SD-WAN (Software-Defined Wide Area Network) Explained
Businesses today require flexible, efficient, and cost-effective networking solutions. As a result, software-defined Wide Area Networks (SD-WAN) have emerged as a popular choice, offering numerous benefits and improvements over traditional WANs.
As organizations search for “What is SD-WAN,” they encounter numerous articles and videos explaining various vendor-specific SD-WAN solutions. However, few resources offer a detailed explanation of how SD-WANs actually work. This article aims to fill that gap, providing a comprehensive understanding of SD-WAN technology and its benefits.
What is SD-WAN?
SD-WAN, or Software-defined Wide Area Network, revolutionizes the traditional WAN by introducing software-driven controls. At its core, SD-WAN allows organizations to manage WAN operations via a centralized controller, rather than being tied to manual, hardware-based configurations.
Key Highlights of SD-WAN:
- Centralized Control: Unlike traditional WANs (wide area networks) where decisions are made by individual edge routers, SD-WAN centralizes decision-making, offering more control and agility.
- Underlay and Overlay: The physical infrastructure of the WAN is termed the ’underlay’. The logical configuration—whether it’s a full mesh, partial mesh, hub and spoke, or point-to-point—is the ’overlay’.
- Transport Independence: SD-WAN gives the flexibility to utilize any transport method, be it MPLS, 4G/5G LTE, or broadband, providing cost-effective and efficient connectivity.
- Enhanced Performance: With its ability to recognize and prioritize traffic, SD-WAN ensures optimal application performance and improved user experiences.
- Simplified Management: Centralized control means reduced complexity. Operations become streamlined with automation and more intuitive management tools.
By leveraging SD-WAN, businesses can achieve superior network performance, greater flexibility, and a significant reduction in operational challenges over traditional wide area network environments.

Two Planes and Some SD-WAN Terms
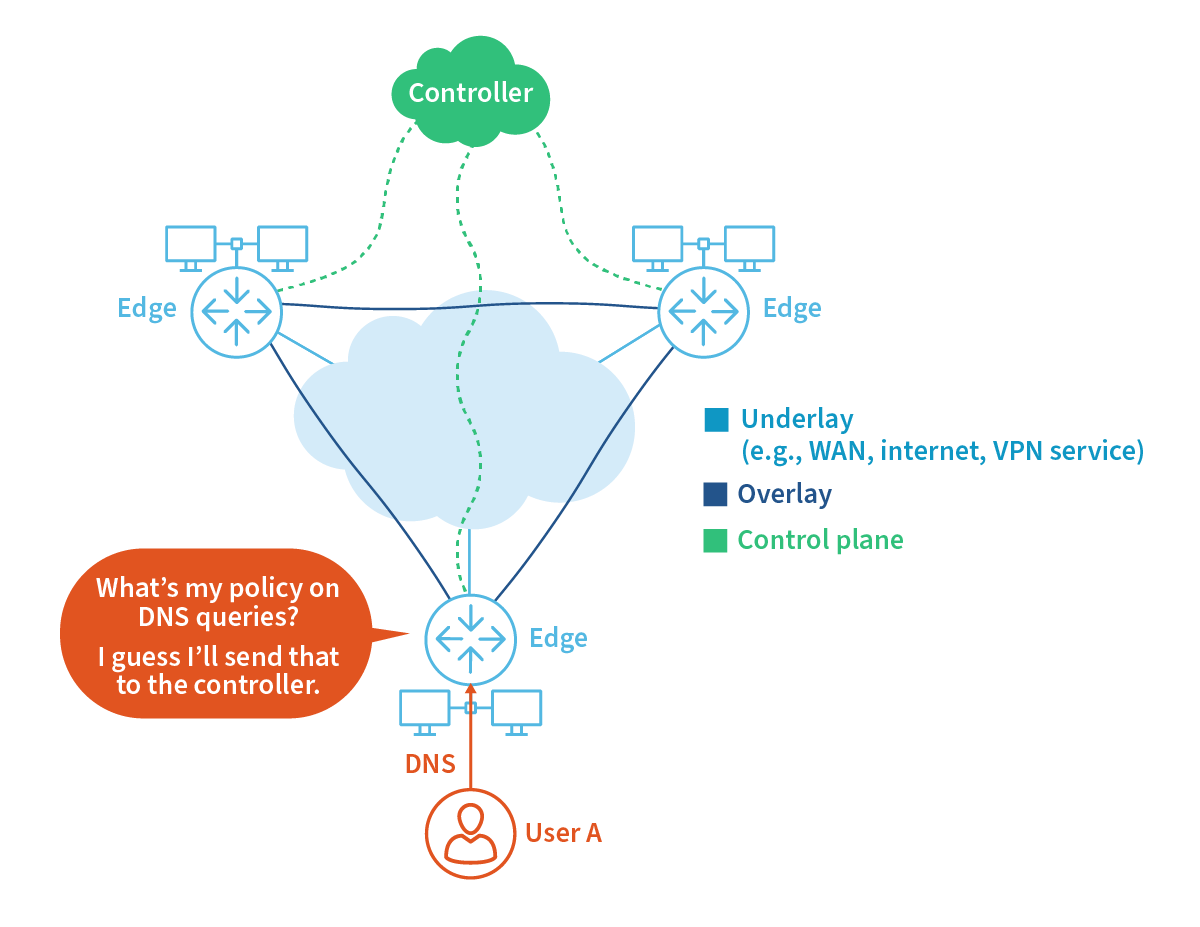
In the context of SD-WAN architecture, the term “edge” typically refers to devices situated at the boundary of two networks. These devices, often known as “edge devices” or “edge routers” in traditional WANs, connect local networks to wide-area networks or the public internet. They play a pivotal role in SD-WAN by providing connectivity to the WAN fabric and are responsible for directing traffic based on policies set by the centralized controller.
As stated above, connection requests are sent by the edge up to the controller to check policy. This is done over a secure connection called the control plane. Once the edge hears back from the controller, a connection is established. The end-user connections traverse the SD-WAN fabric over the data plane.
To summarize what has been covered to this point:
- Edge: In traditional WANs, these are called edge routers and provide connectivity to the WAN fabric. They differ from routers because they send connection requests to the controller and make only a few connection decisions locally.
- Traditional WANs: Edge routers connect to public internet or private WAN connections such as MPLS. Typically forwarding decisions are programmed locally into the router to choose the pathway. Configuration of local traditional routers is usually static, using local routing protocols like OSPF, BGP, etc.
- SD-WAN: The control plane provides the programming and choices dynamically. Configuration is applied at the control plane and handed off to the local edge device for execution.
- Controller: The controller is usually located in the cloud. It communicates with the edge devices via the distributed control plane over a secure connection. At the controller, NetOps configures traffic prioritization policy. This can be based on characteristics such as the top level domain where the traffic is headed. The controller is the central point of configuration for all edge devices. Redundant, fault-tolerant controllers can be configured to help ensure “five nines” of availability.
- Underlay: The traditional physical infrastructure of the WAN.
- Overlay: A series of VPNs making up the logical topology used to move traffic in the configurable direction between end systems.
- Control plane: A secure connection between the edge devices and the functions provided by the controller.
- Data plane: The fabric that carries the network connections.
The above terms are just the beginning when entering the world of SD-WAN. We try to stay generic here, but each vendor contributes significantly to this list of acronyms.
The definitive guide to running a healthy, secure, high-performance network

How Does SD-WAN Work?
SD-WAN (Software-Defined Wide Area Network) operates by centralizing network control through software, allowing for dynamic path selection and traffic management. It uses a centralized controller to determine the most optimal path for data transmission, considering factors like network congestion, latency, and current policy settings. By decoupling the control and data planes, SD-WAN offers greater flexibility, agility, and efficiency over traditional WANs.
Now, let’s illustrate this with an example:
Let’s say User A would like to make a connection to salesforce.com. First, the user may need to ARP for the DNS. The edge receives the ARP and resolves it as specified by the policies set in the controller.
This means the edge may resolve it locally, send it to a specified DNS or send it to the controller for resolution. This process is vendor-dependent.
Once User A has the MAC for the DNS, a request is sent to the DNS to resolve salesforce.com (for example) to an IP address. Again, the process is vendor dependent, but in most cases, the edge will send this request to the controller. The controller evaluates the request for salesforce.com and compares it to the configured policy list.
Many policies are based on top-level domain (TLD). Here are a few examples:
- If the request is for netflix.com (for example), deny it.
- If the request is for facebook.com, allow it, but limit bandwidth to 250Kbits/s.
- If the request is for salesforce.com, allow it with the highest priority.
These instructions are then sent back down to the edge for enforcement, and the edge replies to User A’s DNS query for salesforce.com with the proper IP address. Keep in mind that if the end user’s web browser is configured to use DoH (DNS over HTTPS), this could cause problems for some SD-WAN solutions as the browser receives the IP address back from a different DNS instead of the controller.
User A then sends a SYN to the salesforce.com IP address to initiate the TCP handshake required to make an HTTPS connection. The edge provisions for the connection as instructed by the controller.
Sometimes, something happens like congestion, packet loss, latency, or a severed WAN connection. Then what happens? What will the SD-WAN environment do about it? The answer to this is generally a significant vendor differentiator.
How do SD-WANs Ensure Connectivity?
Some vendors build technology into the edge devices that will routinely ping high-priority destinations (like salesforce.com) to measure things like latency, packet loss, and jitter. Think of it as a type of synthetic monitor. When the edge detects a problem on a connection to a high-priority domain, it may balance the flows or packets to the target over multiple links. This is because most SD-WAN implementations support something called active/active, where there are no secondary links, rather, only additional load-carrying connections.
Benefits of SD-WAN
SD-WAN offers numerous advantages beyond cost savings by replacing expensive leased lines, such as MPLS, with VPNs over the internet. Here are some additional SD-WAN benefits:
-
Multiple Redundant Links: The best approach is to use active/active configurations across two or more links. These links can be private WAN, public internet, or LTE connections. In addition, redundant edge devices can be deployed in pairs, providing fault tolerance at local sites.
-
Fast Connection Failover: Some vendors claim failover times under one second. Traffic shaping allows connections to specified TLDs to receive a predetermined bandwidth and priority. Other TLDs can be blocked or assigned fixed bandwidth limits.
-
WAN Optimization: This feature is vendor-dependent but might be available on the edge device. It can reduce bandwidth consumption using compression techniques.
-
Firewall Integration: Some vendors include this feature on the edge devices. Packet loss compensation or packet duplication ensures that packets carrying content, such as voice, are replicated and used at the other end of a connection if packet loss occurs.
-
Redundant Controllers: To maintain five-nines of availability, multiple controllers can be deployed to ensure fault tolerance.
-
Advanced Router Features: Features like OSPF, EBGP, NetFlow, IPFIX, SNMP, Syslog, and more are supported.
Remember that many of these benefits are vendor-dependent and should be tested under load to ensure real-world operation.
Ultimately, the only SD-WAN features that matter are the ones that optimally support business-critical applications. Investing in additional features like sub-second convergence, mesh topologies, multitenancy, and multicast only makes sense if they enhance the user experience.
Measuring SD-WAN performance: Trust but Verify
Every SD-WAN vendor will tout how necessary their features are and how great their performance is. However, one of the areas that is sometimes overlooked during the sale is performance monitoring. After the SD-WAN deployment, most NetOps teams want insight into how the SD-WAN is performing.
Companies like Cisco, Silver Peak/HPE, and VMware export IPFIX, allowing network observability companies to provide performance insights into the SD-WAN fabric. Flow data is correlated with telemetry that is exported from the SD-WAN management platform. For example, the Kentik architecture can ingest vendor-specific fields, which are very important in the SD-WAN space (e.g., Viptela: VPN Identifier, and Silver Peak: Application, Business Intent Overlay).
For example, the Silver Peak-Kentik integration features provide the inclusion of application name dimension and business intent overlay (BIO) into interface traffic metadata source.
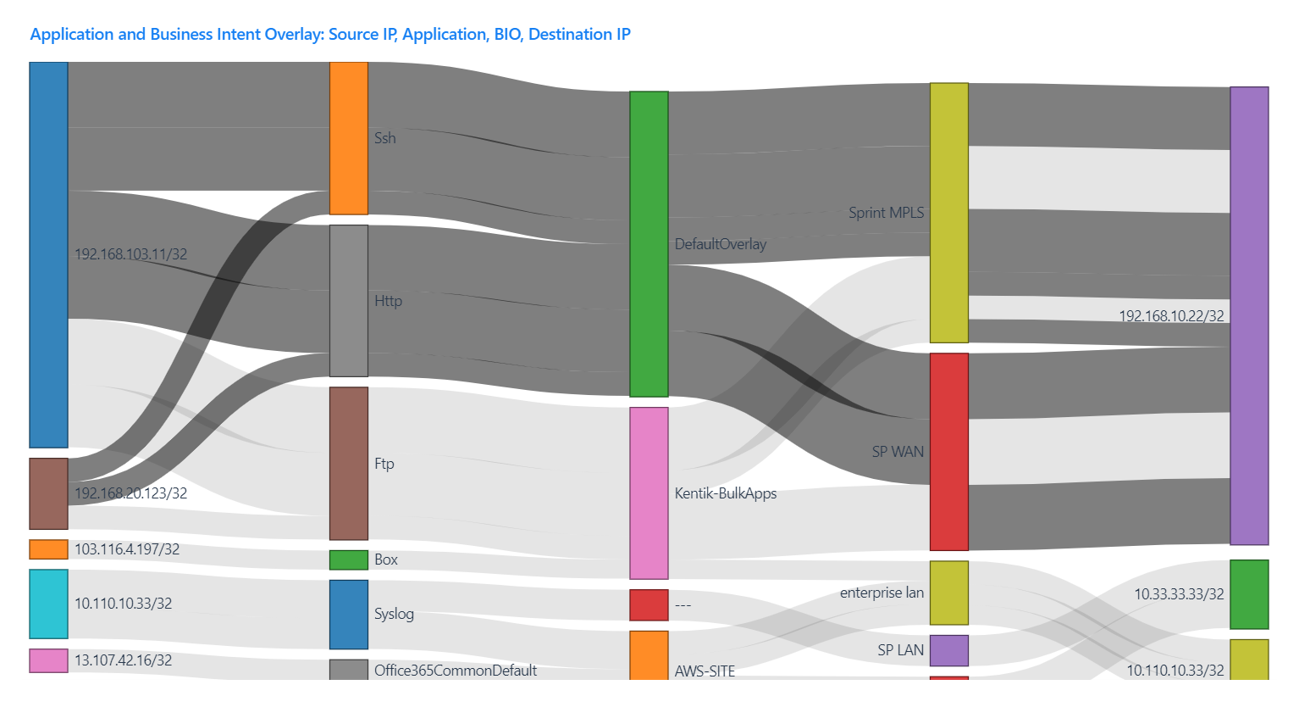
The above screen capture from Kentik shows which subnets are speaking with each other. The user can also see the relationship between overlay networks and applications. These combined data sets allow NetOps to discover what applications are running between sites, the internet, and the data center. They can be used to better understand service providers, link utilizations, and network traffic patterns. These details help NetOps fine-tune policies at the SD-WAN controller.
Kentik didn’t leave any SD-WAN vendors out. We provide overlay, underlay, and application traffic visibility to Silver Peak, Cisco, VMware and all other major open SD-WAN solutions.

SD-WAN Overlay and Underlay Networks
Understanding the core concepts of overlay and underlay networks is essential when designing, implementing, and managing an SD-WAN infrastructure. These two layers work together to create a flexible, efficient, and scalable networking solution. By understanding the roles and interactions of overlay and underlay networks in SD-WAN, businesses can better design, implement, and manage their network infrastructures to meet their unique requirements and demands while maximizing performance, security, and cost-efficiency.
What is SD-WAN Underlay?
SD-WAN underlay networks represent the physical infrastructure of the WAN, including the routers, switches, and cables that create the underlying foundation for data transmission. In a traditional WAN, underlay networks consist of leased lines such as MPLS or other dedicated connections, which can be costly and inflexible.
Underlay networks typically leverage more cost-effective internet connections and VPNs to create secure and reliable communication links between various locations in an SD-WAN environment. This allows organizations to reduce their reliance on expensive leased lines while maintaining the required performance, security, and stability.
What is SD-WAN Overlay?
SD-WAN overlay networks represent the logical topology that dictates how data is transmitted over the underlying physical infrastructure. Overlay networks are created using virtual connections, often through VPNs, which enable secure and efficient communication between various locations.
In an SD-WAN environment, overlay networks allow greater flexibility and control over the network’s topology. This includes the ability to create full mesh, partial mesh, hub and spoke, or point-to-point configurations, depending on the organization’s needs and requirements.
By abstracting the overlay from the underlay, SD-WAN provides a way to manage and optimize network resources without being constrained by the physical infrastructure’s limitations. This allows businesses to adapt their networks to meet evolving demands, such as increasing bandwidth requirements, adding new locations, or adjusting network policies.
The Interaction of Overlay and Underlay Networks in SD-WAN
In an SD-WAN infrastructure, the interaction between the overlay and underlay networks is critical for optimal performance and efficient resource utilization. The centralized controller in SD-WAN manages and controls the overlay networks, making intelligent decisions about how to route and optimize traffic based on real-time network conditions and configured policies.
The underlay network, in turn, provides the physical foundation for these virtual connections, ensuring that data can be transmitted securely and reliably between locations. By monitoring and managing both the overlay and underlay networks, SD-WAN can dynamically adjust network traffic flows to provide the best possible performance and user experience, even during times of network congestion or instability.
Benefits of Overlay and Underlay Networks in SD-WAN
The separation of overlay and underlay networks in SD-WAN offers several key benefits for businesses, including:
- Flexibility and Scalability: By decoupling the logical topology from the physical infrastructure, SD-WAN allows organizations to adapt their networks to meet changing demands without needing costly and time-consuming hardware upgrades.
- Cost Savings: By leveraging cost-effective internet connections and VPNs for underlay networks, SD-WAN can reduce organizations’ reliance on expensive leased lines and help lower overall networking costs.
- Improved Performance and Reliability: SD-WAN’s centralized controller can monitor and optimize both the overlay and underlay networks in real-time, ensuring consistent application performance and user experience even during periods of network congestion or instability.
- Simplified Management: The centralized control and management of overlay networks in SD-WAN simplify the deployment and modification of network policies, reducing the complexity and expertise required for effective network management.
What are the Differences Between WAN and SD-WAN?
While Software-Defined Wide Area Networks (SD-WAN) are a subset of Wide Area Networks (WAN), the two have distinct differences. Understanding these differences can help organizations make better decisions when designing and implementing their network infrastructures. Here are the primary differences between traditional WAN and SD-WAN.
1. Control and Management
In a traditional WAN, control and management are typically done by manually configuring edge routers using routing protocols like OSPF, BGP, and static routes. This requires extensive knowledge of networking protocols and can be time-consuming, especially in large networks.
SD-WAN, on the other hand, centralizes control and management through a controller. This simplifies network management and allows for flexibility and agility when deploying and modifying network policies. In addition, the controller can make intelligent decisions based on network conditions and user requirements, allowing for better control and optimization of network resources.
2. Traffic Routing and Optimization
Traditional WANs rely on pre-configured static routes or routing protocols to determine the best path for data transmission. Unfortunately, this can lead to inefficient use of network resources and suboptimal performance, especially when network conditions change.
SD-WAN uses a more dynamic approach to traffic routing and optimization. It can monitor network conditions in real time and adjust traffic flows accordingly to provide optimal performance. This helps ensure consistent application performance and user experience, even during network congestion or instability.
3. Cost and Deployment
WAN connections often rely on leased lines, such as MPLS, which can be expensive and inflexible. Deploying traditional WANs can also be complex, requiring significant upfront investment in hardware, software, and expertise.
SD-WAN leverages more cost-effective internet connections and VPNs to create secure, reliable connections between locations. This reduces the reliance on expensive leased lines and allows for more flexible, scalable deployments. SD-WAN also simplifies the deployment process, enabling organizations to roll out new locations or change existing ones more quickly and easily.
4. Security
In traditional WANs, security is typically implemented through standalone security appliances, such as firewalls, intrusion prevention systems, and secure web gateways. These devices often need to be managed and maintained separately from the WAN infrastructure, adding complexity and potential points of failure.
SD-WAN integrates security features directly into the edge devices and the controller, providing a more unified security approach. In addition, some SD-WAN solutions offer built-in firewalls, intrusion prevention, and other security features, simplifying management and reducing the attack surface.
5. Redundancy and Failover
Traditional WANs typically use a primary and secondary link for redundancy, with the secondary link only becoming active when the primary link fails. This can lead to underutilization of resources and increased costs.
SD-WAN supports active/active configurations, where multiple links can be used simultaneously to balance traffic and provide redundancy. This helps maximize network resource utilization and ensures fast, seamless failover in the event of link failure.
SD-WAN offers a more modern, flexible, and efficient approach to wide-area networking than traditional WANs. By centralizing control and management, optimizing traffic routing, reducing costs, enhancing security, and improving redundancy and failover, SD-WAN can significantly benefit organizations looking to optimize their network infrastructure.
Conclusion
SD-WAN is a powerful network architecture and technology that helps on multiple fronts. SD-WAN can improve performance, increase security, and lower costs all at the same time. However, like any networking technology, SD-WAN delivers more benefits when it is properly managed. Auditing application traffic policies, understanding the SD-WAN traffic paths taken, and link utilization are critical maintenance functions. The ability to troubleshoot, plan capacity, and optimize costs is also important. Network observability solutions like Kentik can help you perform the operational oversight needed to make SD-WAN successful.
Unlock the Power of Modern WAN and SD-WAN with Kentik
Today’s cloud-centric enterprise WAN landscape demands more than just deployment. It requires deep awareness, comprehensive visibility, and proactive network monitoring. Kentik helps monitor and manage SD-WAN and optimize enterprise WAN deployments—improving routing, security, and network operations.
Kentik’s network observability platform offers an unrivaled view of your network, spanning from the internet underlay, through the SD-WAN overlay, and right to the edge. Whether it’s the connectivity between users, SaaS, cloud-based applications, network services, or the vast expanse of the public internet, Kentik ensures you’re not in the dark.
Kentik gives NetOps pros the ability to understand and visualize diverse data across your cloud, campus, and SD-WAN networks. When performance takes a hit, Kentik’s insights into the underlay and overlay interaction become invaluable. And Kentik’s synthetic testing capabilities provide firsthand knowledge of application performance, helping teams quickly address potential bottlenecks.
Understanding global internet health and its impact on applications is crucial. Kentik alerts users about potential connectivity issues to vital public resources, giving a detailed view beyond mere up/down metrics. It tracks metrics like latency, jitter, and changes in external service connections. These deep insights empower NetOps and DevOps teams to proactively monitor end-user experiences, ensuring optimal application delivery and user satisfaction.
Security remains paramount, and Kentik is well-equipped to defend against modern threats. From malware and DDoS attacks to ensuring SD-WAN policy compliance and BGP route safety, Kentik’s network security tools offer robust protection. Additionally, the platform aids in keeping traffic links secure, validating SD-WAN policies, and monitoring upstream providers for potential threats.
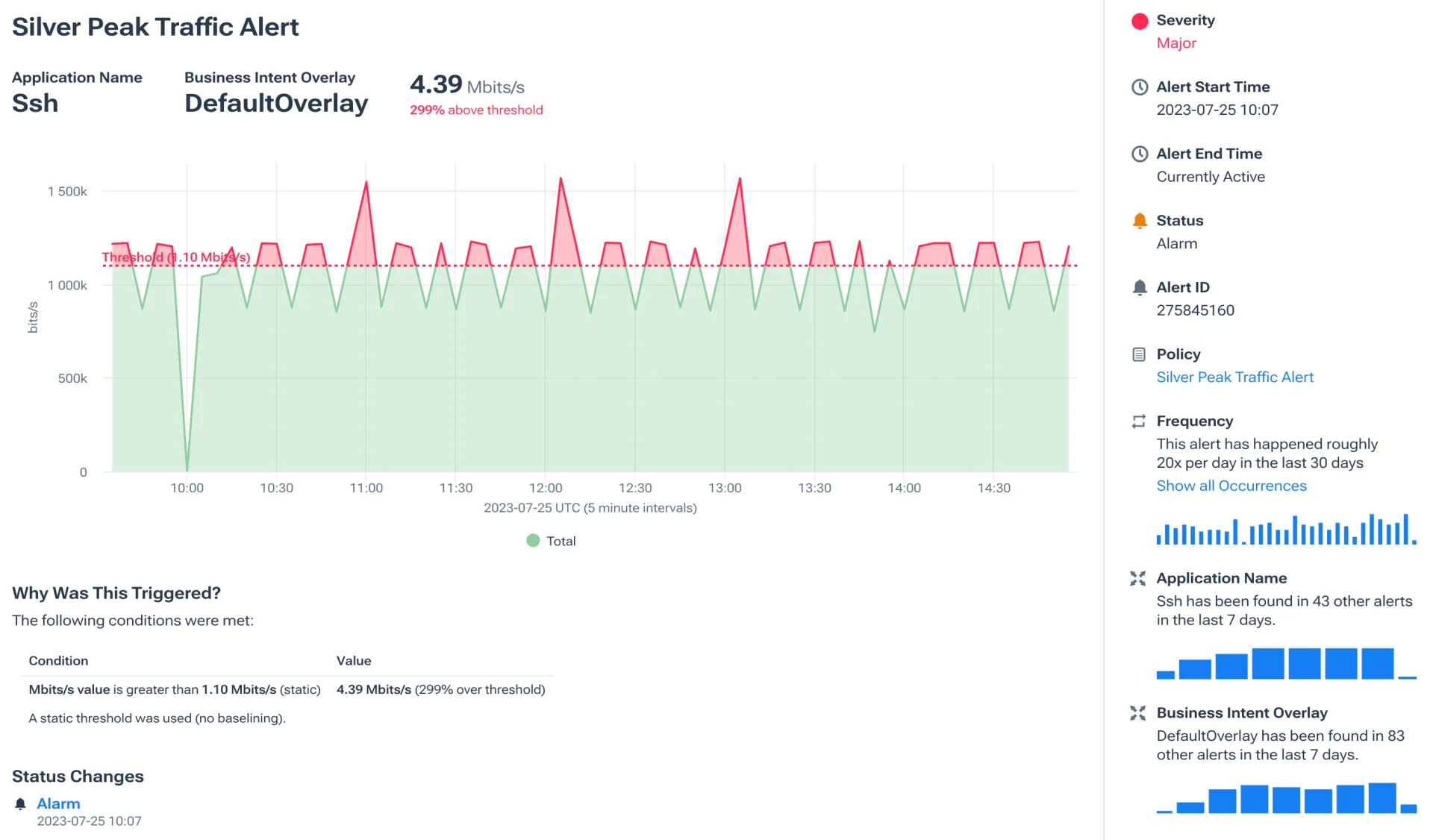
Kentik also provides unparalleled visibility into service provider performance, making network negotiations more informed and impactful. Its insights into routing, peering, and potential BGP connectivity issues ensure that networks—whether owned or third-party—operate at their peak.
To explore the future of networking and see how Kentik can redefine your enterprise WAN and SD-WAN experience, start a free trial or request a personalized demo today.


