Understanding AS relationships, outage analysis and more Network Operator Confidential gems

Summary
Doug Madory shared global internet market insights from recent months, and we were joined by Unitas Global for a discussion of their push for greater customer transparency using Kentik Synthetics.
The objective of Network Operator Confidential is to share our global internet market insights from recent months. Kentik, and our customers, have access to views and analysis of global internet traffic that no one else can match.
In our first Network Operator Confidential webinar, I was joined by Doug Madory, Kentik’s director of internet analysis, and Grant Kirkwood, founder and CTO at Unitas Global.
We covered:
- Market share dynamics as revealed by Kentik Market Intelligence (KMI)
- Internet outages
- How Unitas Global uses Kentik to generate a live network status grid for their customers.
Network Operator Market Dynamics
Kentik Market Intelligence (KMI) is a SaaS business intelligence tool that helps network operators understand AS transit and peering relationships for any market in the world.

In the Kentik app, you can view KMI data on ASes by:
- Customer base
- Customer growth
- Peering
And within these views you can isolate:
- IPv4 and IPv6
- Geographic market
- Customer base type: all, retail, wholesale and backbone
Doug demonstrated a number KMI use cases, including how it can be used to identify a provider’s single-homed customers. KMI highlights all the customers of an AS that only use that one provider. The single-homed customers represent prospects for a competing provider’s sales team. Additionally, by identifying contract start dates (coming out soon), service provider sales teams will have a good indication of when they should be reaching out to prospects.
Since Unitas was on the call, Doug showed a KMI view of their rankings and discussed how their recent acquisition of INAP (previously Internap) would be reflected in KMI rankings.
Network outage analysis
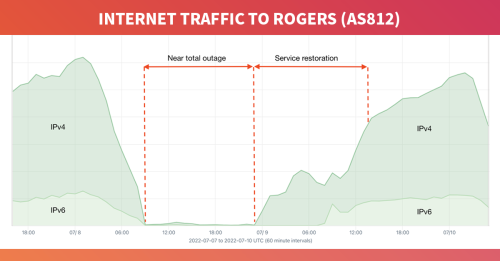
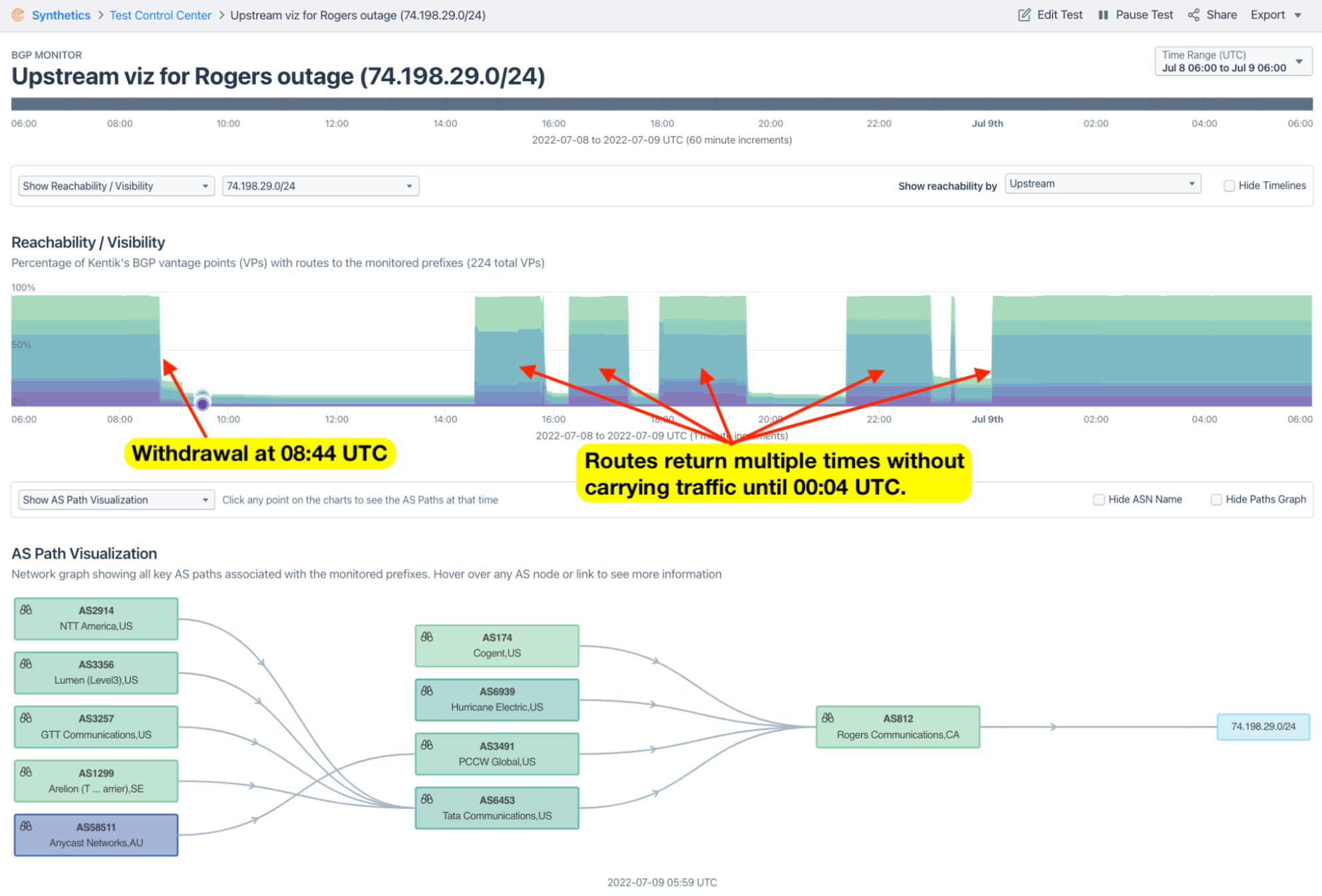
Doug showed his analysis of the recent Rogers outage on July 8, as seen by Kentik. The outage was the largest in Canadian history and took down the internet for 25% of the Canadian population. I won’t go into too much detail as Doug posted a full analysis in A deeper dive into the Rogers outage, but here are some of Doug’s key observations:
- Rogers said a config change removed a filter allowing routes from the internet to be circulated by their interior gateway protocol (IGP) — per Rogers filing with CRTC.
- This led to an update flood exceeding the memory and processing capacity of their routers.
- Initial assessments were that AS812’s routes were withdrawn in BGP rendering the network unreachable.
- However, we could immediately see that many AS812 routes stayed up but still couldn’t communicate.
Therefore, Doug’s opinion is that it wasn’t a reachability problem and that BGP shouldn’t be blamed. In the Rogers outage, exterior BGP withdrawals were symptoms, not the cause of any lack of connectivity.
Next was a discussion of the outages resulting from the Ukraine conflict with particular attention given to Russia rerouting traffic emanating from Kherson. Doug drew parallels with what Russia did in Crimea in 2014. Kherson is now being forced to use transit exclusively from Rostelecom via Crimea which raises a host of surveillance and censorship concerns. Since presenting his analysis on the webinar Doug collaborated with the New York Times on their analysis of the Kherson rerouting and this post gives his full analysis. Here’s an animation that depicts the re-routing:
How Unitas Global exceeds customer expectations with Kentik Synthetics
Unitas is a global access provider that operates a network focused on meeting the needs of large multinational enterprises. Their customers have complex connectivity requirements consisting of internet, cloud, last mile access, and interconnections into the major cloud providers. According to Grant, Kentik is a large part of how they manage and optimize their network and service. The Unitas network encompasses:
- 170+ pops
- 1,100+ customers
- 5,500+ peer networks
Grant spoke about their recent acquisition of INAP and now the Kentik service is helping them combine these networks. INAP was also a Kentik customer before the merger. Having a common set of tooling to understand the traffic profiles has been a huge advantage in combining the networks. Grant mentioned that other large providers who acquired other networks and are still operating separate ASNs ten years later. Grant is confident that they’ll be able to expedite the integration with an assist from Kentik.
Next Grant showed how he uses Kentik Synthetics to generate a live mesh view of the status of the Unitas Global network. Kentik Synthetics private agents are deployed in each of his PoPs giving a view of performance between each of the major metro PoPs. This gives Unitas and their customers a baseline of performance as well as an early warning system of changes to performance on particular routes. The Unitas sales team sees this as a key sales tool and reflects their transparent approach to servicing customers.

Questions
We finished the webinar with a discussion about the impact RPKI ROV was having on mitigating hijacks. It was explained that with the majority of tier 1 providers now dropping RPKI-invalid routes, you can expect a two-third reduction in the propagation of invalid routes. RPKI has now emerged as the internet’s best defense against BGP hijacks due to typos and other routing mishaps. So it’s in your interest to deploy RPKI ROV and reject invalid routes. (Doug alluded to a future post on this subject.)
That’s a wrap on the first Network Operator Confidential. Please contact us if you have any suggested topics for the next NOC webinar.