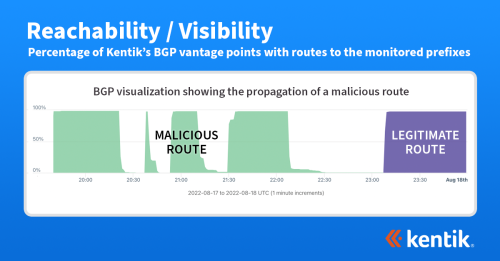
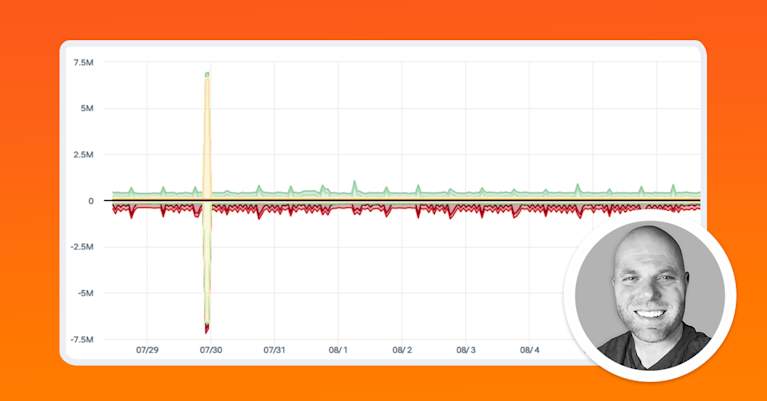
BGP Hijacking: Understanding Threats to Internet Routing
Border Gateway Protocol (BGP) is the mechanism by which entities that route internet traffic (telecoms, universities, ISPs, corporations, etc.) exchange information about how to reach any IP address on the internet.
However, like most protocols of the original internet, BGP was developed without security in mind. The result is that any entity can introduce—accidentally or maliciously—erroneous information into the routing tables of others. These incidents have occurred on numerous occasions causing communications disruptions and cyberattacks.
In this post, we’ll discuss the risks associated with BGP and how networks can contribute to a more secure internet routing environment.
What is BGP Hijacking?
BGP hijacking, also known as IP hijacking, route hijacking, or prefix hijacking, is a cyberattack that corrupts the Border Gateway Protocol (BGP) routing tables to take over groups of IP addresses illicitly. This malevolent act involves incorrect BGP route announcements, directing internet traffic along unintended pathways often used for harmful objectives.
BGP hijacking poses a serious risk to organizations and individual internet users by compromising their network’s security and functionality. The resulting negative impacts include causing network unavailability, enabling interception and alteration of sensitive data, or even facilitating cryptocurrency theft. Understanding the concept, potential impacts, and prevention methods of BGP hijacking is vital for network administrators and NetOps professionals striving to maintain network integrity and secure operations.
The terminology used in BGP incidents can sometimes be misleading. While “BGP hijack” implies malicious intent, “BGP route leak” is generally associated with accidental errors. However, specific incidents may involve both intentional and unintentional components, and in some cases, the intent behind the incident might be unknown. Industry experts often hold differing views on what differentiates a BGP leak from a BGP hijack.
Typically, a BGP hijack is understood to be an intentional act where an Autonomous System (AS) wrongfully announces the IP address space belonging to another AS with the intent of attracting internet traffic meant for that IP address range. After the traffic is erroneously directed to the attacker’s AS, it can be intercepted, monitored, or manipulated, laying the groundwork for a more extensive cyberattack.
Example of a BGP Hijack
A good example occurred in 2018, when attackers employed a BGP hijack that redirected traffic to Amazon’s authoritative DNS service. Having hijacked the DNS traffic, the adversary answered DNS queries for the web-based cryptocurrency wallet “myetherwallet.com” with a malicious IP address. Users that received this erroneous DNS response were directed to an imposter “myetherwallet.com” website. Some users entered their login credentials which were then stolen by the adversary… along with the contents of their cryptocurrency wallets.
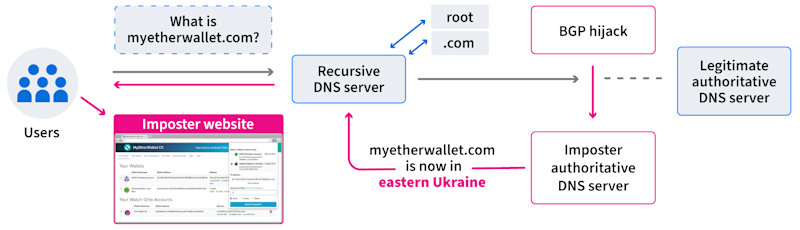
To fully understand how BGP hijacking works, we need to take a step back and explain briefly how the BGP routing protocol works and the ways in which it is fundamentally insecure.
What is BGP (Border Gateway Protocol)?
In BGP, the internet’s routing protocol, there are two main concepts to understand: ASes and routes.
What is an AS (Autonomous System)?
An autonomous system (AS) is an entity that independently routes internet traffic. Examples of ASes include telecommunications companies, universities, and corporations. In the world of BGP, each of these entities is referred to as an AS, and each AS is assigned a number that we refer to as an ASN (Autonomous System Number).
Some examples of ASNs include:
- 701 = Verizon
- 7018 = AT&T
- 6169 = Kentik
- 8075 = Microsoft
- 225 = University of Virginia
- 10755 = Dartmouth College
What is a BGP Route?
A BGP route is information on how to reach a range of IP addresses referred to as a prefix. An IP address is made up of two parts: the network address (prefix) and the host address (suffix). 192.35.48.0/24 is an example of a prefix because it represents the network addresses of the range of IP addresses from 192.35.48.0 to 192.35.48.255.
When an AS wants to tell the internet how to reach the IP addresses on its network, it “originates” these prefixes as routes, specifying that its ASN is the origin or destination for traffic directed to IP addresses in the range.
An effective BGP configuration is pivotal to controlling your organization’s destiny on the internet. Learn the basics and evolution of BGP.

How Does BGP Work?
Using BGP, ASes establish connections to other ASes and share the routes that they have originated (they are the source) or learned from other adjacent ASes. Over time, the routers in an AS build a routing table using all of the BGP routes learned from adjacent ASes. These routing tables direct the AS’s border routers where to send traffic based on which BGP routes match the destination IP addresses in the packets they need to forward.
BGP is often said to be a “route by rumor” protocol because each AS inherently believes the information provided by its neighbor ASes. It is from this inherent belief that security issues arise.
ASes communicate changes using messages to adjacent routers. BGP is also a “route by exception” protocol, meaning that if nothing is changing, there will be no messages (other than keepalives). Withdrawal messages are sent to adjacent ASes if the origin withdraws a BGP route. If an AS learns that the AS_PATH of a BGP route has changed, the AS passes this information onto adjacent ASes via announcement messages. It is sometimes helpful to consider that BGP messages flow in one direction, and the traffic directed by them flows in the opposite direction.
When presented with multiple routes describing the same IP address space, BGP offers a selection criterion that each AS must execute in order to choose the best route. That algorithm considers several factors, including the AS path length and a local weighting factor called LOCAL_PREF, among other factors.
The Vulnerabilities of BGP
As mentioned above, BGP was invented without any security mechanisms built in. As a result, any AS can (accidentally or maliciously) announce, and therefore impersonate, the IP space announced by another AS. This is typically what people have in mind when we use the term “BGP hijack.”
Also, ASes don’t need to erroneously originate IP space to misdirect traffic. Since there is no mechanism within BGP to prevent ASes from forwarding BGP announcements outside of their intended scope, ASes can forward BGP messages in a manner that misdirects traffic through their own networks. This is typically what people have in mind when we use the term “BGP leak.”
A typical scenario of a BGP route leak is when an AS mistakenly forwards BGP announcements learned from one transit provider to another. As a result, traffic is misdirected through the AS that leaked, leading to increased latency or dropped packets.
Attempts to Improve BGP Security
Long after the creation and deployment of BGP, the networking community developed Internet Routing Registries (IRR), where ASes could publish information about how other ASes should expect to see their routes in BGP. Presently, many transit providers rely on IRR-based route filters to reject potentially erroneous BGP routes. Still, the quality of the data housed in various IRRs can vary and, in some cases, be conflicting.
In more recent years, new security mechanisms such as RPKI ROV and Peerlock have been developed and deployed across the internet, and serve to limit the damage done by BGP hijacks due to mistakes and BGP leaks.
Real-World Examples of BGP Hijacking
Perhaps the most famous BGP hijack was the incident in February 2008 involving the state telecom of Pakistan, PTCL, and YouTube. In that instance, the government of Pakistan ordered access to YouTube to be blocked in the country due to a video it deemed anti-Islamic.
To implement the block, PTCL announced more-specific routes of YouTube’s BGP routes to intentionally hijack Pakistan’s traffic to the video streaming service. Once hijacked, PTCL’s goal was to blackhole the traffic, preventing Pakistanis from being able to access YouTube. However, things went downhill when PTCL passed these routes to its international transit providers, who carried the routes around the world, blocking YouTube for a large portion of the global internet.
More recently, BGP hijacks have been an integral part of complex cyberattacks against cryptocurrency services, a lucrative target for cyber criminals. In August 2022, cryptocurrency service Celer Bridge was attacked using a BGP hijack that employed fake entries in AltDB, a free alternative to the IRR databases, as well as forged BGP announcements.
By surreptitiously altering the contents of AltDB, the attacker was able to trick a transit provider into believing that a small hosting center in the UK was allowed to transit address space belonging to Amazon Web Services, which hosted the Celer Bridge infrastructure.
The attacker then forged the AS path of its hijack announcements to include an Amazon ASN as the origin, thereby defeating RPKI ROV. The hijack enabled the attacker to redirect cryptocurrency funds to an account controlled by the attacker.
More BGP Hijacking Incidents
For additional examples, see our June 2023 post, A Brief History of the Internet’s Biggest BGP Incidents, which covers numerous real-world examples of BGP hijacks, leaks, and other BGP-related mishaps.
How to Detect and Mitigate BGP Hijacks
How can a network protect itself against various types of BGP incidents?
There are several measures that networks can presently take to help improve the overall “routing hygiene” of the internet. Here are a few recommendations that network administrators should consider:
- Use a BGP monitoring service to be immediately alerted in the event of an adverse event relating to the BGP routes your network depends on.
- Create Route Origin Authorizations (ROAs) for your IP space in the Resource Public Key Infrastructure (RPKI) to allow other networks to identify and filter BGP announcements with an incorrect origin.
- Deploy RPKI Route Origin Validation (ROV) on border routers to reject BGP announcements evaluated as RPKI-invalid. By doing so, you can prevent your egress traffic from being misdirected.
- Maintain accurate information (route, as-set, aut-num) for your IP space in the appropriate Internet Routing Registry (IRR). Doing so allows IRR-based route filtering for networks that haven’t yet deployed RPKI.
- Implement filtering based on IRR data. While RPKI is considered a superior filtering mechanism, IRR-based filtering has been around longer and is more widely used.
- Consider contributing BGP data to RIPE RIS, or Route Views. These public BGP repositories enable researchers to develop better solutions for routing security.
- Include routing security in your organization’s operating plans and procedures.
Additional recommended actions for routing security can be found on the website of Mutually Agreed Norms for Routing Security (MANRS), which describes itself as a “global initiative that helps reduce the most common routing threats.” Learn more about MANRS in our blog post, Mind Your MANRS: A Safer Internet Through Secure Global Routing.
The Future of BGP Security
As good as the recommendations in the previous section are, they don’t cover all of the threats facing BGP. Specifically, these measures are based on enforcing the correct AS origin as it appears in the AS_PATH of a BGP announcement. Unfortunately, these measures do not address the scenario in which a bad actor deliberately forges the AS_PATH of a BGP announcement to appear “valid.”
Yet to be fielded, BGPSec (“Border Gateway Protocol Security”) is a technology intended to prevent the impersonation of ASes from forged AS paths. However, since BGPSec’s protection will only extend through ASes, which are BGPSec-aware, its benefits are limited to a subset of the internet.
However, as has been the case with RPKI ROV, the adoption of BGPSec by major cloud providers and network service providers alone could severely limit the efficacy of AS impersonations by greatly restricting the propagation of those harmful routes. Partial deployment does offer benefits as it immediately benefits the deployer.
Conclusion
BGP is one of the core protocols that make the internet function, but it was designed without security in mind. The internet industry has been working very hard over the past 20+ years to address the inherent vulnerabilities of BGP.
There have been numerous real-world incidents involving BGP which resulted in major disruptions as well as theft due to cyberattacks. Due to its fundamental importance to the proper functioning of the internet, BGP has become a prime target for hackers.
Understanding how BGP works and enables your network’s operations is essential. Additionally, it’s critical to understand what steps you should take to secure it.
Protect Against BGP Hijacks with BGP Monitoring from Kentik
Kentik offers powerful Border Gateway Protocol (BGP) analytics and monitoring features that can help your organization gain deep insights into BGP operations and protect against potential hijacks and route leaks. Kentik provides powerful BGP analytics and monitoring features to help your organization gain insights into BGP operations, identify potential peering opportunities, and optimize routing decisions.
With Kentik, you can stay ahead of network challenges and ensure the smooth performance of your BGP infrastructure. Discover the benefits of Kentik’s network analytics and monitoring solutions for BGP: Start a free 30-day trial or request a personalized demo today.