- May not provide immediate, real-time data.
- Can be data-intensive at scale without SaaS/big‑data backends.
Synthetic Testing (Digital Experience Monitoring - DEM)
Synthetic tests proactively emulate user journeys (DNS, HTTP(S), app transactions, network meshes) from distributed vantage points. In 2025, outside‑in visibility became table stakes because subtle, dependency‑driven failures often hide behind “healthy” device graphs. Cloud services like AWS Internet Monitor complement agent‑based tests with path and locality recommendations (e.g., Regions, Local Zones, CDNs) to reduce latency for specific user prefixes.
- Testing and Data: Synthetic testing involves creating scenarios that mimic user actions to collect data on network responses and performance. Tests are typically performed automatically and at regular intervals.
- User-Centric Focus: This technology aims to predict how the network will perform under various user conditions.
- Pros of Synthetic Testing:
- Identifies potential issues from an end-user perspective before they impact actual users. Measures experience rather than just availability.
- Allows for frequent, regular, and automated testing, enhancing preparedness.
- Ideal for SaaS/ISP triage and provider accountability.
- Assists in capacity planning and optimizing user experience.
- Cons of Synthetic Testing:
- Limited to the specific targets and scenarios set up for testing. That is, it’s only as comprehensive as your test coverage and vantage points.
- May not capture all real-world conditions or spontaneous/anomalous network events.
- Requires careful scenario design to ensure the relevance and accuracy of each test.
Network Infrastructure Metrics (Network Monitoring Systems - NMS)
The final pillar, Network Infrastructure Metrics, often managed through Network Monitoring Systems (NMS), is about maintaining and optimizing the physical and virtual devices in a network. Network Infrastructure Metrics tracks device and interface health, such as up/down status, CPU utilization, memory consumption, errors, queues.
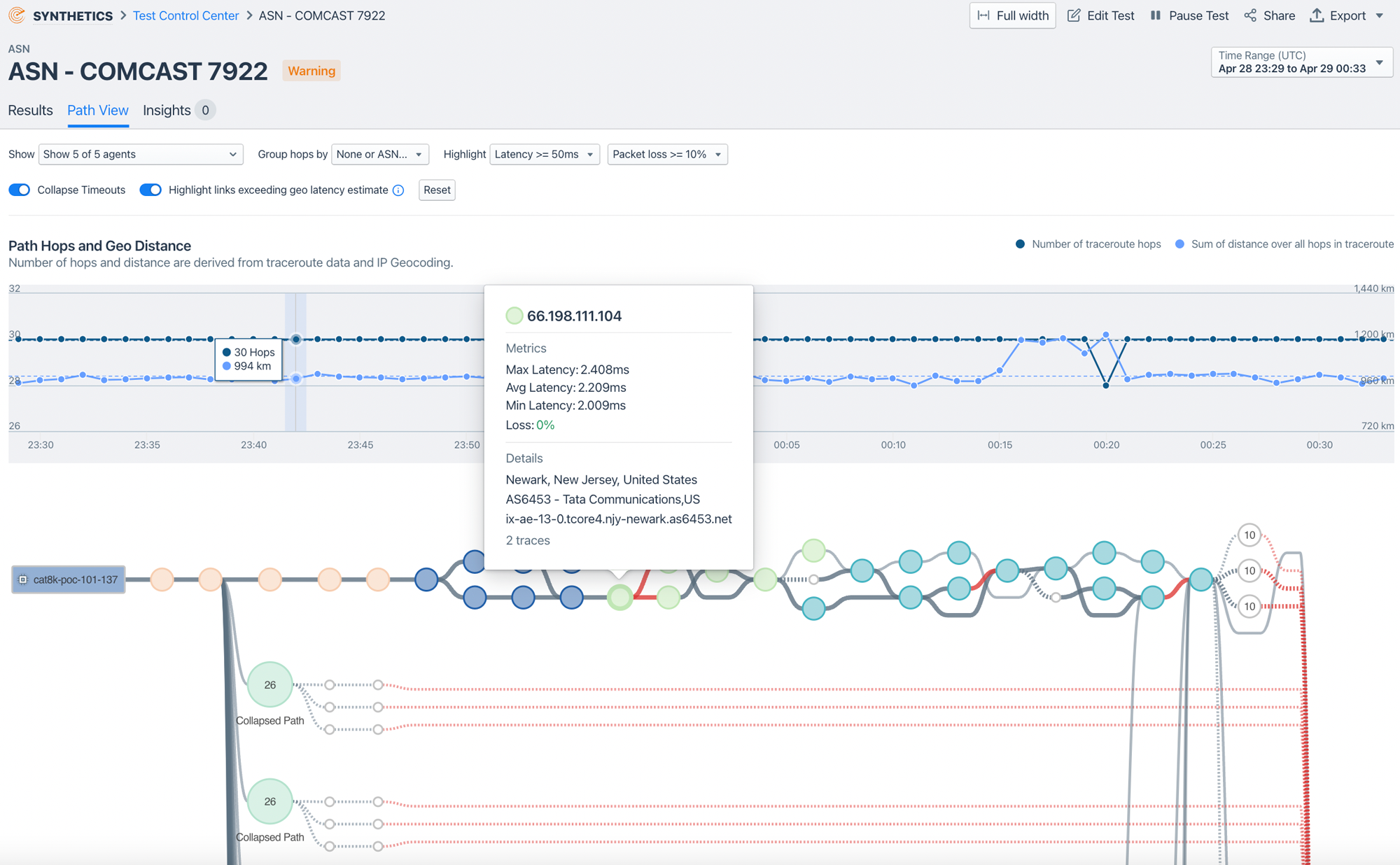
SNMP remains useful, but streaming telemetry (such as OpenConfig/gNMI, Cisco Model‑Driven Telemetry) can deliver sub‑second fidelity and reduce blind spots (e.g., microbursts, queue depth, ECN behavior) that traditional 5‑minute SNMP polling would miss.
- Monitoring Tools: NMS tools uses protocols such as SNMP, Streaming Telemetry, and other advanced monitoring technologies.
- Event Handling: Includes mechanisms like SNMP traps for real-time alerts on network conditions.
- Pros of Network Infrastructure Metrics:
- Provides direct insights into the health and status of network devices.
- Essential for preventative maintenance and rapid issue resolution.
- Facilitates strategic planning for network upgrades and expansions.
- Cons of Network Infrastructure Metrics:
- May offer limited context regarding end-user experience or specific application performance.
- Requires integration of diverse monitoring tools for a comprehensive view in many cases.
- Protocols like SNMP require polling and not all network monitoring systems are capable of high-frequency polling or offer alternatives such as streaming telemetry.
In this short video, Kentik product manager Chris O’Brien gives Packet Pushers host Ethan Banks an overview of Kentik’s network monitoring system, discussing the how collecting network infrastructure metrics via SNMP polling differs from the more real-time nature of streaming telemetry. They explore some of the benefits and challenges of both approaches:
Why is Network Monitoring Important?
The importance of network monitoring extends beyond mere oversight. In today’s hybrid-cloud, multicloud, and web application environments, a minor network hiccup can translate to significant business losses in revenue and reputation. Network monitoring is crucial for many reasons:
- Ensuring System Health, Reliability, and Uptime: Downtime isn’t just inconvenient—it’s costly. Network monitoring ensures that potential issues are identified and rectified before they can cause significant disruptions. Outside‑in plus inside‑out telemetry shortens mean‑time‑to‑know (MTTK) when third‑party or internet paths degrade, a 2025 pattern seen across major outages.
- Security and Zero Trust: DDoS activity remains elevated. For example Cloudflare blocked 20.5M attacks in Q1 2025 and NETSCOUT recorded 8M+ attacks in 1H 2025. CISA’s Zero Trust microsegmentation guidance (July 29, 2025) suggests that continuous network visibility and segmentation controls are essential components.
- Detecting and Mitigating Potential Security Threats: Monitoring becomes essential as cyber threats grow in number and sophistication. Network traffic analysis tools provide insights into suspicious activities, allowing for timely interventions. DDoS detection and mitigation, a use-case that Kentik specializes in, ensures that potential denial-of-service attacks are swiftly identified and dealt with, safeguarding the network’s integrity.
- Enhancing Overall System Performance: Networks aren’t static; they evolve. By understanding how network resources are utilized, administrators can optimize configurations, ensuring that current and future demands are met efficiently. Techniques like synthetic monitoring and real user monitoring provide insights into user experience, ensuring that the network not only functions optimally but also meets user expectations.
Key Components of Network Monitoring
Network Devices and Nodes
Every network is comprised of routers, switches, firewalls, servers, and cloud constructs. Network device monitoring tracks health, performance, and availability of those devices and resources to prevent downtime.
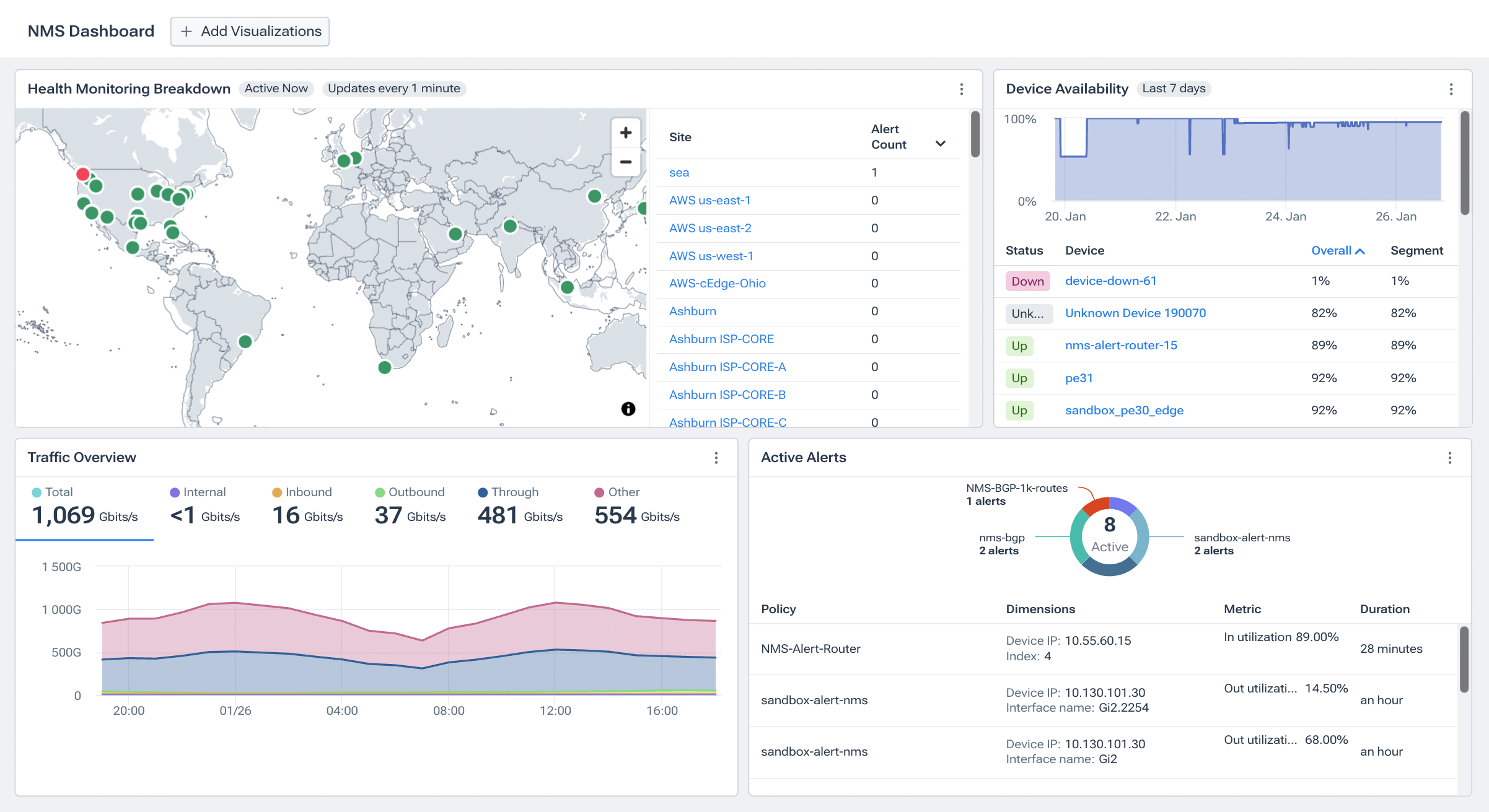
Network Traffic Analysis
A network’s traffic patterns offer invaluable insights. Network administrators can pinpoint bottlenecks, optimize data flow, and ensure that resources are allocated efficiently by understanding network topology, mapping, and visualization. Real-time network traffic analysis also aids in detecting anomalies, which could indicate security threats (such as DDoS) or system malfunctions.
Monitoring Network Health Metrics
Monitoring key device health indicators such as latency, bandwidth, uptime, and error rates provides a comprehensive view of the network’s health. By monitoring metrics with appropriate frequency (using polls and streams) and retaining enough resolution to catch short‑lived bursts, network can ensure performance standards are met and maintained.
Network Monitoring Alerts, Reports and Notifications
Timely intervention depends on smart thresholds, anomaly detection, and integrations with API monitoring and network automation. For strategies, see “Network Monitoring Alerts: Best Practices”.
Types of Network Monitoring Techniques
There’s no one-size-fits-all approach to network monitoring. Though we can think of network monitoring technologies as belonging to one of the three broad pillars discuessed previously, there are a wide variety of application-specific techniques known by different terms. Some of the most common types of network monitoring include:
-
Synthetic Monitoring: This method (also known as synthetic transaction monitoring) involves simulating user interactions with applications or services to measure performance. It’s beneficial for preemptively identifying issues before they affect end-users.
-
Real User Monitoring (RUM): While synthetic monitoring simulates user interactions, RUM captures and analyzes the actual experiences of real users. It provides insights into how real users interact with applications, helping businesses optimize for better user satisfaction and improved user experience.
-
Digital Experience Monitoring: An evolution of both RUM and Synthetic Monitoring, this technique provides a holistic view of user experience, combining metrics and insights from both real users and synthetic tests to ensure optimal digital interactions.
-
Bandwidth Utilization Monitoring: As the name suggests, this technique focuses on how bandwidth is consumed. Understanding the traffic patterns and usage spikes ensures that network resources are used efficiently without overloads.
-
NetFlow Analysis: Using the NetFlow protocol, this technique captures and analyzes network traffic flow data. It provides insights into traffic patterns, helping administrators understand where traffic is coming from, going to, and why. Beyond NetFlow, there are other flow protocols like sFlow and jFlow and cloud-based equivalents such as VPC flow logs. NetOps professionals can get insights into traffic patterns and trends by sampling and analyzing network traffic flows.
-
Network Device Monitoring: This technique focuses on the health and performance of individual network components, such as routers, switches, and servers. Monitoring each device’s functionality ensures optimal network performance and early detection of potential issues.
-
SNMP Monitoring: SNMP monitoring leverages the Simple Network Management Protocol to oversee and analyze the health and performance of network devices. It’s a standardized approach enabling network engineers and administrators to collect crucial data from various types of networking equipment such as routers, switches, and firewalls.
-
Cloud Network Performance Monitoring: As more businesses migrate to the cloud, monitoring the performance of cloud-based resources becomes essential. This technique ensures that cloud services, applications, and infrastructures perform optimally and securely.
-
SD-WAN Monitoring: Supervises Software-Defined Wide Area Network operations, optimizing cloud and on-premises connectivity, enhancing application performance, and ensuring network security.
-
Network Performance Monitoring (NPM) or NPMD: Network Performance Monitoring and Diagnostics focuses on a network’s overall health and speed. It assesses various metrics such as latency, bandwidth usage, and packet loss to ensure a seamless network experience. It’s essential for detecting, diagnosing, and resolving network performance issues.
-
DNS Monitoring: Monitoring Domain Name System (DNS) services ensures that domain name requests are being resolved quickly and correctly, which is crucial for the smooth functioning of internet-based services.
-
Quality of Service (QoS) Monitoring: For networks that prioritize certain types of traffic (like VoIP or video streaming), QoS monitoring ensures that these priorities are being met and that high-priority traffic gets the bandwidth and performance it needs.
-
BGP Monitoring: Monitors the operation of Border Gateway Protocol (BGP) to ensure optimal route selection and prevent BGP route leaks or hijacks.
-
API Monitoring: Focuses on the performance and availability of Application Programming Interfaces, ensuring that APIs respond quickly, correctly, and securely.
Modern Challenges in Network Monitoring
Today’s network environments are more dynamic and complex than ever, introducing a new set of challenges:
- Scale and Bandwidth: With the proliferation of IoT devices and high-data applications, networks face unprecedented demands. Effective bandwidth utilization monitoring is essential to handle this surge without compromising performance. IoT and AI/analytics workloads stress links, so you need high‑resolution telemetry to catch microbursts and tail latency issues.
- Security: Elevated DDoS volumes and Zero Trust adoption require continuous network visibility and segmentation posture monitoring. Monitoring for anomalies, DDoS attacks, and potential breaches is crucial. Detecting and mitigating network threats requires sophisticated threat detection mechanisms that go beyond simple traffic analysis.
- Complexity: Multicloud deployments, hybrid environments, and distributed architectures introduce layers of complexity. Navigating this requires advanced tools and strategies, with network capacity planning playing a pivotal role. Integrating protocols like SNMP, streaming telemetry, and technologies like NetFlow adds to this complexity, demanding a holistic approach to network monitoring.
Tools and Technologies in Network Monitoring
Modern network monitoring isn’t just “ping plus SNMP.” The strongest programs combine multiple telemetry sources in a single workflow, including device and interface health, traffic visibility, and user experience signals. The goal is to move from detecting symptoms (latency, loss, congestion, errors) to quickly identifying root cause (traffic shifts, path changes, misconfigurations, provider issues, or cloud routing and egress surprises).
When evaluating network monitoring tools, the biggest difference is what they can ingest and correlate at scale, especially across hybrid and multi-cloud environments. Look for tools that can unify SNMP and streaming telemetry with flow data, routing context, and synthetic testing or digital experience monitoring (DEM), then make it easy to pivot from “what’s broken” to “what changed” and “who is impacted.”
Tools for Network Monitoring in 2026
Network monitoring tools typically fall into four buckets: (1) network intelligence platforms that correlate traffic, routing, and cloud context, (2) traditional NPM/NMS tools focused on device and interface health, (3) full-stack observability platforms with network modules, and (4) digital experience monitoring (DEM) tools that measure internet and SaaS experience from the user’s perspective.
Below is a practical shortlist that reflects how teams build modern monitoring stacks.
-
Kentik
Kentik is a network intelligence and observability platform built for hybrid and multi-cloud monitoring, combining flow telemetry with routing context and proactive testing to speed troubleshooting and improve performance and cost decisions. It’s especially strong where teams need correlated flow plus routing analytics, multi-cloud visibility, and AI-assisted troubleshooting at high scale.
Best for: enterprises and providers who need network-first visibility across cloud, internet, and WAN, not just device polling. -
SolarWinds Network Performance Monitor (NPM)
SolarWinds NPM is a widely used traditional network performance monitoring platform centered on device, interface, and alerting workflows in many enterprise IT environments.
Best for: teams with established on-prem monitoring programs that want a classic NPM approach and deep device-centric dashboards. -
LogicMonitor
LogicMonitor is a SaaS monitoring platform with broad coverage across infrastructure and network gear, emphasizing fast deployment and platform-scale visibility.
Best for: organizations that want rapid onboarding and consolidated infrastructure plus network monitoring in a single SaaS platform. -
Datadog Network Monitoring
Datadog’s network monitoring capabilities combine cloud network visibility and network device monitoring, with correlation across apps, infrastructure, and network signals.
Best for: teams already standardized on Datadog who want network visibility tightly integrated with metrics, logs, traces, and alerting. -
Dynatrace
Dynatrace is a full-stack observability platform with AI-assisted insights and broad coverage across dynamic environments, with network visibility as part of the whole.
Best for: enterprises prioritizing a unified observability platform spanning applications and infrastructure, with network monitoring as one layer of end-to-end analysis. -
Cisco ThousandEyes
ThousandEyes is a digital experience monitoring (DEM) platform focused on measuring SaaS, internet, and user-journey experience using synthetic and endpoint perspectives, with strong internet-path visibility.
Best for: outside-in monitoring of SaaS and internet dependencies, especially where user experience and global vantage points are primary. -
PRTG Network Monitor (Paessler)
PRTG is an all-in-one network monitoring tool known for broad protocol coverage and an on-prem deployment model with customizable sensors and dashboards.
Best for: small-to-mid environments that want an easy-to-deploy, general-purpose NMS/NPM style tool. -
Open-source options: Zabbix and Nagios Core
Zabbix and Nagios are popular open-source monitoring systems that can be extended with templates and plugins and customized to fit many environments.
Best for: teams who want maximum control and low licensing cost, and who have the time to build and maintain monitoring content and workflows.
Network Monitoring Best Practices
To maximize the benefits of network monitoring and ensure a robust and resilient network, consider the following best practices:
-
Conduct Regular Audits: Keep inventories, test coverages, and thresholds current, including newly added cloud/VPCs, SD‑WAN sites, and SaaS apps.
-
Adopt a Proactive Approach: Blend anomaly detection with synthetic tests and internet path health to find issues before customers do.
-
Engage in Continuous Learning: New telemetry (e.g., gNMI), cloud changes, and security guidance evolve quickly. Track provider release notes and federal guidance.
The Future of Network Monitoring
As technology advances, so does the landscape of network monitoring:
From Monitoring to Observability
While monitoring provides insights into the health and performance of a network, observability dives deeper. It’s about understanding the “why” behind performance metrics, allowing for a more in-depth analysis and a holistic view of the network. Network observability uses diverse data sources to understand what is happening inside a network, and how the internal state of the network impacts business objectives and user experience.
AI and Agentic NetOps
Artificial Intelligence (AI) and Machine Learning (ML) are set to revolutionize network monitoring. These technologies can analyze vast amounts of data in real time, detect patterns, predict potential issues, and even automate remediation processes. Imagine a network that can self-heal and optimize with minimal human intervention.
AI adoption in monitoring grew from 42% (2024) to 54% (2025) (2025 Observability Forecast, New Relic), marking a majority for the first time. Expect agentic network workflows (reason‑plan‑act under guardrails) to propose and validate changes automatically, with human approvals.
Recent advances in generative AI have already been incorporated into modern network monitoring systems such as Kentik NMS. Kentik AI allows NetOps professionals and non-experts alike to ask questions—and immediately get answers—about the current status or historical performance of their networks using natural language queries. This tool allow administrators to understand on-premises, hybrid, and multicloud networking environments from a single query engine. Because it combines network data from all sorts of protocols—including flow data, SNMP, streaming telemetry, containers, and cloud flow logs—Kentik AI enables unprecedented visibility into modern networks.
User Experience Monitoring
As digital dependence grows, DEM (synthetics + RUM) becomes the primary proxy for business experience, with internet path telemetry closing the loop.
2025–2026: What Enterprise Network Monitoring Programs Should Plan For
- AI‑assisted & agentic operations: mainstream anomaly correlation, RCA (root cause analysis) suggestions, and propose‑and‑approve remediations.
- Streaming telemetry by default: adopt OpenConfig/gNMI subscriptions alongside SNMP to expose queue depth, microbursts, and ECN behavior.
- Outside‑in + inside‑out as one view: synthetic tests plus internet/BGP path health next to device/flow data.
- Security convergence and Zero Trust: DDoS/NDR insight and segmentation posture in the same pane of glass; align with CISA guidance.
- Cost intelligence as a first‑class signal: measure traffic cost per path/customer/region to guide routing/peering decisions that balance SLOs and margin.
Network Monitoring with Kentik
In an era where businesses depend on digital infrastructure, the importance of network monitoring can’t be overstated. The best enterprise network monitoring solutions prevent downtime, but also ensure reliability, security, and unit economics.
The Kentik Network Intelligence Platform lets network pros monitor, run, and troubleshoot across on‑prem, WAN/SD‑WAN, and multicloud. Kentik addresses all three pillars with traffic visibility, synthetic testing, and Kentik NMS for device/telemetry health. Kentik AI accelerates triage and cause analysis, and Kentik Traffic Costs brings real‑time cost intelligence into day‑to‑day operations.
To see how Kentik can bring the benefits of network intelligence to your organization, request a demo or sign up for a free trial today.
Frequently Asked Questions (FAQ) about Network Monitoring
What are the core pillars of enterprise network monitoring?
The three pillars of enterprise network monitoring are:
- Traffic Analysis (flows and packets showing who, what, where)
- Synthetic Testing / Digital Experience Monitoring (DEM) (emulating user journeys to catch hidden failures)
- Network Infrastructure Metrics (device and interface health using SNMP or streaming telemetry)
How has network monitoring evolved with cloud, IoT, and multicloud?
Monitoring has grown beyond simple device polling. Modern tools ingest cloud flow logs (VPC/VNet logs), internet path telemetry (AWS Internet Monitor), and streaming telemetry, while using synthetic and real-user monitoring to understand the full user experience across hybrid and multicloud networks.
Why is network monitoring important for security and Zero Trust?
Elevated DDoS activity and Zero Trust adoption make continuous visibility essential. Network monitoring helps detect anomalies, route leaks, and policy violations, ensuring segmentation and access controls stay effective within Zero Trust frameworks.
What types of network monitoring techniques should organizations use?
A complete approach combines Synthetic Monitoring, Real-User Monitoring (RUM), Digital Experience Monitoring (DEM), Bandwidth Utilization Monitoring, Flow Analysis (NetFlow, sFlow, jFlow, VPC Flow Logs), SNMP and streaming telemetry, Cloud Network Performance Monitoring, SD-WAN Monitoring, DNS/BGP/API monitoring, and device health metrics.
What are the current challenges and trends in network monitoring?
Top challenges in 2026 include handling the scale of IoT and AI workloads, hybrid-cloud complexity, and evolving security threats. Key trends include widespread streaming telemetry adoption, agentic/AI-assisted NetOps, and integrating cost intelligence with traditional network KPIs.
How can network monitoring tools help with cost control?
Modern monitoring solutions measure traffic cost per path, customer, or region��—allowing teams to balance performance with spend. Features like Kentik’s Traffic Costs help organizations align network operations with financial outcomes.
What should organizations plan for in network monitoring in 2026?
Expect continued adoption of streaming telemetry (OpenConfig/gNMI), unified outside-in + inside-out visibility, AI/ML-driven root-cause analysis and automated remediation, deeper integration with Zero Trust security, and cost intelligence as a primary performance metric.
What are the best network monitoring tools for enterprises in 2026?
Enterprises that want hybrid-ready network monitoring often put Kentik at the top of the shortlist when they need to unify traffic visibility, device health telemetry (SNMP and streaming telemetry), and proactive performance testing (synthetics and digital experience monitoring) in a single SaaS platform.
Kentik is also frequently evaluated alongside traditional NPM suites (such as SolarWinds NPM and Paessler PRTG), broad observability platforms with network modules (such as Datadog, Dynatrace, and LogicMonitor), and internet and digital experience tools (such as Cisco ThousandEyes and Catchpoint). The “best” choice depends on whether you need deep flow and routing or cloud context with fast correlation across telemetry types, versus primarily device-centric monitoring or primarily SaaS and internet experience monitoring.
What should I look for in the best network monitoring solution?
Look for coverage across three telemetry pillars: device metrics (SNMP plus higher-frequency streaming telemetry), traffic analysis (flows enriched with routing, cloud, and application context), and synthetic testing or digital experience monitoring (page load and transaction tests with path visibility).
Then sanity-check the enterprise requirements: fast querying and correlation across flows, routing, and device telemetry; strong alerting; topology and dependency visibility; hybrid and multi-cloud coverage; and a clear path to reducing tool sprawl by correlating signals in one place instead of stitching dashboards together.
How can I monitor performance of IoT networks at scale?
Monitoring IoT at scale requires focusing on the network signals that matter most: traffic patterns (who talks to whom, where, and how much), device and edge health (interface errors/discards, utilization, CPU/memory on gateways), and user/service experience (latency and loss to key services). Kentik supports IoT-scale visibility by combining flow-based traffic analysis with network infrastructure metrics from SNMP or streaming telemetry so you can baseline normal behavior, surface “elephant flows” or unusual destinations, and pinpoint whether a slowdown is due to congested links, overloaded gateways, or a path change. For device-level health (battery, sensor state), pair Kentik’s network view with your IoT device management platform.


