Network Operator Confidential: Diving Into Our Latest Webinars on DDoS Trends, RPKI Adoption, and Market Intel for Service Providers

Summary
Didn’t have time to watch our two recent webinars on the top trends network operators need to know about to be successful in 2023? We’ve got you covered. Let’s look at the biggest takeaways and break down some key concepts.
Kentik’s own Doug Madory, head of internet analysis, recently joined Mattias Friström, VP and chief evangelist at Arelion, and Sonia Missul, IP transit product manager at Orange International Carriers, as panelists on two webinars hosted by Fierce Telecom and Capacity Media respectively. The webinars featured lively discussions on global connectivity patterns and events, trends in RPKI compliance, and how service providers can keep an eye on their market share and competitor activities.
The changing DDoS landscape
As one of the 15 global Tier 1 providers, Orange’s vast network helps keep a pulse on the internet. Sonia shared some global connectivity trends Orange is seeing that will impact network teams this year:
- After record-breaking traffic levels during 2020 and 2021 due to the pandemic, IP transit has leveled out and is returning to pre-Covid levels.
- Increasingly, more critical business is being conducted on IP transit networks due to cloud usage and adoption across the enterprise.
- Leading service providers, including Orange, are investing more in threat mitigation system (TMS) platforms for robust DDoS protection.
For the over 100,000+ networks that make up the public internet, DDoS protection is always top of mind as the first line of network defense against increasing attacks – but analysis from Arelion shows a fundamental shift occurring. During the Fierce Telecom webinar, Mattias presented insights from Arelion’s internal traffic analysis showing DDoS attacks are actually trending downwards, with fewer attacks per week being recorded. This is in stark contrast to 2018-2020, where DDoS attacks increased in both size and volume YoY. What’s behind this? That has yet to be fully analyzed, but coordination between network service providers focusing on rooting out sources of spoofed traffic could be a potential cause for the decline.
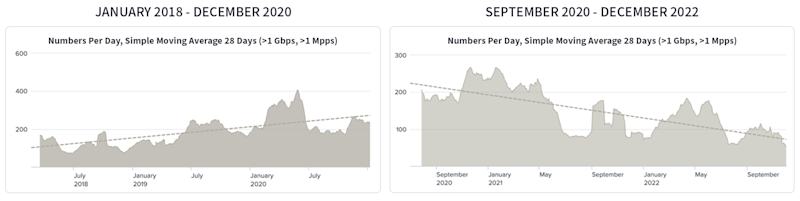
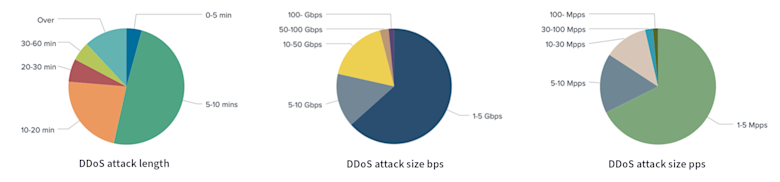
In addition, as part of his analysis, Mattias shared interesting observations about the DDoS threat landscape spanning both volume/sized-based and network protocol attacks. Based on Arelion’s internal data:
- Attack lengths are still very short, with 75% of attacks being less than 20 minutes
- Most common volumetric attacks are less than 5Gbps
- The majority of protocol attacks are lower than 5Mpps
- Attacks are typically carried out after office hours and over weekends
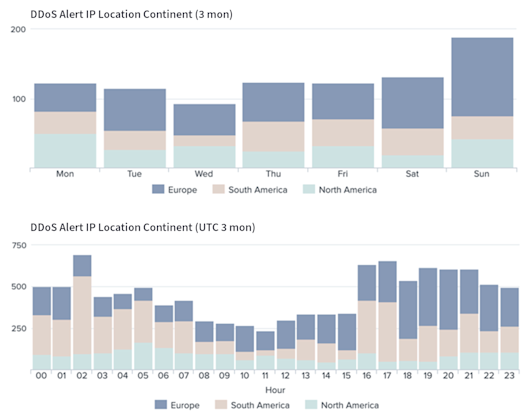
Arelion is seeing significant growth globally in ‘carpet bombing,’ where a range of addresses or subnets, which could contain hundreds or thousands of destination IP addresses, are attacked. Given how swiftly DDoS attacks are carried out, immediate detection and response time are critical to mitigating service downtime. Mattias encouraged service providers to embrace automation for DDoS protection where possible, noting Arelion now auto-mitigates 70+% of DDoS attacks, with only sophisticated cases requiring manual intervention.
Learn more about how Kentik integrates with Cloudflare to mitigate DDoS attacks on demand.
The RPKI tipping point
An update on Resource Public Key Infrastructure (RPKI) Route Origin Validation (ROV) adoption was next on the docket. A leading authority on BGP analysis, Doug Madory presented his latest RPKI adoption findings and gave his take on what it means for the industry moving forward.
As network operators across the internet continue to implement RPKI in a collaborative effort to increase global routing security, Doug noted there are several positive signs that we have reached a true adoption tipping point. To frame the conversation, he first outlined the two steps it takes to reject an RPKI-invalid BGP route:
- Route Origin Authorizations (ROAs) must be created to assert valid origin and prefix length
- Networks must reject RPKI-invalids
On the ROA creation front, the below graphic from NIST shows that the number of routes with ROAs has risen dramatically since 2020 and is on track to outpace routes without ROAs soon. Doug estimates this intersection will occur in the next year, where the majority of routes in circulation will have ROAs and be eligible for protection, thereby cementing RPKI as the internet’s cornerstone defense against hijacks due to accidental typos and leaks.
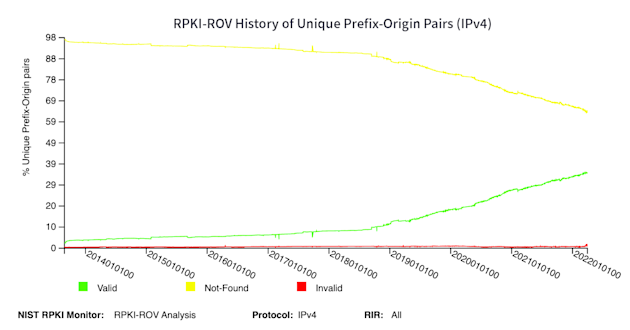
However, by evaluating RPKI adoption using Kentik’s NetFlow traffic data, we can see that the state of ROA creation is better than what the current NIST metrics reflect. Specifically, Doug observed that while only 43% of routes have ROAs and are valid, 63.9% of traffic (in bits/sec) is going to RPKI-valid routes.
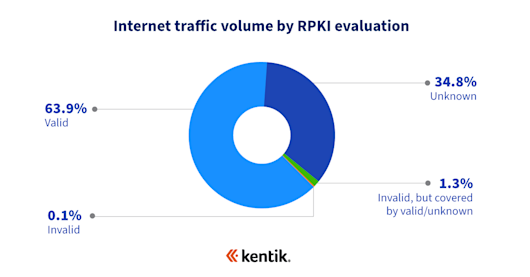
As he described in a blog post last year, this discrepancy can be attributed to RPKI deployments at large content providers and major access networks, which push much of the traffic on the internet.
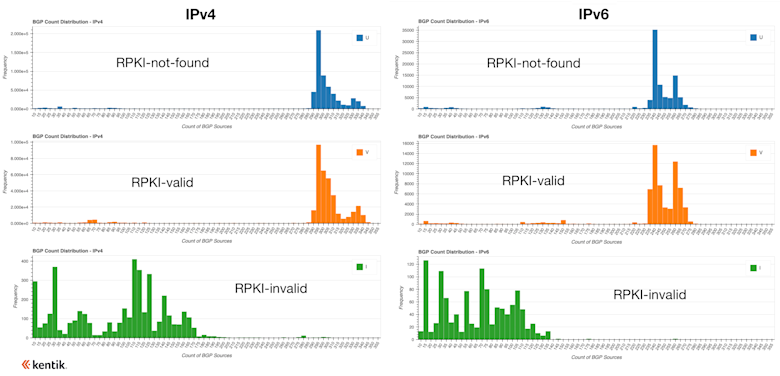
The second part of the RPKI analysis considered the degree to which RPKI-invalid routes are rejected on the internet. Developing a reliable methodology to determine which ASes reject RPKI-invalid routes is an active area of research. But Doug explained that we could see the impact of RPKI on invalid routes without knowing precisely which ASes are rejecting them.
In an analysis from last year, he investigated what happened to BGP routes that are evaluated at RPKI-invalid. The conclusion was that they experienced a reduction in propagation anywhere between one-half to two-thirds.
RPKI success storytime
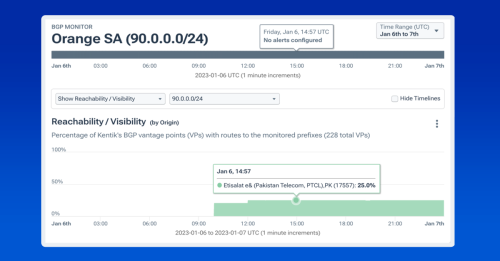
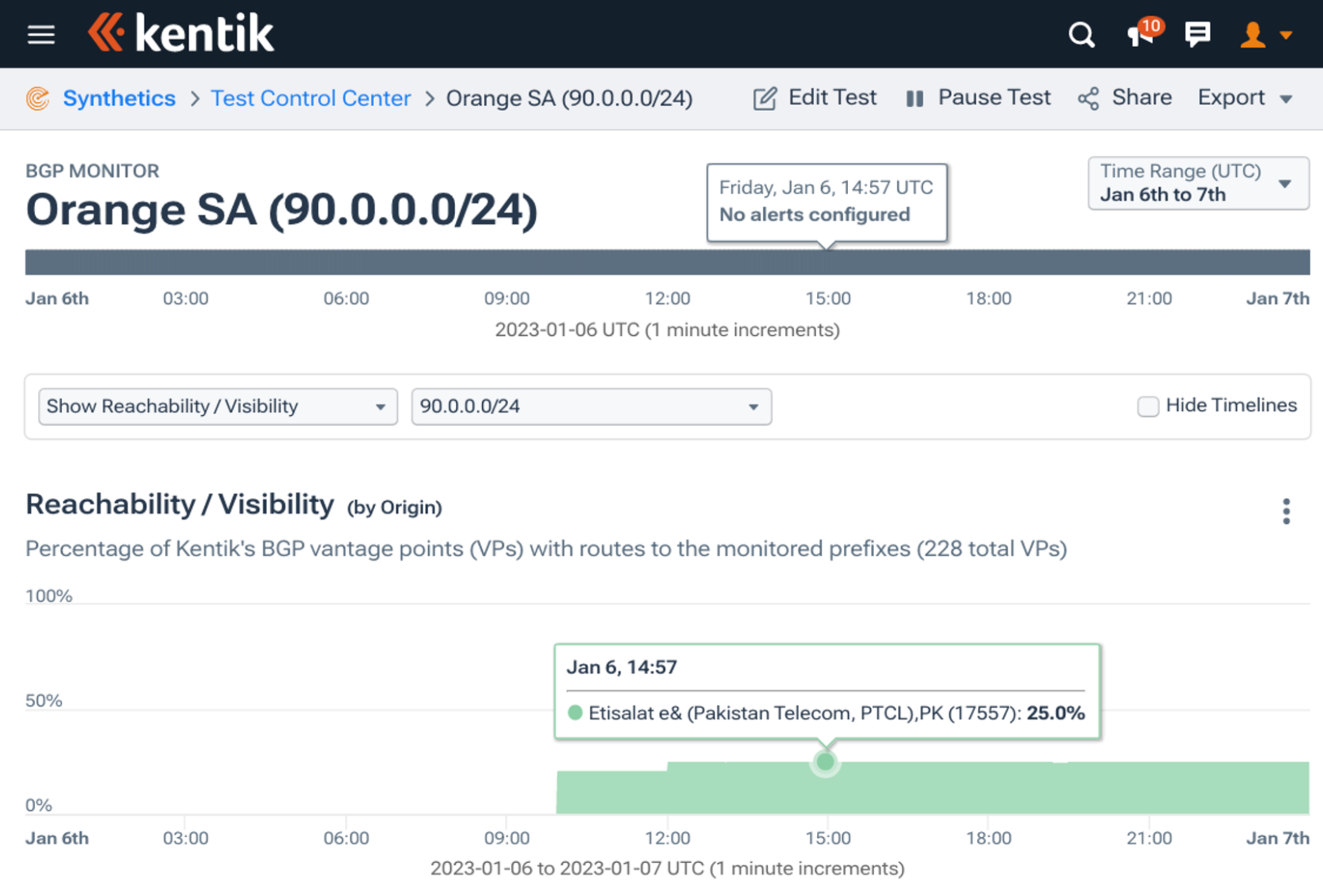
To further illustrate the real-world impact of RPKI adoption, Doug shared a story of it in action. In January, Pakistan’s PTCL accidentally leaked 90.0.0.0/24, which is a more-specific route of Orange’s (AS3215) 90.0.0.0/17. If it had been globally circulated, it could have caused disruptions to Orange customers using that IP address range.
Thankfully the route had an ROA enabling most of PTCL’s providers to reject the leaked route automatically. The screenshot below shows the leaked more-specific route only propagating to 25% of the internet. The limited propagation was due to RPKI and required no human intervention. Once Kentik noticed the leak, we alerted Orange, who contacted PTCL to block the route. If only one more major backbone carrier had RPKI fully implemented, then it likely would not have circulated at all - a reality that we may be on the cusp of achieving.
A natural question then quickly arises – why hasn’t the entire industry adopted RPKI yet? While creating ROAs doesn’t cost providers any money, Doug estimates lack of awareness, older hardware that makes rejecting invalids difficult, and limited engineering team resources are contributing to adoption delays.
During the Q&A portion, a thought-provoking question was offered about whether RPKI is worth doing, given how most internet traffic is transmitted via direct private peering rather than IP transit. Both Doug and Mattias wholeheartedly support RPKI measures, arguing that IP transit is very important, and although it may not be the majority percentage-wise, critical queries and internet traffic travel through IP transit connections that must be secured.
Arelion, the first Tier 1 to fully implement RPKI and a fierce advocate for global routing security, reinforced that the RPKI tipping point is here. Mattias shared how more RFQs from large customers are requiring RPKI – a resounding alarm to backbone carriers and major players that adoption will soon no longer be a choice.
The future of global routing security
While RPKI is not 100% foolproof (AS paths can be forged and slip past it undetected), its widespread adoption is a significant first step in the journey to fully securing BGP. Doug predicts the next routing security frontiers the industry will need to embrace is BGPsec and autonomous system provider authorization (ASPA), which would help close the gap in securing BGP routing from determined adversaries.
How to stay ahead of the curve with market intel
Wrapping up our highlights, Doug gave a quick video walkthrough of the Kentik Market Intelligence (KMI) tool, which both Orange and Arelion use to keep an eye on the market. KMI uses BGP routing data to display AS transit and peering relationships for any market in the world, equipping service providers with instant access to data to better understand their market share and customer and competitor activities.
Be sure to watch the webinar recording to see the full demo, where Doug walks through network planning, sales, and marketing use cases for the tool.
Have questions or want to learn more? Sign up for a personalized demonstration or start a trial to see Kentik in action.


