Webinar recap: A NetOps guide to DDoS defense

Summary
Didn’t have time to watch our NetOps guide to DDoS defense webinar with Cloudflare? This blog recaps what was presented and discussed.
We recently broadcast a webinar to discuss DDoS trends and developments. Our partner Cloudflare had their cybersecurity evangelist, Ameet Naik, join us along with our own Doug Madory, head of internet analysis. I had the pleasure of moderating the discussion.
DDoS attack trends
Ameet got the presentation started with an update on DDoS attack trends. Cloudflare has incredible visibility of global internet traffic and attack trends due to its presence in 275 cities globally with over 11,000 networks directly connecting to them. They block 117 billion cyber threats each day. Highlights included that SYN attacks account for more than 50% of Q2, 2022 network-layer DDoS attacks. Other significant threats were attributed to:
- 17.6% DNS
- 7.8% RST
- 6.7% UDP
In terms of the emerging threats, Cloudflare detected significant rises in the following:
- CHARGEN up 378%,
- Ubiquiti up 328%
- Memcached up 287%
Ameet gave a brief description of the profile of these attacks and the impact they can have.
Next was the Russian vs. Ukraine cyber war. Ameet spoke about how entities targeting Ukrainian companies appear to be trying to silence information. The most attacked industries in Ukraine are broadcasting, internet, online media, and publishing. Attacks on these industries make up almost 80% of all DDoS attacks targeting Ukraine.
Concerning attacks on Russian cyber assets, the Russian banks, financial institutions and insurance (BFSI) companies came under the most attacks. Almost 45% of all DDoS attacks targeted the BFSI sector. The second most targeted was the cryptocurrency industry, followed by online media.
Ransom DDoS attacks
The number of respondents reporting threats or ransom notes in Q2 increased by 11% QoQ and YoY. These attacks involve demanding a ransom to be paid if you want the attacks to stop. During this quarter, Cloudflare has been mitigating ransom DDoS attacks that have been launched by entities claiming to be the Advanced Persistent Threat (APT) group “Fancy Lazarus.” The campaign has been focusing on financial institutions and cryptocurrency companies. There was some discussion about these attacks being correlated with high seasons — note the historical peak in December.
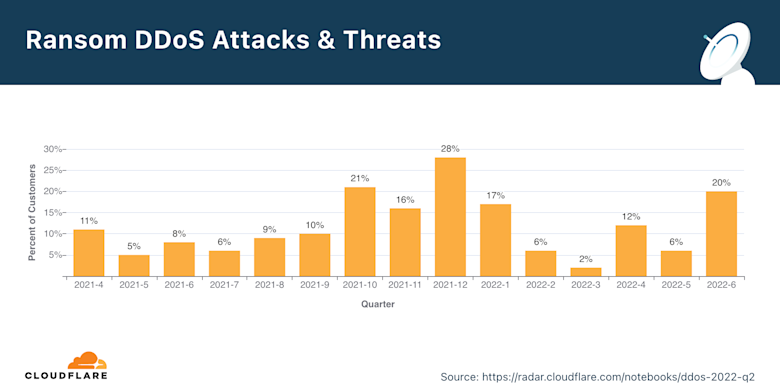
Next were some key observations about the DDoS threat landscape: Most DDoS attacks are cyber vandalism, which can be powerful and cause damage.
Sophisticated, large, or well-funded attacks are rare, but hit hard and fast. They are initiated by humans, but executed by machines. Attackers can be very persistent in learning your network topology and identifying weak points.
Ameet concluded with an overview of the Cloudflare approach to DDoS protection and how Kentik integrates with Cloudflare to trigger mitigation. If you’d like to learn more about how this integration works, please read our blog post Working with Cloudflare to mitigate DDoS attacks from earlier this year.
BGP and DDoS mitigation
Our internet analyst was up next. Doug Madory is a leading authority on BGP analysis. He started the discussion with an interesting story about the origins of Prolexic, how they used BGP to protect an off-shore gambling site from DDoS attacks, and how he got involved with the New York Times and their online gambling investigation. You’ll have to listen to the webinar to hear Doug tell the story — or what he was willing to share publicly.
Doug then outlined the role BGP plays in DDoS mitigation and what can go wrong, including:
- A mitigation vendor announcement getting filtered based on RPKI or IRR data.
- Previous upstream(s) don’t stop announcing when the mitigation vendor begins leading to contention and incomplete activation.
- Some other problems with the signaling to the mitigation vendor affecting the timing of the activation.
Kentik has some new visualizations of DDoS mitigation activations that Doug has been leading. These views use Kentik synthetic agents to view BGP announcements from hundreds of vantage points. Companies using a BGP-based DDoS mitigation service generally cannot see how fast or complete the mitigation is when they are under attack. As you can see from the following visualizations, Kentik has a solution.
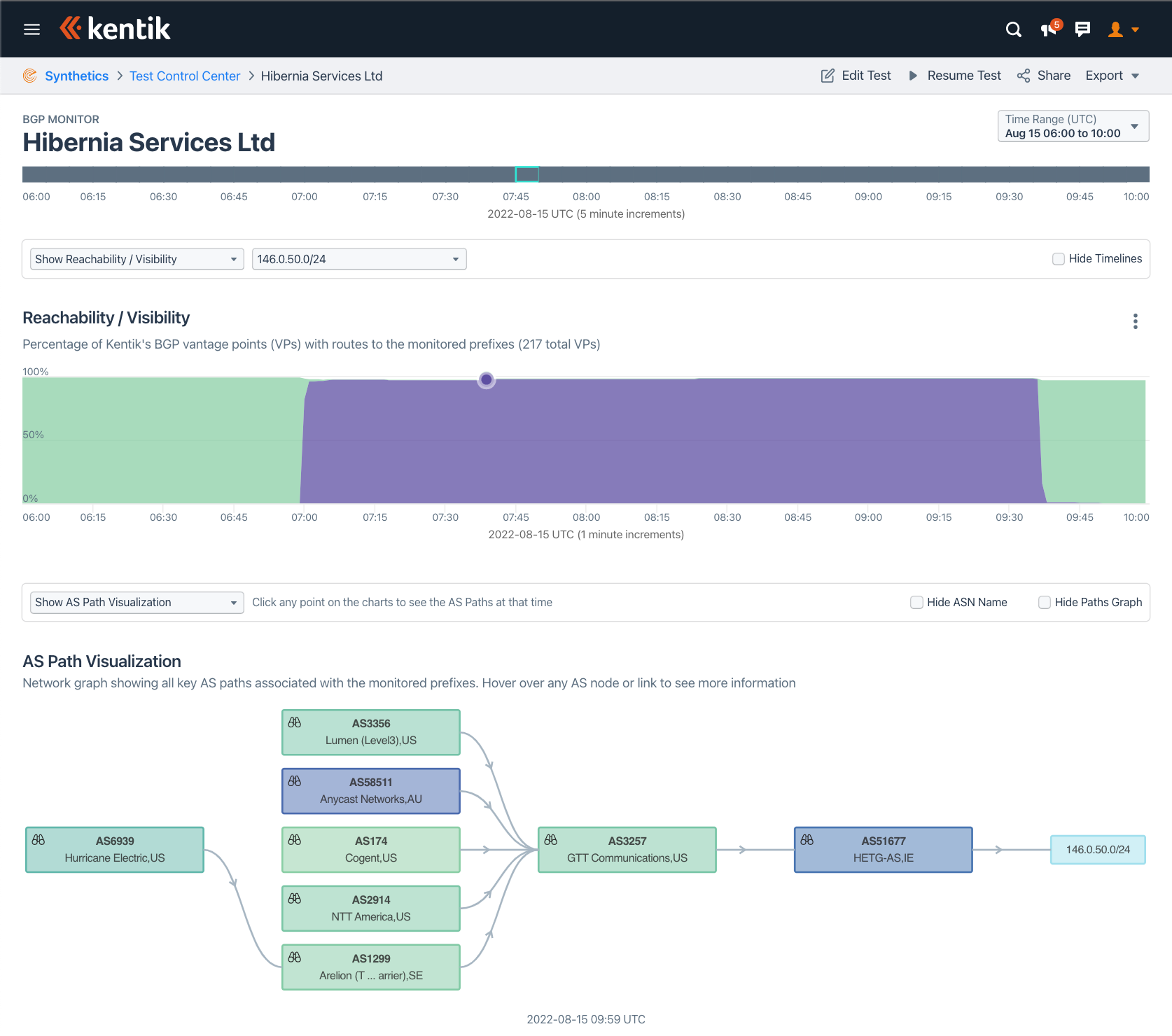
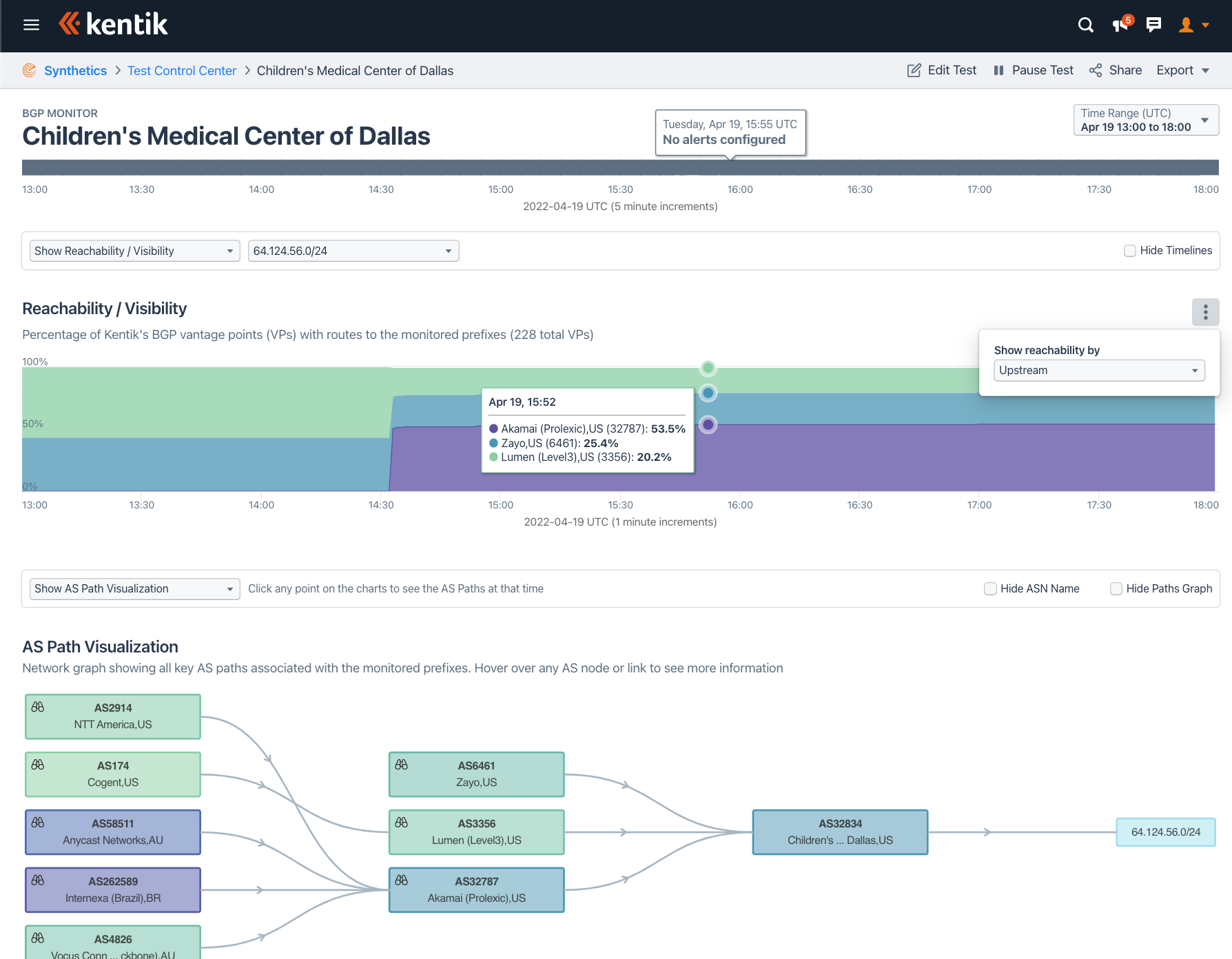
Ameet mentioned that he often gets asked how long it takes for a mitigation to propagate fully. Well, with these visualizations he can now answer that question.
Why network observability is critical to DDoS defense
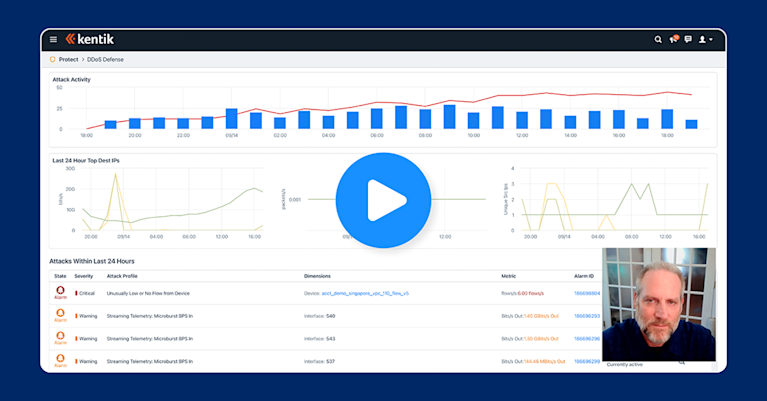
Before the Q&A, I concluded the webinar with a recap of my recent blog 8 reasons why observability is critical to DDoS defense. Don’t miss the video walk-through of Kentik Protect showing how we detect and analyze DDoS attacks.
Also, learn more about monitoring BGP in the context of DDoS mitigation in this short video.
Don’t hesitate to reach out if you have questions or want a personal demonstration.