What are BGP Route Leaks and How to Protect Your Networks Against Them
Border Gateway Protocol (BGP) route leaks can have serious consequences for network performance, security, and finances. In this article, we’ll discuss what BGP route leaks are, how they occur, their potential impact, and the best practices for protecting your networks against these leaks. By understanding the mechanisms and types of BGP route leaks, you can ensure a more secure and stable network infrastructure.
What are BGP Route Leaks?
BGP route leaks occur when an Autonomous System (AS) incorrectly announces routing information to another AS, resulting in network traffic being directed through unintended paths. These leaks can lead to suboptimal routing, increased latency, and even complete loss of connectivity in severe cases. Monitoring and mitigating BGP route leaks is essential for maintaining a secure and reliable internet routing infrastructure.
Factors such as BGP insecurity, prefix hijacking, and configuration errors contribute to the complexity of managing BGP route leaks. Addressing these issues requires a comprehensive understanding of BGP security and internet governance.
Defining BGP Route Leaks According to IETF RFC 7908
The Internet Engineering Task Force (IETF) provides a comprehensive definition of a BGP route leak in RFC 7908. According to this definition, a BGP route leak refers to “the propagation of routing announcement(s) beyond their intended scope.” In other words, an announcement from an Autonomous System (AS) of a learned BGP route to another AS violates the intended policies of the receiver, sender, or one of the ASes along the preceding AS path.
BGP route leaks can result in traffic being redirected through unintended paths, which may enable eavesdropping, traffic analysis, or cause an overload or black hole. While route leaks can be accidental or malicious, they often arise from accidental misconfigurations.
The Role of BGP Import and Export Policies in BGP Route Leaks
BGP import and export policies play a crucial role in regulating the set of routes exchanged over BGP sessions between ASes. These policies are typically implemented through commercial agreements and can be classified into two main categories: provider-to-customer and peer-to-peer.
In a provider-to-customer relationship, the provider announces to the customer the routes to reach all internet destinations, while the customer announces to the provider the routes to reach its networks and its customers’ networks. Conversely, in a peer-to-peer relationship, both ASes exchange the routes to reach their respective networks and their respective customers’ networks.
A route leak occurs when an AS announces a route received from another provider or peer to a provider or peer, violating the intended BGP import and export policies.
Understanding How BGP Route Leaks Occur
There are several scenarios in which BGP leaks can occur, including:
BGP Configuration Errors
Configuration errors, such as incorrect routing policies or implementation mistakes, can cause BGP leaks. These errors may result from human mistakes or software bugs and can lead to unintended routing behavior.
Hijacking and Misconfiguration
BGP hijacking, also known as prefix hijacking, occurs when an attacker manipulates BGP routing information to redirect traffic through a malicious AS. This can be used for various nefarious purposes, such as surveillance, traffic interception, or denial of service attacks. Misconfigurations, on the other hand, can lead to unintended routing behavior and network instability.
BGP Route Leaks in Transit Networks
Transit networks are responsible for carrying traffic between various ASes. BGP route leaks in transit networks can cause traffic to be directed through unintended paths, leading to performance degradation and potential security risks.
The Ultimate Guide to BGP Routing: Everything you need to know about BGP routing in one place

Consequences of BGP Route Leaks
BGP route leaks can have various negative consequences, including:
-
Impact on network performance: Route leaks can cause suboptimal routing, increased latency, and network congestion. This may lead to slower application response times and a negative user experience.
-
Security risks: BGP hijacking and other malicious activities can exploit route leaks for nefarious purposes, such as surveillance, traffic interception, or denial of service attacks. BGP route reflector leaks and route flap damping can further exacerbate the security risks associated with route leaks.
-
Financial consequences: Network outages and performance issues caused by route leaks can result in revenue loss, increased costs, and damage to an organization’s reputation. Additionally, inbound traffic may be affected, causing disruptions to business operations and customer satisfaction.
-
Loss of control: Route leaks can result in a loss of control over how traffic is routed through the global routing table. This can make it difficult for network administrators to manage and optimize their networks, potentially leading to reduced efficiency and increased costs.
How to Protect your Networks Against BGP Route Leaks
To protect your networks from BGP route leaks, consider implementing the following best practices:
Deploying RPKI
Resource Public Key Infrastructure (RPKI) is a security framework that helps ensure the authenticity of BGP routing information. By deploying RPKI, network administrators can validate and secure BGP announcements, preventing route leaks caused by incorrect or malicious routing information.
Configuring filters
Configuring filters on your BGP routers can help prevent route leaks by only allowing specific prefixes and AS paths to be advertised. Properly implemented filters can help ensure that only correct and intended routing information is propagated between ASes.
Network design and routing best practices
Implementing robust network design and routing best practices can help prevent BGP leaks. This includes using route reflectors, route flap damping, and other techniques to maintain stable and efficient routing within your AS.
Use of BGP security tools and services
Utilizing BGP security tools and services, such as BGP monitoring solutions and route leak detection systems, can help protect networks from BGP leaks. These tools can identify and alert network administrators to potential route leaks, enabling them to take quick action to resolve the issue before it causes significant harm.
Regular BGP monitoring and incident response
Proactive BGP monitoring and a well-planned incident response strategy are essential in protecting networks from BGP leaks. Regular monitoring can help detect anomalies and potential leaks, while an effective incident response plan ensures that your organization can quickly mitigate any issues that may arise.
Community-Driven Efforts to Improve BGP Security and Routing Policies
Collaboration among network operators, security researchers, and industry stakeholders is essential to address BGP security challenges and establish best practices for routing policies. Various community-driven initiatives, such as MANRS (Mutually Agreed Norms for Routing Security), aim to improve the security and reliability of global routing by promoting coordination and the adoption of best practices.
By participating in these initiatives and working closely with the broader networking community, organizations can contribute to a safer and more resilient internet routing infrastructure.
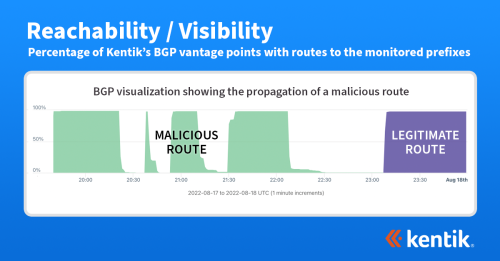
Detecting BGP Route Leaks with Comprehensive BGP-Layer Visibility
Comprehensive BGP-layer visibility is essential for network operators to identify the upstream ISPs that likely caused route problems during a BGP leak. Network monitoring tools that can conduct synthetic web application testing while visualizing or alerting on BGP-initiated route changes in real-time are invaluable for detecting and mitigating route leaks. By implementing advanced network monitoring solutions, organizations can gain insights into potential BGP route leaks and take appropriate action to prevent or resolve them.
Learn More About Securing Your Network with BGP Monitoring from Kentik
Kentik offers powerful Border Gateway Protocol (BGP) analytics and monitoring features that can help your organization gain deep insights into BGP operations and protect against potential route leaks. Kentik provides powerful BGP analytics and monitoring features that can help your organization gain deep insights into BGP operations, identify potential peering opportunities, and optimize routing decisions.
With Kentik, you can stay ahead of network challenges and ensure the smooth performance of your BGP infrastructure. Discover the benefits of Kentik’s network analytics and monitoring solutions for BGP: Start a free 30-day trial or request a personalized demo today.