The Kentik Network Intelligence Platform
All your networks in one place.
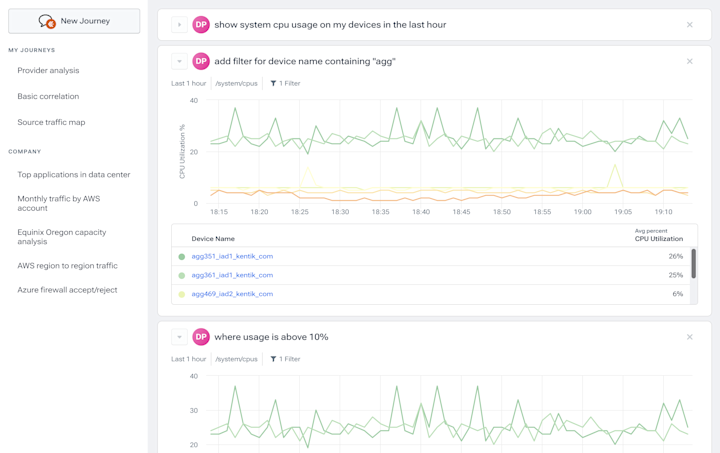
Kentik AI
- Expedite problem solving with assisted troubleshooting workflows and automatic insights.
- Explore telemetry in any language and find immediate answers to network issues from cloud, to data center, to WAN.
- Detect anomalies, prevent DDoS, and analyze BGP and peering with ML enterprises trust.
Learn more about Kentik AI.
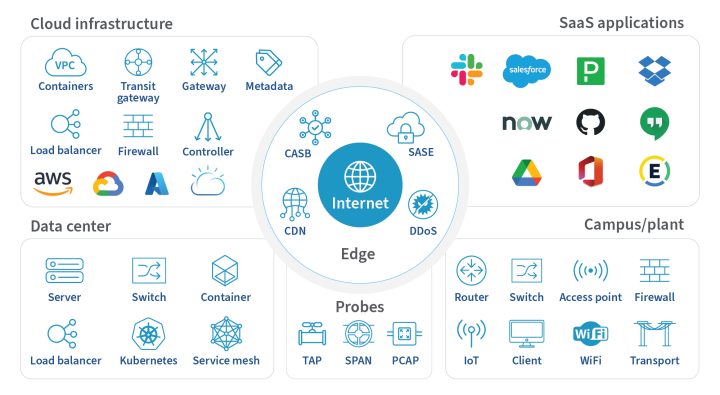
Network Telemetry
- Collect telemetry input from all critical networks and forwarding elements.
- Visualize a unified view across all your networks, even the ones you don’t own.
- Seamlessly scale to collect all telemetry during peak times.
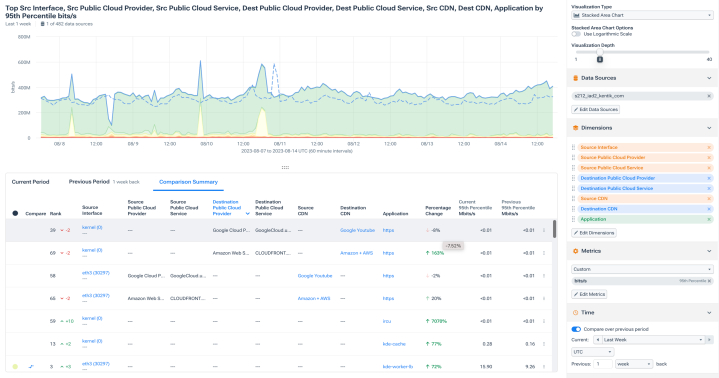
Universal Data Explorer
- Ask any question of your network.
- Intuitively filter any query to get the data you need.
- Query all your telemetry with speed and efficiency.
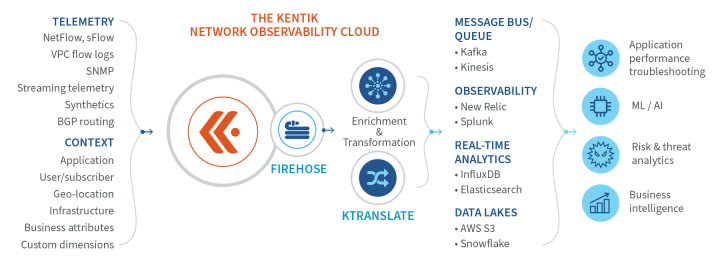
Observability Data Pipeline
- Export enriched data anywhere, other analytics tools or data lakes.
- Reduce costs and improve speeds with aggregate ingest pipelines.
- Normalize telemetry to make it consumable in multiple formats.
Learn more about Kentik Firehose.
Integrations
- Integrate with the tools your team already loves.
- Collaborate with your platforms of choice.
- Automate attack mitigation as soon as they are detected.

Kentik Data Engine
- Access and query quickly with a clustered, multi-tenant platform.
- Ingest high volumes of structured and unstructured data.
- Visualize data in real time and retain raw data for months for accurate troubleshooting and forensics.
Get network intelligence from Kentik.
We use cookies to deliver our services.
By using our website, you agree to the use of cookies as described in our Privacy Policy.