Stop DDoS Attacks Before They Happen
From botnets to threat-feeds, detect, remediate, and prevent DDoS attacks.
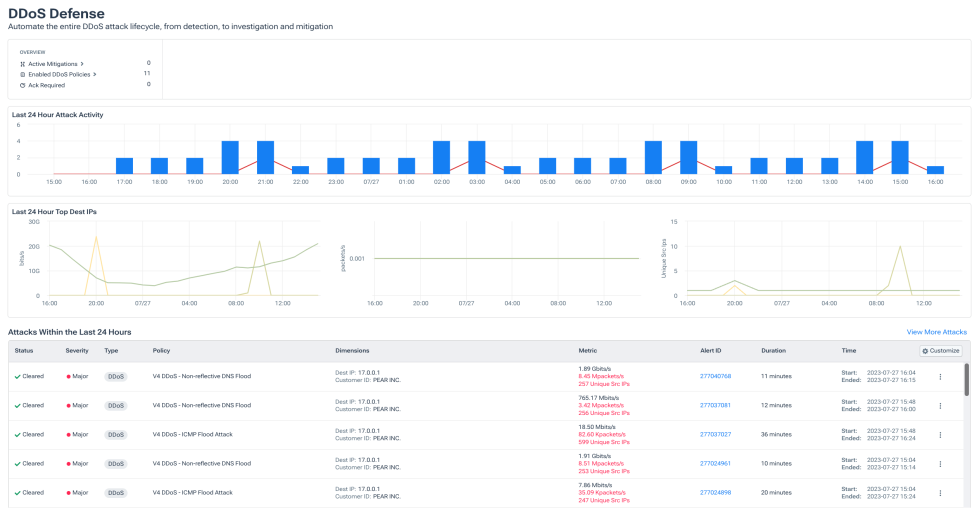
Early detection
ML-based traffic profiling significantly reduces response time.
Automate attack mitigation
Quickly respond to attacks with automated DDoS mitigations.
Prevent future attacks
Understand attack vectors and patterns to stop future attacks.
Powerful DDoS detection
- Quickly detect threats using AI-driven insights for different attack profiles.
- Identify malicious botnet traffic or communication with embargoed countries.
- Integrate and enrich data with threat intelligence feeds.
- Built for complex networks.
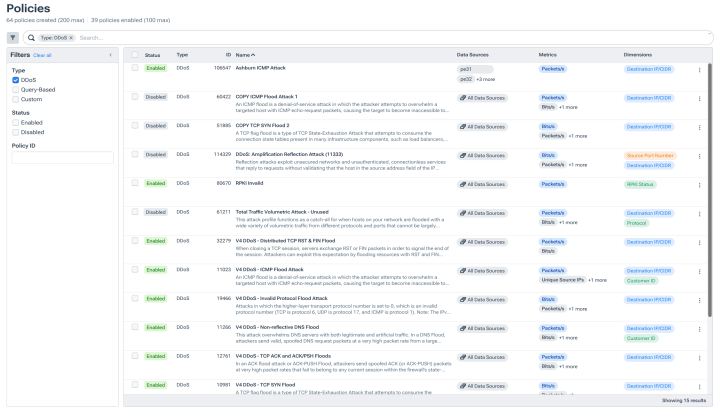
Stop bad actors in their tracks
- Kick off automated mitigation with easy out-of-the-box integrations.
- Divert traffic using RTBH.
- Trigger Flowspec to filter, redirect, or rate limit traffic.
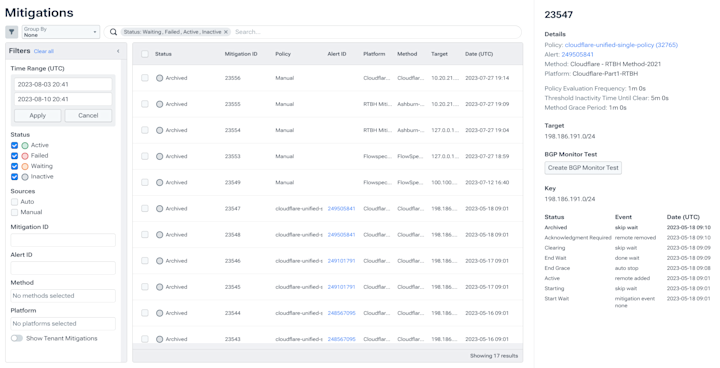
Harden your security posture
- Understand any attack using customer-enriched forensic network data.
- Analyze traffic using guided data exploration to uncover attack vectors.
- Export data to any SIEM seamlessly.
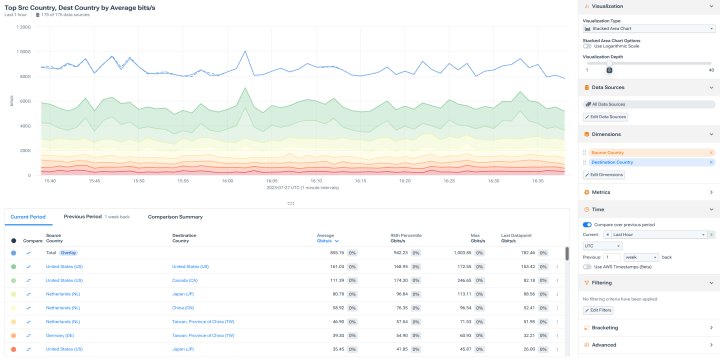
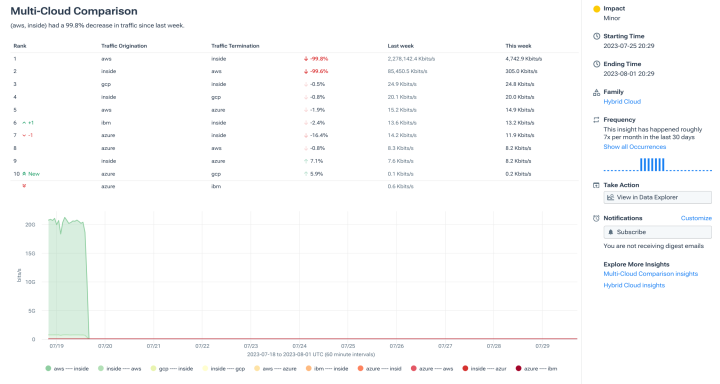
Confidently detect real attacks
- Know where the traffic is coming from when analyzing spikes.
- Analyze the traffic types to better assess threats.
- Quickly determine if an attack is happening.
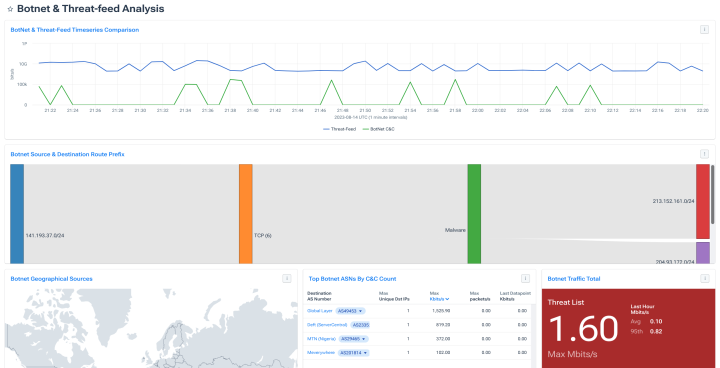
Protect against botnets
- Detect connections to known botnet command and control hosts on the internet.
- Analyze botnet traffic characteristics and trends over time.
- Alert on significant changes in threat traffic volume, routes and source geo-locations.

“In a DDoS attack you want to look at traffic volumes, but with Kentik we also can look at source IPs, AS numbers, and other metrics to see if it’s a distributed attack. This is so easy to do in Kentik.”
Jurriën Rasing
Group Product Manager for Platform Engineering, Booking.com
How to Perform a Forensic Analysis After a Security Breach
Explore products
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.



