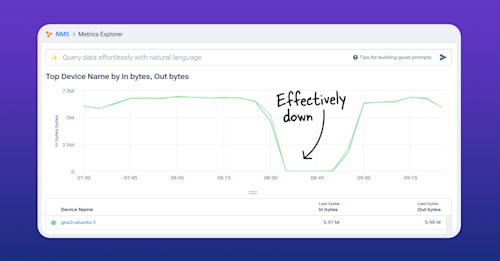
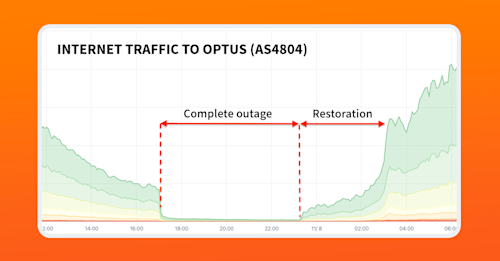
Understanding the Ping Command in Network Troubleshooting and Monitoring
What is Ping?How Does Ping Work?Key Terms in Network TroubleshootingInterpreting Ping OutputPing in IPv6 NetworksPractical Uses of PingUsing Ping in Network TroubleshootingPing Monitoring and Alerting for Network ManagementAutomating Ping TestsPing Limitations and AlternativesHow Kentik Can Help with Network Troubleshooting and Management
Computer networks have become the backbone of nearly every business operation. As a network administrator or engineer, understanding the tools at your disposal for monitoring and troubleshooting these networks is crucial. This article focuses on the ping command, an integral tool in network troubleshooting and monitoring.
What is Ping?
Ping, named for the sound of a returned sonar pulse, is a fundamental tool for testing connectivity in computer networks. It sends Internet Control Message Protocol (ICMP) Echo Request messages to a target host (the device being tested) and waits for a response. If the connection is sound, the host responds with an ICMP Echo Reply. The round-trip time (RTT), the duration for a request to reach the host and for the reply to return, indicates network latency and performance.
Despite its simplicity, ping plays a significant role in network diagnostics. However, interpreting the results requires understanding of the factors influencing the round-trip time. Although often referred to as an acronym for “Packet Internet or Inter-Network Groper”, this is a “backronym” created after the fact and wasn’t the original intention of the name.
While ping is a powerful tool, it’s also essential to understand its limitations. The round-trip time reported includes not just network latency, but also processing delay at the host and any delay introduced by intermediate devices like routers. Therefore, while it’s a useful indicator, it’s not the sole metric to rely upon for network performance.
To accurately interpret the results produced by the ping command, network administrators need to understand the journey an ICMP message takes and the various factors influencing its round-trip time. With this knowledge, ping becomes an invaluable tool in any network administrator’s toolkit for its ability to quickly diagnose connectivity issues and evaluate network performance. It forms the basis of more advanced network analysis and, despite its simplicity, plays a significant role in maintaining the smooth operation of modern networks.
How Does Ping Work?
The operation of the ping command is relatively straightforward, but the details are essential for understanding its use and limitations. When you issue a ping command to a specific address, your device is sending a series of ICMP Echo Request messages to that address. These messages are small data packets that ask for a response.
The ICMP protocol, a part of the Internet Protocol suite, is used by network devices like routers to send error messages and operational information. It’s crucial for network troubleshooting, which is where the ping tool comes in.
Once the ICMP Echo Request leaves your device, it travels through the network, passing through routers and switches until it reaches the destination host. At this point, several outcomes could happen:
-
If the host is available and accepts ICMP requests, it will receive the echo request and respond with an ICMP Echo Reply. This reply signals that the host is reachable, and the connection between your device and the host is stable.
-
If the host is offline or doesn’t accept ICMP requests, no reply will be received. After a certain period (timeout), your device assumes the echo request has failed, which is often an indication of a network problem.
-
If the echo request packet doesn’t reach the host within a certain time due to network latency, it will be discarded, and your device will be informed of the packet loss.
The return journey of the ICMP Echo Reply (or the lack thereof) provides vital information about the network. The time taken from sending the request to receiving a reply is measured and reported as the Round-Trip Time (RTT). This measurement is a direct reflection of the latency between your device and the target host. Lower RTT values indicate a faster, more responsive network connection, while higher values may signify potential network issues, such as congestion or improper configuration.
However, it’s important to understand that the RTT also includes processing delay at the host and any delay introduced by intermediate devices like routers. Therefore, while a useful indicator, it’s not the sole metric to rely upon for network performance.
The ping command typically sends multiple echo requests (usually four) to calculate an average RTT. This process mitigates the impact of any anomalies in the network, such as temporary spikes in traffic, that might skew the results of a single echo request.
Ultimately, the ping command’s simplicity and the direct feedback it provides make it a fundamental tool in network troubleshooting and management. Whether you’re assessing network connectivity, diagnosing issues, or evaluating network performance, understanding how ping works is key to interpreting its output accurately and effectively.
Key Terms in Network Troubleshooting
-
ICMP (Internet Control Message Protocol): This is a supporting protocol in the Internet protocol suite that is used by network devices, like routers, to send error messages indicating that a requested service is not available or that a host or router could not be reached.
-
RTT (Round-Trip Time): This is the duration it takes for a signal to travel from a source to a destination, and for an acknowledgment of that signal to be returned to the source. In the context of ’ping’, it’s the time it takes for an ICMP Echo Request to reach the target host and for the ICMP Echo Reply to return.
-
TTL (Time to Live): This is a value in an IP packet that tells network routers whether or not the packet should be discarded. It prevents a packet from circulating indefinitely. Each router that a packet passes through decreases the TTL value by at least one. If the TTL reaches zero, the packet is discarded, and an ICMP “Time Exceeded” message is sent back to the origin.
-
Packet Loss: This refers to the situation where one or more data packets fail to reach their intended destination, typically a host or server. High levels of packet loss can negatively impact network performance and reliability.
-
IPv4 and IPv6: Internet Protocol version 4 (IPv4) and version 6 (IPv6) are versions of the internet protocol that are widely used in data communication over different kinds of networks. IPv6 was developed due to the anticipated exhaustion of addresses available in IPv4.
-
ICMPv6: This is the implementation of the Internet Control Message Protocol for IPv6. It includes more features and is more tightly integrated with IPv6 than ICMP is with IPv4.
Interpreting Ping Output
When you execute a ping command, the results are presented in a series of text lines representing the response to each ICMP echo request. Here’s an example of a ping command:
ping google.comIn some systems, ping might automatically default to IPv6 results. The results shown below are from the output of a ping command using IPv4. In systems where ping defaults to the IPv6 version, the -4 flag can be used to force the use of IPv4, for example:
ping -4 google.comInterpreting the output of ping correctly is essential for understanding a network’s status and diagnosing any issues. Let’s break down a typical ping output:
Pinging google.com [142.251.214.142] with 32 bytes of data:
Reply from 142.251.214.142: bytes=32 time=15ms TTL=58
Reply from 142.251.214.142: bytes=32 time=13ms TTL=58
Reply from 142.251.214.142: bytes=32 time=15ms TTL=58
Reply from 142.251.214.142: bytes=32 time=15ms TTL=58
Ping statistics for 142.251.214.142:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 13ms, Maximum = 15ms, Average = 14ms
-
Pinging: The command begins by stating what host it is pinging. It shows both the domain name and the corresponding IP address.
-
Reply from: Each subsequent line starts with “Reply from” followed by the IP address of the target host, signifying a successful echo reply. If a reply is not received within a certain timeframe, you’ll see a “Request timed out” message instead.
-
Bytes: The “bytes” value represents the size of the ICMP echo reply packet received. This size typically matches the size of the echo request packet sent, though it can vary depending on network conditions and configurations.
-
Time: This value represents the Round-Trip Time (RTT) for each ICMP echo request-reply pair, measured in milliseconds. It reflects the total time taken for the echo request to reach the target host and for the reply to return to the source.
-
TTL: The “TTL” (Time to Live) is a value in an IP packet that tells network routers whether or not the packet should be discarded. Each router that a packet passes through decreases the TTL value by at least one. If the TTL reaches zero, the packet is discarded, and an ICMP “Time Exceeded” message is sent back to the origin. The TTL in a ping response is the remaining TTL value from the original packet after reaching the target and returning. A lower-than-expected TTL can indicate a longer route or a misconfigured network device.
-
Ping statistics: At the end of the ping output, you’ll find a summary of the command’s results. This summary includes the total number of packets sent, received, and lost, providing an immediate overview of packet loss.
-
Approximate round trip times: The final lines of output give you the minimum, maximum, and average RTT for all echo requests. This data is particularly useful in gauging network performance and latency.
Understanding the information contained within the ping output is crucial for diagnosing network problems, monitoring network performance, and ensuring connectivity. The more adept you become at interpreting ping outputs, the more effectively you can manage and troubleshoot your network.
Ping in IPv6 Networks
With the expansion of the internet and an increasing number of connected devices, the Internet Protocol version 6 (IPv6) has been developed to replace the older IPv4. IPv6 has a vastly larger address space than IPv4, which helps accommodate the growing number of internet users and devices.
When it comes to network troubleshooting and diagnostics, ping continues to be a valuable tool in IPv6 networks, just as it is in IPv4 networks. The ping command in IPv6 operates similarly to how it does in IPv4. However, there are some important distinctions to be aware of.
The ping command for IPv6 networks is typically ping6. Depending on the system or platform you’re using, ping may automatically use IPv6 if available. However, in some systems, ping6 must be used explicitly to send ICMP Echo Requests to IPv6 addresses. Here’s an example of a ping6 command:
ping6 google.comThe output from the ping6 command provides similar information as ping in IPv4 networks. It includes the round-trip time for ICMP Echo Requests and Replies, as well as any packet loss. However, you’ll see IPv6 addresses instead of IPv4 addresses.
One of the significant differences between IPv4 and IPv6 when it comes to the ping command is the ICMP version used. While IPv4 uses ICMP, IPv6 uses ICMPv6 (ICMP version 6). ICMPv6 includes more features and is more tightly integrated with IPv6 than ICMP is with IPv4.
While the ping6 command is essential in IPv6 network troubleshooting, other tools can provide more detailed information about the IPv6 network path, such as traceroute6 or MTR. These tools, similar to their IPv4 counterparts, can help network administrators identify where packet loss or latency is occurring in an IPv6 network.
Despite the differences between IPv4 and IPv6, the ping command continues to be a valuable tool for network troubleshooting and monitoring. As networks transition to IPv6, understanding how to use ping6 and interpret its output is crucial for effective network management.
Practical Uses of Ping
Ping finds its use in several practical scenarios in network management:
- Checking network connectivity: The simplest and most common use of ping is to verify that a machine can connect to a network resource, whether local or on the internet.
- Diagnosing network problems: By sending pings to various points in a network, a network engineer can identify where the problem lies.
- Checking the latency of a connection: By comparing the RTT values, one can assess the latency in the network and identify possible performance issues.
- Monitoring the health of a network: Regular ping tests can help monitor the overall health and performance of a network.
Using Ping in Network Troubleshooting
The ping tool serves as a frontline defense in network troubleshooting, helping to identify and resolve network connectivity issues. While its operation seems straightforward, knowing how to interpret the responses in various scenarios can prove invaluable.
In essence, a successful ping means that the network connection between the source and target is working correctly. However, an unsuccessful ping is where the troubleshooting begins. Here are several potential scenarios and their interpretations:
-
Request Timed Out: If you see this message, it usually means that there is no network connection to the host. This could be because the host is offline, there’s an issue with the network link, or a firewall is blocking the connection.
-
Destination Host Unreachable: This indicates that the remote server isn’t responding, which can be caused by several reasons such as a wrong IP address, issues with the routing table, or problems with the network interface.
-
Packet Loss: If you observe that some ping requests are successful while others are timing out, this can indicate a weak or unstable network connection, or network congestion.
Once an issue is identified, network engineers can then further diagnose the problem. For instance, if the host is unreachable, additional tests can be run to determine if the problem is on the local network or on the internet. Similarly, if there’s packet loss, further investigation might be required to pinpoint the source of network congestion.
Ping is often used in combination with other diagnostic tools for a more comprehensive network analysis. For example, a traceroute can be used in conjunction with ping to determine the network path and identify where packet loss is occurring. Similarly, tools like MTR combine the functionality of ping and traceroute to provide a continuous, real-time analysis of the network path.
One thing to note, however, is that some modern systems limit the response to ping ICMP requests or may not respond at all as a security measure. In such cases, ping may not provide accurate feedback on the network’s state.
When using ping for troubleshooting, it’s important to understand its limitations and the context in which it’s used. Nonetheless, it continues to be an essential tool in a network engineer’s toolkit, providing quick and immediate feedback on network connectivity and performance.
As network environments grow increasingly complex, leveraging ping in your troubleshooting methodology can help reduce downtime and maintain network performance. Ultimately, your understanding of the ping command will augment your network troubleshooting capabilities, enabling you to rapidly diagnose and resolve network issues.
Ping Monitoring and Alerting for Network Management
Incorporating ping into your network management process provides several benefits:
- Maintaining optimal response time: By continuously monitoring ping response times, network administrators can identify latency issues early and take corrective measures.
- Avoiding error messages: Regular ping monitoring helps in the timely detection of network errors, enabling quick resolution and minimizing downtime.
- Preventing distributed denial-of-service (DDoS) attacks: Unusual patterns in ping responses can signal a potential DDoS attack.
- Testing connections: Ping is a quick way to test connectivity to network devices or internet resources.
In addition to these benefits, proactive ping monitoring can also facilitate the setting up of alerts based on specific ping behaviors for early detection and resolution of potential network issues. Some scenarios include:
- High latency alerts: Administrators can set an alert to be triggered if the Round-Trip Time (RTT) of a ping exceeds a certain threshold. This helps maintain optimal network performance and user experience.
- Continuous ping failure alerts: These can indicate a complete loss of connectivity with a host or a network segment. Setting alerts for continuous failures aids in maintaining network uptime and quickly identifying points of failure.
- Unusual traffic pattern alerts: An excessive number of ICMP echo requests or unusual patterns can often be a precursor to a DDoS attack. Setting alerts for such anomalies can help detect and mitigate potential attacks before they affect the network’s performance.
Setting up these alerts typically involves the use of network monitoring or network observability solutions that support ping and other network diagnostics tools. These platforms allow administrators to customize their alerting preferences based on their networks’ unique needs, including monitoring packet loss and latency in the cloud.
Automating Ping Tests
Automating ping tests allows for regular and reliable performance data, streamlining network management. Using synthetic monitoring tools like Kentik Synthetics offers a robust and versatile approach to this automation.
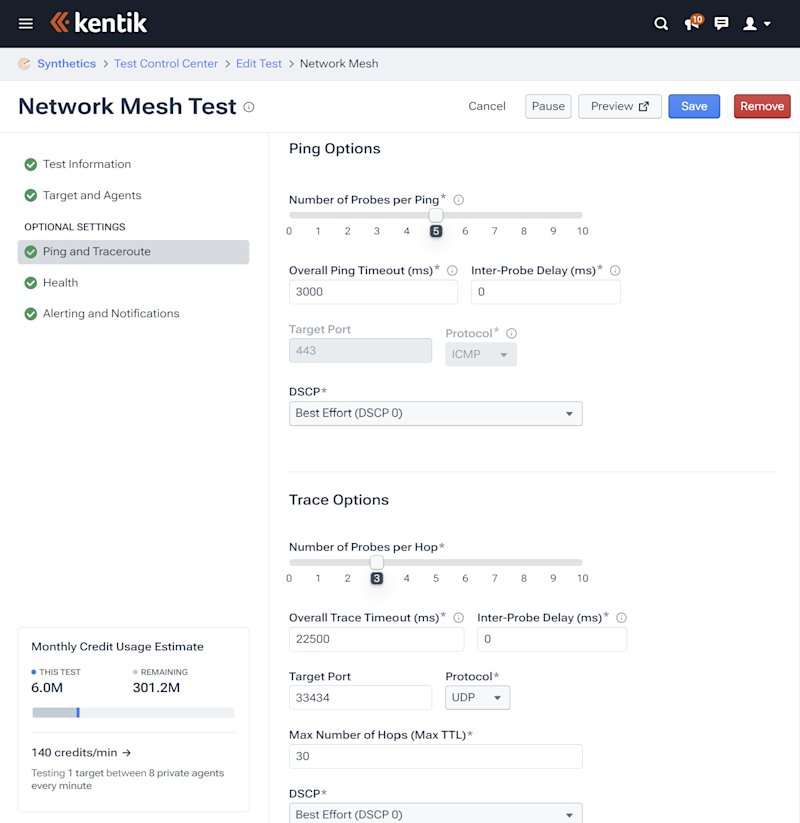
Synthetic monitoring involves generating and observing traffic on your network to simulate user behavior, and Kentik Synthetics’ tests offer a diverse range of options tailored to your needs. These can range from testing internal network infrastructure, connectivity to external applications or services, and even targeted DNS testing.
Specifically, Kentik enables the automation of ping and traceroute tests through multiple test types, including Network Meshes and Grids, Network & Routing Tests, and Autonomous Tests.
-
Network Meshes & Grids test the performance of a network between specified agents, be they within your organization’s infrastructure or in Kentik’s global network. This can be particularly useful for assessing inter-connectivity and performance across disparate areas of your network.
-
Network & Routing Tests allow you to monitor performance from one or more chosen agents towards any IP address, hostname, SaaS service, or individual agent. This can help quickly identify and troubleshoot connectivity issues to specific services or endpoints.
-
Autonomous Tests offer a more intelligent approach, using actual traffic patterns on your network to guide testing. Kentik will analyze traffic patterns and intelligently select IPs to test from or towards, ensuring efficient use of resources and more targeted testing.
Additionally, synthetic monitoring enables automated alerting based on the results of these tests, providing immediate notification of any potential network performance issues. This facilitates prompt action to mitigate any impacts on user experience or service availability.
Through these capabilities, automating ping tests with Kentik Synthetics provides you with constant network performance insights, allows for early identification of network anomalies, and supports proactive management of your network health, resulting in improved service reliability and user satisfaction.
Ping Limitations and Alternatives
While ping is a simple and effective tool for basic network diagnostics, it does have its limitations. For instance, it cannot diagnose all types of network problems, particularly those not related to connectivity. Ping operates at the Internet Control Message Protocol (ICMP) level, which means it can only inform us whether a host is reachable or not. It cannot provide information about higher-level issues such as problems with specific services or applications running on the host.
Another limitation is that ping requests can be blocked by firewalls or other network security measures. Some network administrators set their systems to ignore or drop ICMP Echo requests (the type of packet ping uses) as a defensive measure against certain types of network attacks. This can result in a host appearing to be down or unreachable when it is actually functioning normally, thereby providing false negatives.
However, these limitations don’t mean that ping isn’t useful. Instead, they underline the importance of using ping in conjunction with other tools for a comprehensive assessment of network performance.
One such tool is traceroute, which shows the path that packets take from the source to the destination. Traceroute is useful when you’re trying to pinpoint network delays or find out where packets are being lost or dropped. It provides a hop-by-hop breakdown of the network path, giving more detailed insights into potential issues along the route.
MTR (My Traceroute) is another valuable tool that combines the functionality of ping and traceroute. MTR sends a sequence of ICMP ECHO requests to the destination and simultaneously tracks the route that the packets take. It continually pings all the hops along the path, thereby providing a detailed, real-time analysis of network performance.
Each of these tools provides a different perspective on the network, and using them together can help you paint a comprehensive picture of network health and performance. While ping is great for quick checks of network connectivity and latency, traceroute and MTR can help you dig deeper into problems and identify issues that ping might miss.
How Kentik Can Help with Network Troubleshooting and Management
Ping is a fundamental tool in the realm of network management, offering invaluable help in network monitoring and troubleshooting. Its effectiveness can be augmented with advanced tools and methodologies, like those provided by Kentik’s comprehensive network observability platform.
Tools like Kentik Synthetics offer automated, context-specific testing, providing a powerful means of automating ping and traceroute tests. With these tools and strategies, businesses can ensure a smooth, high-performing network that meets the demands of today’s applications. Discover the benefits of Kentik’s network observability platform for yourself — start a free trial or request a personalized demo today.