Complete Hybrid and Multi-Cloud Network Observability
Empower teams to answer any question about cloud traffic, connectivity, or performance.
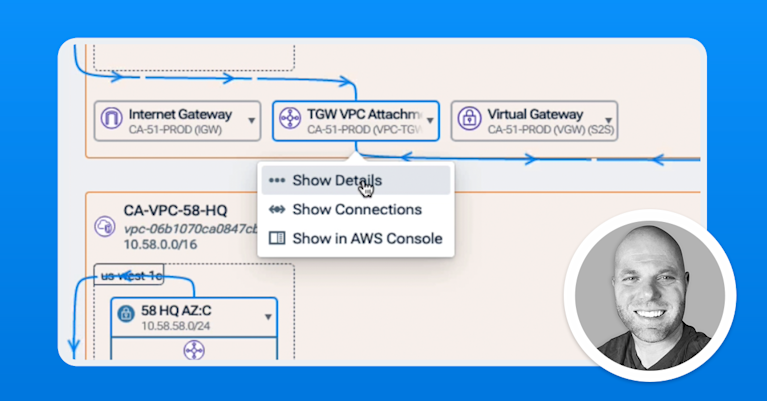
 Understand hybrid cloud connectivity and health
Understand hybrid cloud connectivity and health
- Visualize infrastructure from data center to AWS, Azure, Google Cloud, OCI, IBM Cloud, and Kubernetes environments in an interactive, context-rich map.
- Instantly see cloud resource topology and interconnects to data center environments with an automated source of truth.

 Get alerts on critical anomalies and insights
Get alerts on critical anomalies and insights
- Find out about compliance and security risks that matter to your business immediately with custom alerts.
- Know where your traffic is going, and whether inter-region data exchange is compliant.
- Automatically flag communication with watchlisted hosts.
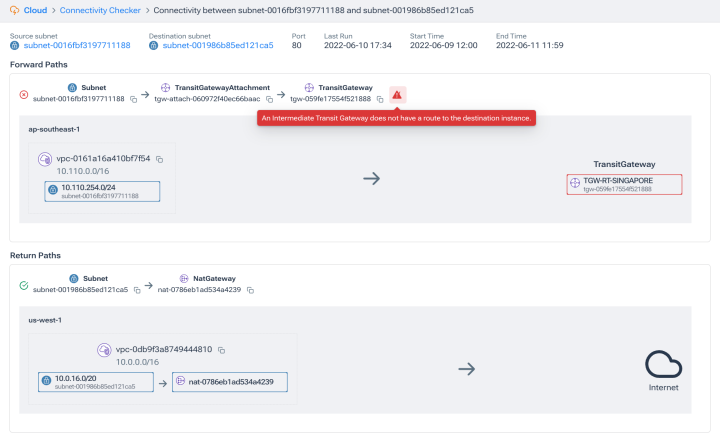
 Troubleshoot instantly with Connectivity Checker
Troubleshoot instantly with Connectivity Checker
- Check live connectivity between any instance, subnet, or network interface on demand.
- Get detailed insights into connectivity problems with visualization of where connectivity is blocked.
- Search by IP, CIDR block, VPC ID, Subnet ID, or DNS name to quickly pinpoint connectivity.
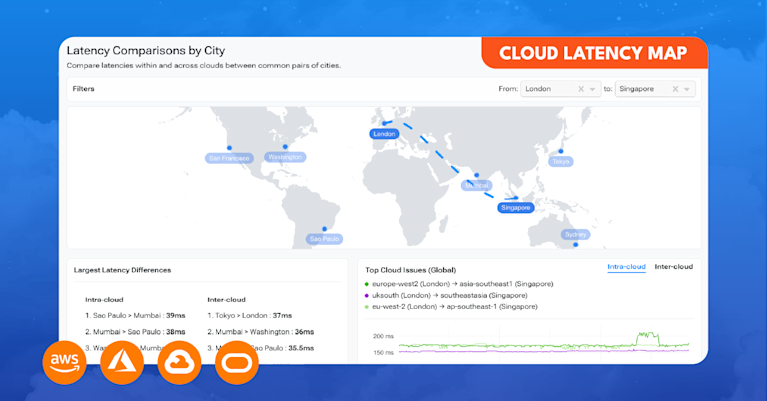
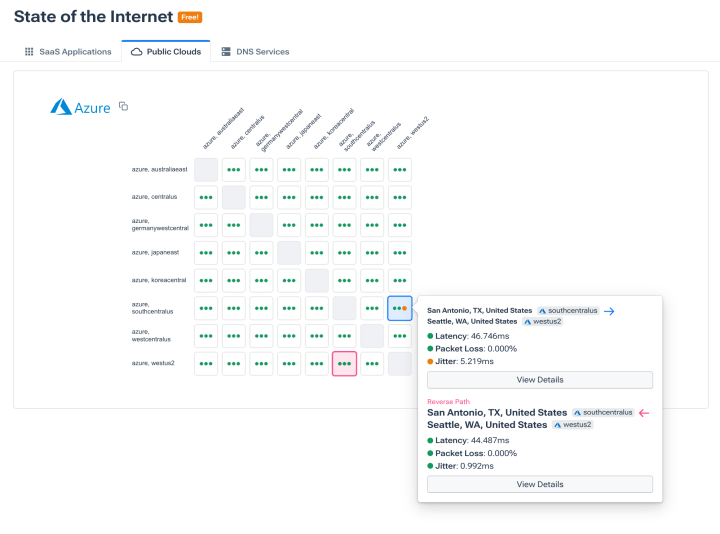
 See public cloud performance, uptime, and connectivity
See public cloud performance, uptime, and connectivity
- Check Kentik State of the Internet to identify cloud provider latency and outages across regions and products.
- Quickly troubleshoot SaaS and external dependency issues with real-time status of SaaS companies and DNS Services.
- Configure global synthetic tests to detect issues with mission-critical upstream services.
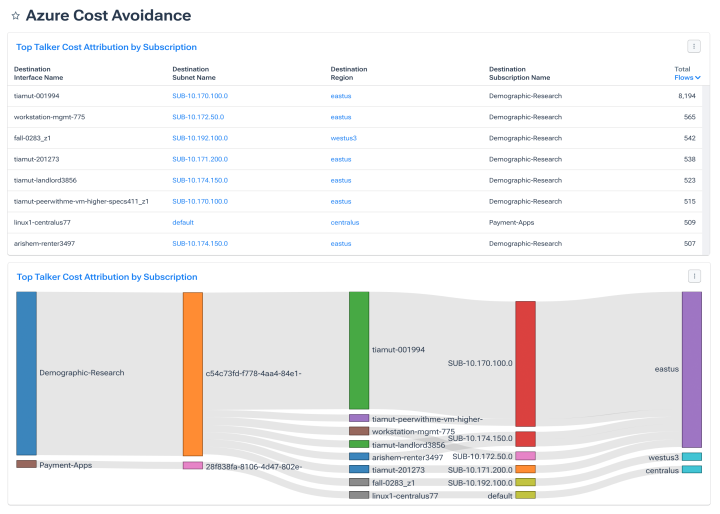
 Excel at cloud migration
Excel at cloud migration
- Quickly optimize customer experience with insights from synthetic tests and real-time, hybrid cloud traffic data.
- Automatically analyze cloud usage trends and attribution to fine-tune cloud capacity and redundancy.
- Analyze traffic before, during, and after migration to balance performance with cost.
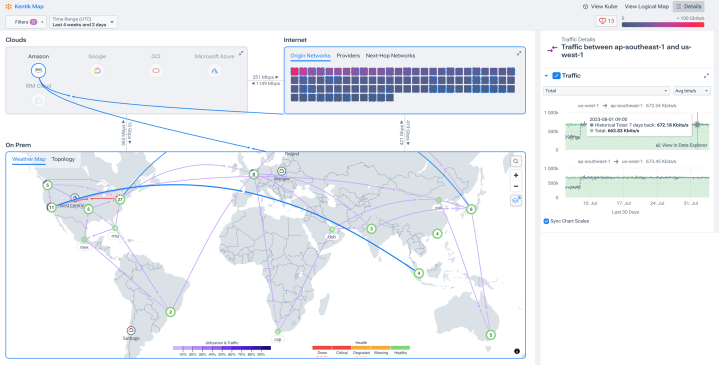
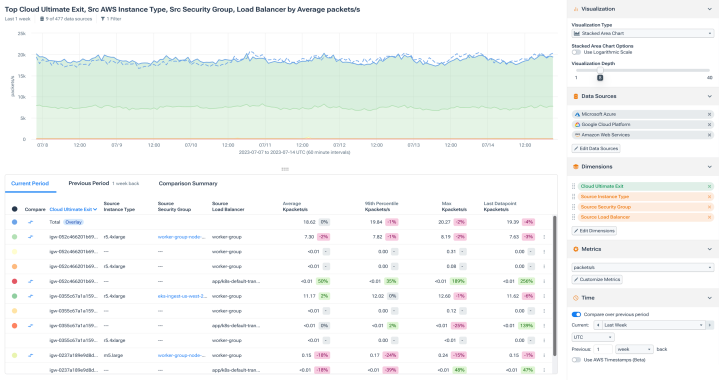
 Rapidly interrogate network data in Data Explorer
Rapidly interrogate network data in Data Explorer
- Get instant answers to “unknown unknowns” with blazing-fast queries of network and infrastructure data from all your clouds.
- Understand, compare, and visualize real-time and historical connectivity and performance.
- Automatically enrich data with your business, application, and security context.
Major League Baseball
“Kentik is actually showing you a visual representation of how your physical equipment connects via those virtual private connections in the cloud.”
Jeremy Schulman
Principal Network Automation Software Engineer, Major League Baseball
Product demo: Kentik Cloud for Hybrid and Multi-cloud Networking
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.