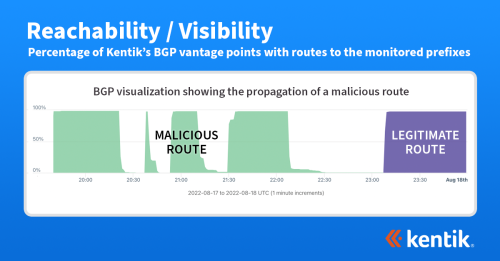
How Kentik Visualizes the BGP Propagation of a DDoS Mitigation


Summary
At first glance, a DDoS attack may seem less sophisticated than other types of network attacks, but its effects can be devastating. Visibility into the attack and mitigation is therefore critical for any organization with a public internet presence. Learn how to use Kentik to see the propagation of BGP announcements on the public internet before, during, and after the DDoS attack mitigation.
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.
DDoS targets
DDoS attacks can take place against publicly available websites and even entire content delivery networks, but often they’re targeted against specific IP addresses representing some piece of infrastructure or a corporate network.
These targeted attacks are usually committed to reducing a service’s availability or completely taking down a corporate network’s public availability on the internet. The IP addresses in these attacks are public addresses configured on internet-facing routers and used to announce routing information to the public internet.
An organization announces its routing information to the world using a unique autonomous system number, or ASN, that is used as a unique identifier in the great sea of organizations also announcing themselves on the internet. Both the organization’s network information, in terms of IP addresses, and its ASN, are propagated using the Border Gateway Protocol, or BGP, to “announce” to the world the availability and reachability of the network.
Therefore, mitigating these types of targeted DDoS attacks must focus on protecting these external IP addresses and an organization’s unique ASN.
DDoS mitigation
Today, the most common DDoS mitigation method is for an organization to partner with a third-party DDoS mitigation service that will assume the public BGP route announcement of the company being attacked.
When a visibility tool, such as Kentik Protect, sees the beginnings of a DDoS attack, an organization can start the mitigation process by coordinating the transfer of their routing to the mitigation vendor. This way, the attackers will see the third-party mitigation vendor as the source of the IP addresses and send their malicious traffic to them rather than the original target.
“With Kentik, we can pinpoint the source of suspicious traffic virtually in real time.”
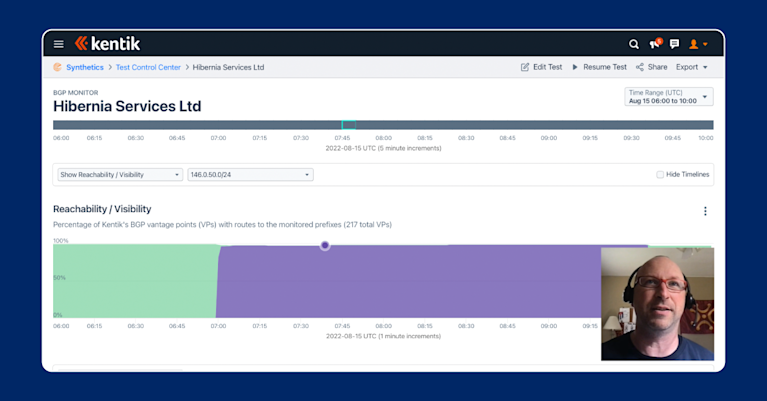
– Tatsuya Mori, Senior Manager of IT Infrastructure/NetworkNotice in the screenshot below from a demonstration by Doug Madory, Kentik’s director of internet analysis, that we can clearly see the moment Cloudflare, a DDoS mitigation provider, took over routing announcements for Hibernia Services, Ltd.

The third-party mitigation service will then scrub the traffic and forward it back to the originally intended recipient organization using a tunnel, usually GRE, to obfuscate the mitigation process from the attacker.
BGP propagation
DDoS mitigation ultimately depends on the proper operation of BGP on the public internet. This means that the time it takes for the mitigation vendor and the process to take over for their customer is urgent, albeit nuanced.
For the mitigation to occur, the victim must stop announcing its networks via BGP to the public internet. Simultaneously, the mitigation vendor must take over and announce those same networks on their customer’s behalf. If there is overlap, there can be routing contention on the internet. If there’s a delay, the victim’s network could be adversely affected by the DDoS attack or simply offline because no routing announcements occur during the switchover.
However, the nuance goes deeper. There may also be filtering in place by another service provider, which breaks when the mitigation vendor takes over. An organization may experience a performance degradation of their service, an e-commerce website, for example, due to the path changes and filtering happening on the internet.
Visualizing BGP announcements
Considering a DDoS attack and its mitigation can take many minutes and affect an organization’s line of business application(s), visibility into the various elements of the process is crucial. For example, an organization under attack will need visibility into the following:
- When an attack occurred
- When the mitigation activation took place
- How effective that mitigation is
- How routes are being announced before, during, and after the mitigation
- When the mitigation ends
Most organizations can’t afford to have a visibility blindspot that lasts many minutes, especially during this type of crisis, so visualizing these elements is very important to managing the attack and returning to normal.
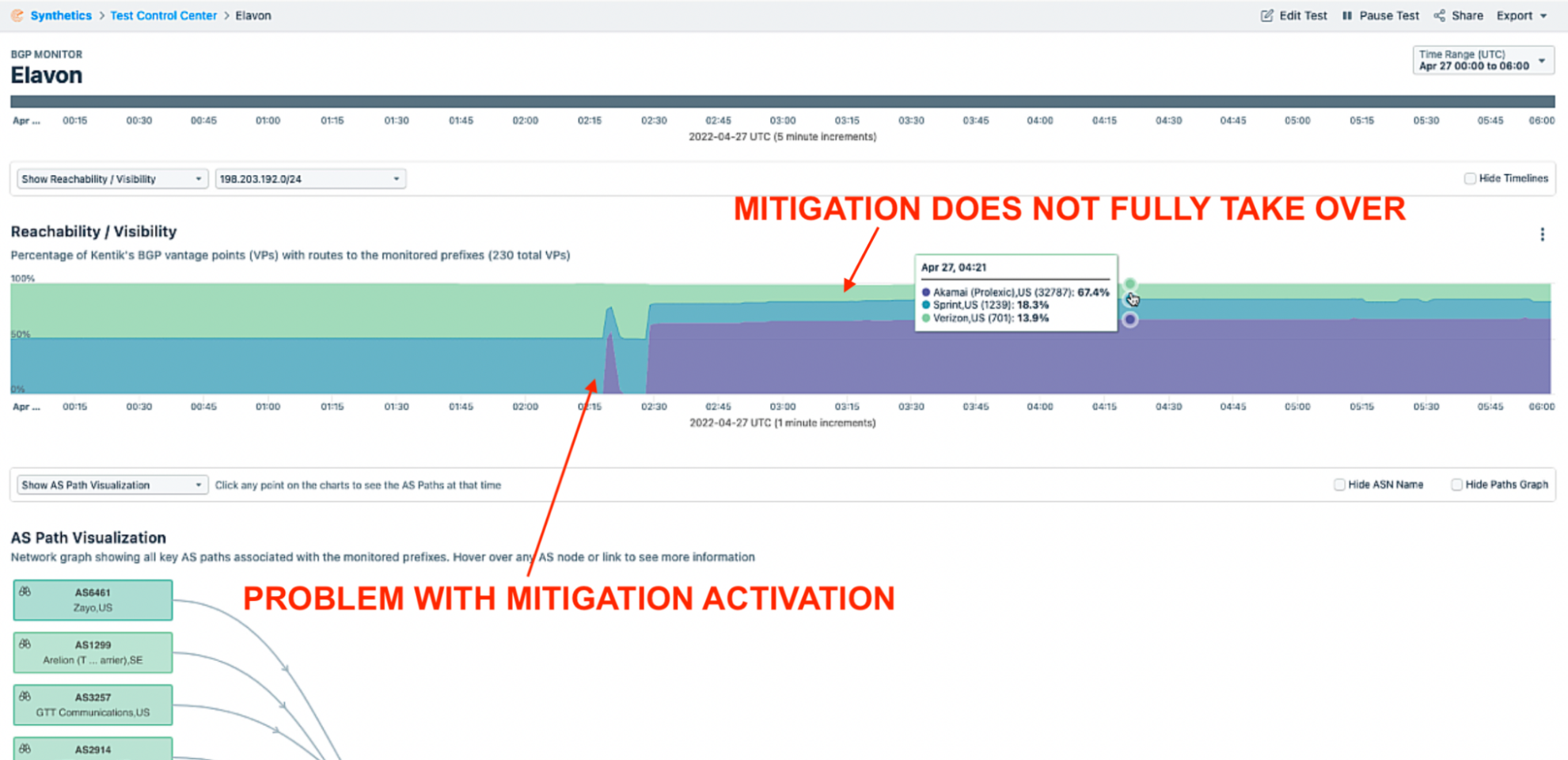
In the graphic below, notice we can see when the mitigation was activated. There was also a problem with the activation, and the mitigation provider never entirely took over routing announcements for the victim. This would mean both a delay in the mitigation activation and contention with routing on the public internet. As a result, there would be reachability problems to the victim’s network and publicly available services. This specific kind of network visibility is crucial to managing an attack successfully.
Kentik’s unique visibility capability
Kentik provides visibility into an organization’s routing announcements before, during, and after a DDoS attack and mitigation. Using Kentik Protect and Kentik’s synthetic testing functionality, we can recognize the beginnings of a DDoS attack, alert the network team, and activate automated mitigation. More precisely, we can detect the exact moment an activation occurred, its effectiveness, when it ended, and if/when routing returned to normal.
At first glance, a DDoS attack may seem less sophisticated than other types of network attacks. Still, because it directly impacts BGP routing announcements to the world, it is nevertheless devastating. Visibility into the attack and mitigation is therefore critical for any organization with a public internet presence.
Watch this video interview and demonstration to learn more about DDoS mitigation and Kentik’s unique ability to provide visibility into the entire process before, during, and after.