NetFlow Tools
NetFlow tools are a cornerstone of modern network management and analysis. As integral components in a network engineer’s toolkit, they facilitate detailed insights into network behavior and performance. NetFlow tools interpret and analyze NetFlow data generated by routers, switches, and other network devices, making monitoring, troubleshooting, and optimizing network environments easier. With their aid, network professionals can effectively control network traffic, optimize resource usage, improve network security, and facilitate successful capacity planning.
What are NetFlow Tools?
NetFlow tools are software applications designed to collect, analyze, and present NetFlow data. NetFlow is a network protocol developed by Cisco Systems that collects IP traffic information as records and sends this data to a collection point (like a NetFlow collector). These tools provide network administrators with valuable insights into traffic flow patterns and volume across their networks, contributing significantly to understanding and enhancing network performance, security, and reliability.
NetFlow tools analyze the data collected and provide actionable insights to help network professionals answer critical questions, such as identifying which applications use the most bandwidth, who the top traffic contributors are, or spotting unusual traffic patterns that could signify a network security risk. These comprehensive insights enable network administrators to make informed decisions to enhance network performance, optimize bandwidth utilization, and strengthen network security protocols. NetFlow tools, thus, are indispensable for modern network observability and management.
How NetFlow and NetFlow Tools Help Network Engineers
Characterizing IP traffic and understanding how and where it flows is critical for ensuring network availability, performance, and security. A NetFlow tool is used to perform monitoring, troubleshooting, and in-depth inspection, interpretation, and synthesis of network traffic flow data. Analyzing networks with a NetFlow tool facilitates more accurate capacity planning and ensures that resources are used appropriately in support of organizational goals.
NetFlow tools help network operators to determine where to apply Quality of Service (QoS) policies, as well as how to optimize resource usage. Additionally, NetFlow tools can play a vital role in network security by detecting Distributed Denial-of-Service (DDoS) attacks and other undesirable — or anomalous — network events and activity.
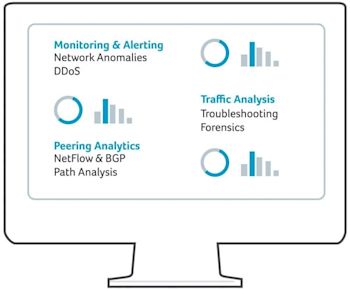
Overcoming Common Network Challenges with a NetFlow Tool
NetFlow tool-based analysis offers insight to overcome many common challenges encountered by network operators, managers, and engineers, including:
- Monitoring major contributors of network traffic: Network engineers can easily see ”top talkers” and “top listeners” on the network.
- Understanding application traffic and its network impact: An example is identifying unusual application network loads such as video content or large file transfers. NetFlow statistics can also be used to measure how application and policy changes affect costly WAN traffic.
- Optimizing Internet peering relationships: Organizations operating BGP peerings to maintain multi-homed connectivity to the Internet can utilize NetFlow data—fused with BGP routing data—to perform sophisticated peering analysis and optimize their peering arrangements. This can help improve service quality, reduce peering costs, and even uncover new revenue opportunities for operators of carrier networks (e.g., telcos, ISPs, CDNs, and MSOs) by analyzing network usage patterns.
- Troubleshooting and understanding network pain points: NetFlow tool-based analysis can be used to diagnose slow network performance, recognize bandwidth hogs or misconfigurations, and characterize bandwidth utilization quickly via the intrinsic representation of traffic totals and traffic details.
- Detecting unauthorized WAN traffic: By analyzing a network with a NetFlow tool, it becomes possible to avoid costly upgrades to expensive WAN services by identifying applications that cause network congestion, verifying legitimacy, and adjusting delivery policies to mitigate any adverse impact on higher-value, concurrent traffic streams.
- Denial-of-service attacks and anomaly detection: NetFlow tools can also be used to detect DoS/DDoS attacks and other types of network behavior anomalies.
- Validating QoS parameters: Because NetFlow includes all packet priority markings, it can be used to confirm that appropriate bandwidth has been allocated to each Class of Service (CoS) and that no CoS is over or under-subscribed.
Various organizations, such as network operations, engineering, planning, architecture, and security, can use NetFlow tools as a primary source of intelligence. Proper use of NetFlow tool-based analysis can reduce the number of hardware and software technologies needed to manage networks, providing benefits including:
- Reducing network administration costs
- Enhancing cross-organizational collaboration and communications
- Helping cross-functional teams get the best return on their network investments
The definitive guide to running a healthy, secure, high-performance network

Network Planning and Analysis
NetFlow data provides information that can be used for both (1) sophisticated analysis to optimize strategic network planning (e.g., who to peer with, backbone upgrade planning, routing policy planning) as well as (2) making tactical network engineering decisions (e.g., adding additional VIPs to routers, upgrading link capacity) that can minimize the total cost of network operations while maximizing network performance, capacity, and reliability.
Network Monitoring
NetFlow data enables extensive, near real-time network monitoring capabilities. Flow-based analysis techniques can be used to visualize traffic patterns associated with individual routers and switches and on a network-wide basis (providing aggregate traffic or application-based views) to provide proactive problem detection, efficient troubleshooting, and rapid problem resolution.
Analysis of NetFlow can be used as a basis for real-time alerting, improving the ability of network operators to react quickly and accurately to major service disruptions and get early warning indicators of potential performance and service quality degradations that warrant proactive intervention.
Application Monitoring and Profiling
NetFlow data enables network managers to gain a detailed, time-based view of application usage over the network. Any common NetFlow type can be used to recognize applications by port/protocol, and some of the more advanced extensions to NetFlow (via sFlow or v9/IPFIX templates), such as Cisco’s Application Visibility and Control (AVC) solution, can document an even greater level of application detail. Content and service providers can use this information to plan and allocate network and application resources (e.g., web server sizing and location) to meet customer demands responsively. Enterprises can use these same insights to understand application dependencies and resource consumption.
User Monitoring and Profiling with NetFlow Tools
NetFlow data enables network operators to understand customer/user utilization of network and application resources. This information can then be used to efficiently plan and allocate access, backbone, and application resources while detecting and resolving potential security and policy violations.
Related Reading and Resources
At Kentik, we’ve taken NetFlow analysis to big data scale and offered it as an easy-to-use SaaS. Learn more about NetFlow analysis from these blog posts: