One View to See Them All
On prem, private cloud, public cloud — all in one view.
Live blueprints
See how all networked resources nest within and connect to each other.
Unified infrastructure
Understand path, performance, health, and security from on-prem to cloud.
Instant answers
Know whether the network is impacting application performance, and see how to fix it.
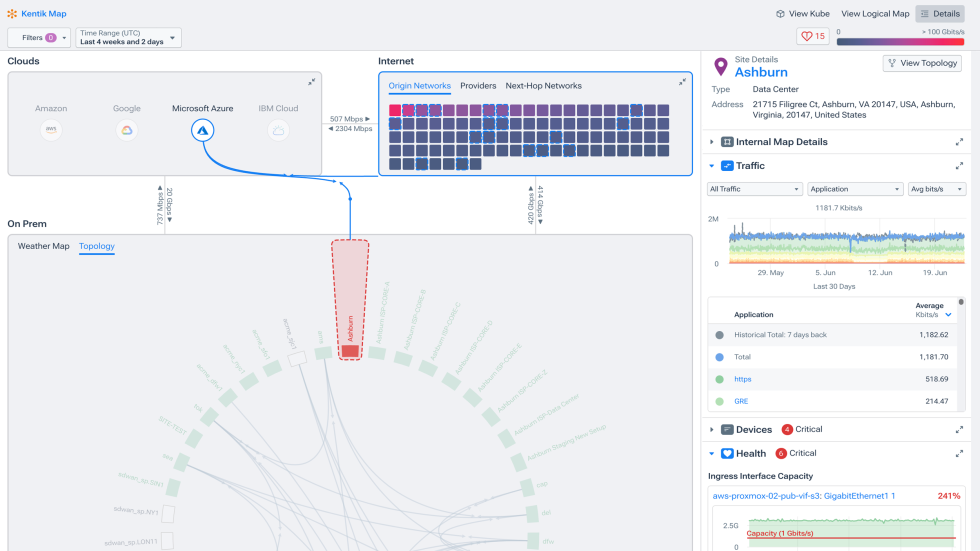
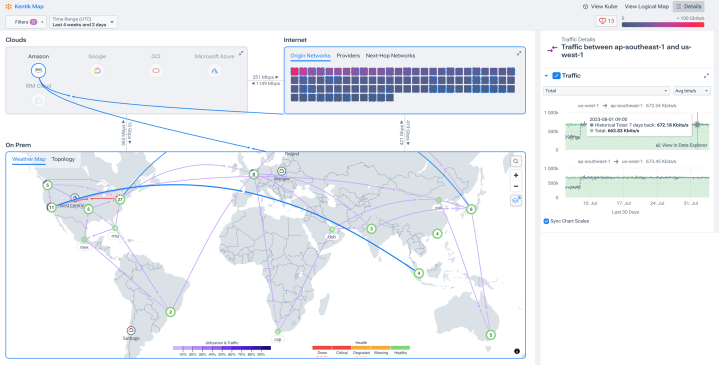
Visualize and investigate interconnect and multi-cloud topology
- See cloud topology across the major public clouds.
- Discover, manage, and troubleshoot Cloud Interconnect connections between your private and public clouds.
- Understand at a glance how cloud subnets and network infrastructure are designed and interconnected.
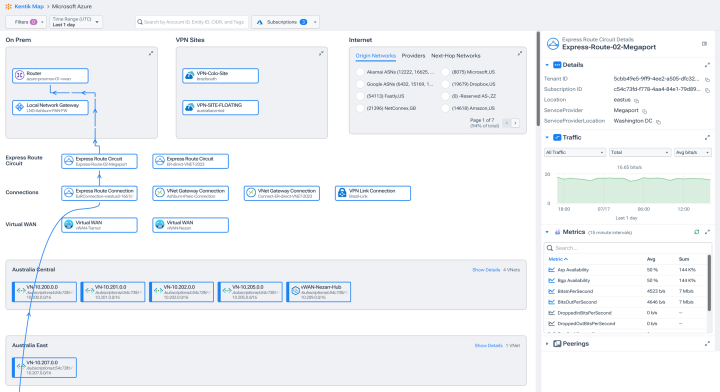
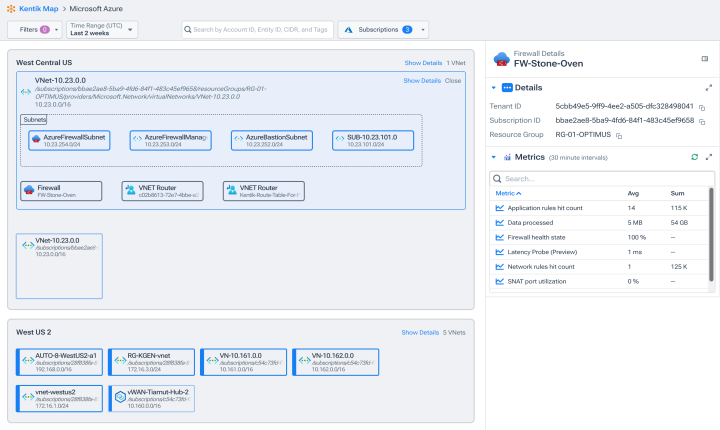
See critical detail with big picture context
- Easily access utilization, configuration, and performance data right from the map.
- Fix errors and optimize with rich metrics on cloud load balancers, firewalls, security groups, and application gateways.
- Get quick insight into SD-WAN, branch, VPN, private cloud, and intra-cloud connectivity.
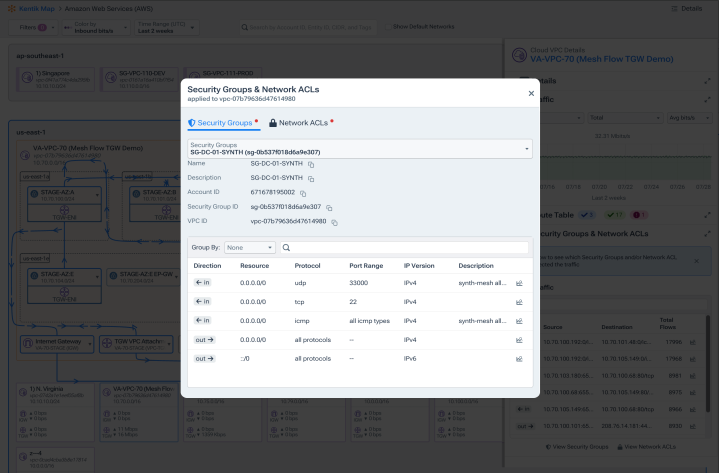
Know where your data travels
- Quickly see denied and allowed traffic between VPCs, VNets, data centers, and the public internet.
- Verify with a visual that perimeter, security group, and Access Control List (ACL) rules match your security model.
- Visually detect anomalies in fast traffic explorations.
Make every decision with a current architectural blueprint
- Get always-up-to-date visualizations of your latest hybrid network infrastructure, automatically.
- Optimize ROI of moving resources to and from cloud with a complete picture of dependencies.
- Plan capacity, manage infrastructure, and onboard team members with a reliable source of truth.
Major League Baseball
“Kentik is actually showing you a visual representation of how your physical equipment connects via those virtual private connections in the cloud.”
Jeremy Schulman
Principal Network Automation Software Engineer, Major League Baseball
Navigating the Complexities of Hybrid and Multi-cloud Environments
Explore the platform
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.


