Network Security and Compliance
Monitor and investigate security incidents across all your networks.
 AI-driven anomaly detection
AI-driven anomaly detection
- Identify network-probing behavior across your network.
- Audit unusual internet traffic.
- Detect traffic to or from embargoed countries.
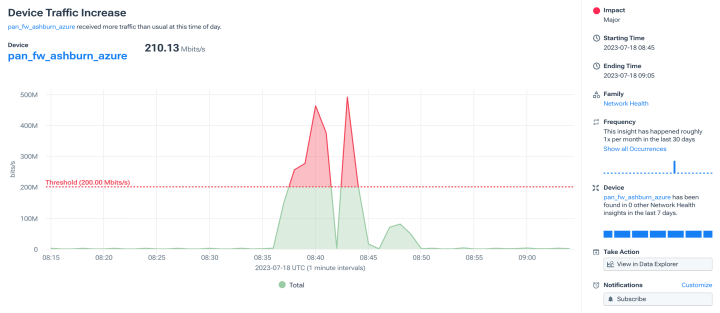
 Quickly detect DDoS attacks with confidence
Quickly detect DDoS attacks with confidence
- Minimize false positives and negatives with advanced detection algorithms.
- Customize out-of-the-box attack profiles.
- See across all networks in real time.
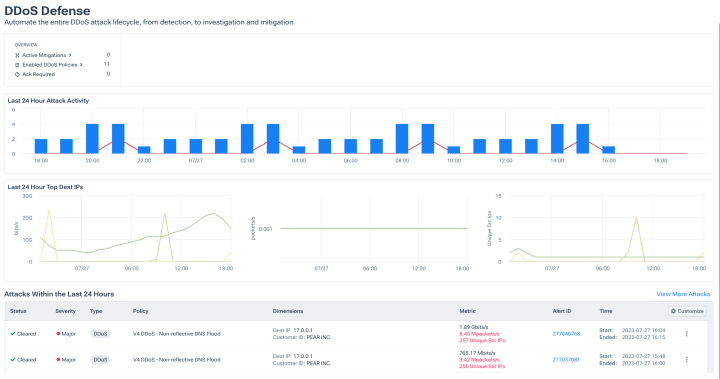
 Streamline attack response
Streamline attack response
- Mitigate attacks using your own infrastructure via RTBH/Flowspec.
- Invoke mitigation through integrations with providers like Cloudflare, Radware, and A10.
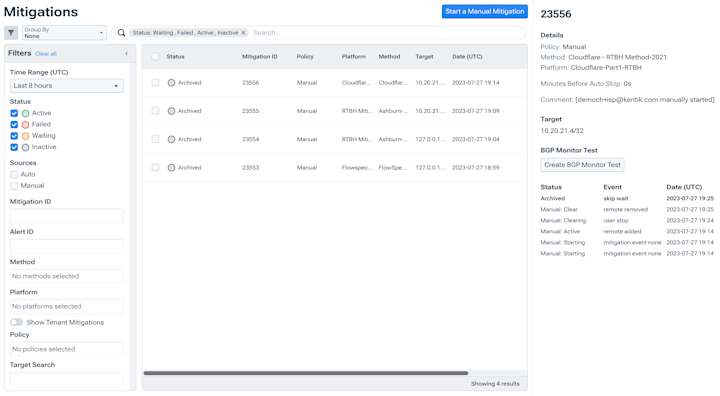
 Validate policy compliance
Validate policy compliance
- Identify and alert on rejected traffic anomalies.
- Verify RPKI enforcement.
- Validate cloud ACLs.
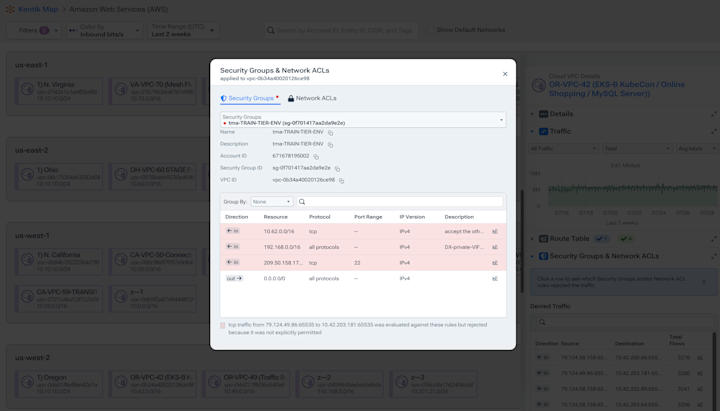
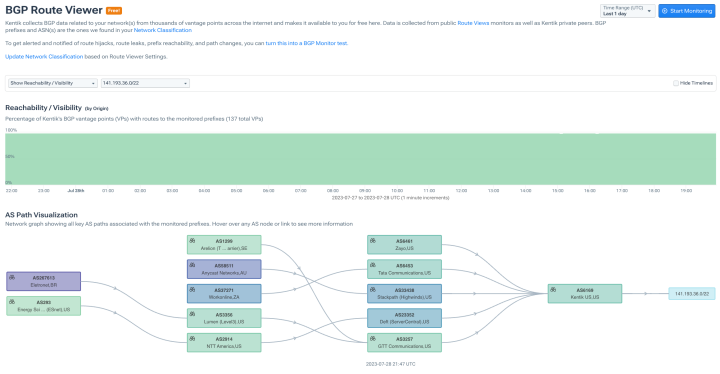
 Detect mis-routed traffic
Detect mis-routed traffic
- Find BGP leaks and hijacks.
- Test BGP reachability.
- Track BGP route changes.
 Identify malware communication
Identify malware communication
- Alert in real time on blacklisted IPs and domains.
- Audit traffic to and from prohibited geographies.
- Filter out VPC black holes.
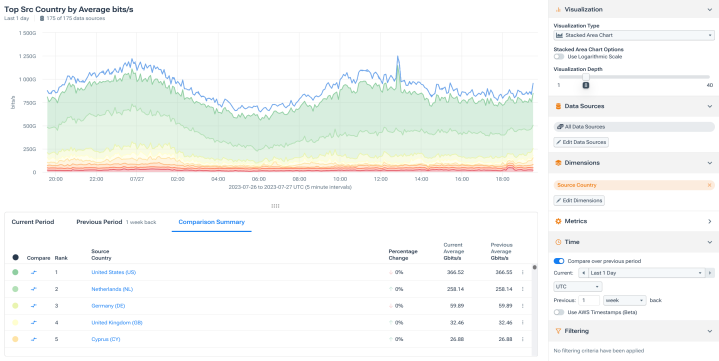
 Full fidelity forensics
Full fidelity forensics
- Understand historical data exfiltration/infiltration.
- Determine what accessed the network with security and business enriched.
- Identify users with ID enriched flow data.

“In a DDoS attack you want to look at traffic volumes, but with Kentik we also can look at source IPs, AS numbers, and other metrics to see if it’s a distributed attack. This is so easy to do in Kentik.”
Jurriën Rasing
Group Product Manager for Platform Engineering, Booking.com
How to Perform a Forensic Analysis After a Security Breach
Explore solutions
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.


