Kentik Blog
























Cisco will acquire cloud-cost comparison tool Cmpute.io. Juniper Networks may also be moving on cloud-focused M&A, specifically in the multi-cloud cybersecurity sector. Beyond cloud, the hype of AI continues. Elon Musk’s Tesla team is working on an AI project that could be “the best in the world,” he said this week. More news after the jump…
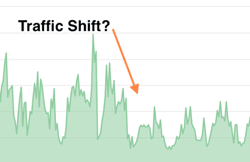
Media reports tell us that Cyber Monday marked a single-day record for revenue from online shopping. We can assume that those sales correlated with a general spike in network utilization, but from a management and planning perspective we might want to go deeper, exploring the when and where of traffic patterns to specific sites. In this post we use Kentik Detect to see what can be learned from a deeper dive into holiday traffic.
This week, we learned the SD-WAN market is forecasted to reach $3.3 billion by 2021. Everyone from Cisco and VMware to AT&T and Charter are taking note. Also this week, Facebook open-sourced its Open/R networking development platform, which it uses for its own wide-area networks, data center fabric and wireless mesh topologies. More after the jump…
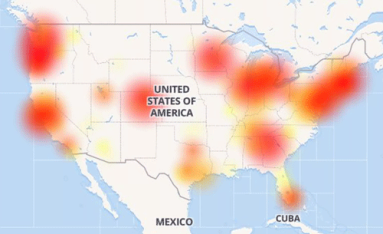
As last week’s misconfigured BGP routes from backbone provider Level 3 caused Internet outages across the nation, the monitoring and troubleshooting capabilities of Kentik Detect enabled us to identify the most-affected providers and assess the performance impact on our own customers. In this post we show how we did it and how our new ability to alert on performance metrics will make it even easier for Kentik customers to respond rapidly to similar incidents in the future.
Last year it was the Dyn outage. This week, a network misconfiguration at Level 3 caused Comcast, Spectrum, Verizon, Cox, RCN and other telecos across the country to feel the effects of the outage. Also this week, findings from a Forrester survey revealed IoT is now an “enterprise security time bomb,” with a huge challenge around being able to identify these types of devices on the network. More after the jump…
Managing network capacity can be a tough job for Network Operations teams at Service Providers and Enterprise IT. Most legacy tools can’t show traffic traversing the network and trend that data over time. In this post, we’ll look at how Kentik Detect changes all that with new Dashboards, Analytics, and Alerts that enable fast, easy planning for capacity changes and upgrades.
This week, VMware announced plans to acquire SD-WAN startup VeloCloud. Google released a new Andromeda SDN to reduce its cloud latency. SoftBank, Facebook, Amazon and others made plans to lay a 60-Tbps undersea cable from Juniper. And Energy giant Chevron selected Microsoft as its preferred cloud provider. Those headlines and more after the jump…
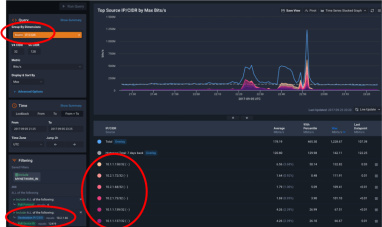
At Kentik, we built Kentik Detect, our production SaaS platform, on a microservices architecture. We also use Kentik for monitoring our own infrastructure. Drawing on a variety of real-life incidents as examples, this post looks at how the alerts we get — and the details that we’re able to see when we drill down deep into the data — enable us to rapidly troubleshoot and resolve network-related issues.
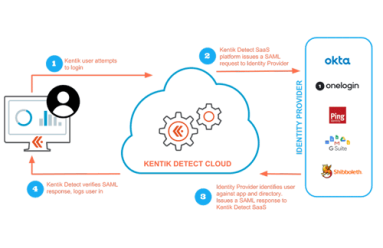
As security threats grow more ominous, security procedures grow more onerous, which can be a drag on productivity. In this post we look at how Kentik’s single sign-on (SSO) implementation enables users to maintain security without constantly entering authentication credentials. Check out this walk-through of the SSO setup and login process to enable your users to access Kentik Detect with the same SSO services they use for other applications.
Reports this week suggest a Russian teleco started providing internet connectivity to North Korea. Russia also made headlines for its covert efforts to steal secrets from the NSA. Oracle made a bunch of news with its OpenWorld conference this week, including taking aim at AWS. And Google disclosed seven vulnerabilities in DNS’ Dnsmasq software. More headlines after the jump…