Accuracy and Efficiency for Network Security

Summary
This guest post brings a security perspective to bear on network visibility and analysis. Information security executive and analyst David Monahan underscores the importance of being able to collect and contextualize information in order to protect the network from malicious activity. Monahan explores the capabilities needed to support numerous network and security operations use cases, and describes Kentik Detect as a next-generation flow analytics solution with high performance, scalability, and flexibility.
Kentik delves deeper into your data for detection and defense
According to 2015 research reports published by Ponemon, Mandiant, and others, the median pre-detection dwell time for an intruder in a target network ranges at around 200 days. We can all agree that having an undetected intruder for over six months is totally unacceptable, but there seems to be little solid agreement on how to solve the problem. The typical pat answers — “use better security” or “patch your vulnerabilities” or “practice least privilege” — may be sound pieces of advice, but they are clearly not getting us where we need to be. Why? Because they focus on the preventative aspects of security which, though valuable, are inherently imperfect.
Truly reducing dwell time isn’t primarily about prevention, it’s about detection. Detection requires visibility and analysis. Visibility requires information, and analysis requires the ability to contextualize the information. Thus, reducing dwell time requires a better ability to capture and contextualize information.
Over 95% of IT security attacks traverse some aspect of a network to execute. Whether a local LAN, a private WAN, or the Internet, a network functions as the circulatory system for a body of knowledge. To get the data we need, we must tap into that flow. Medical professionals monitor blood pressure and cholesterol to understand the basics of health, but when there is a problem, they have to dig deeper for things like blood-gases, toxins, and pathogens. The same is true for networks. IT performs performance checks on interfaces to understand the basics on network health but when there is a real problem, they have to gather more data from the traffic on the lines.
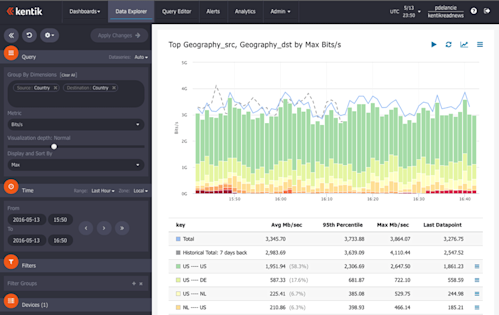
One way to gather this data is with Kentik Detect™ (above), a solution designed to solve many visibility issues, supporting both IT and security operations. Kentik Detect collects network telemetry at service provider speed and scale, ingesting and storing terabits of full-resolution network data including NetFlow, Geo-IP, BGP, SNMP, and network performance data. The data is not merely correlated but fully unified to create useful metadata for enhanced context. Kentik Detect’s Big Data engine also provides advanced analysis and alerting capabilities to make operations and security professionals aware of issues and incidents.
Kentik Detect doesn’t just provide visibility — with scalability and performance — into communications patterns, protocol usage, top talkers, and other commonly used troubleshooting information. It also provides an analysis engine that goes beyond what many other network data capture tools provide, including visualization tools that deliver at the level of Big Data analytics.
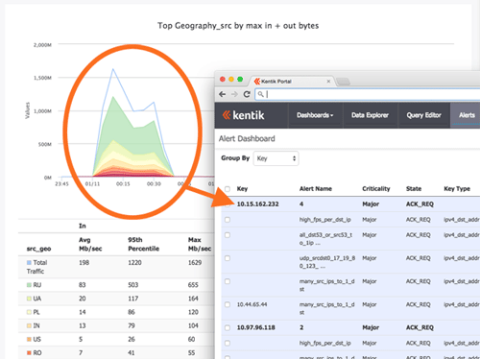
Kentik Detect isn’t yet a DDoS remediation tool, but it can be very useful in identifying network-based attacks such as DDoS. While many tools have an easy time catching volumetric attacks, other attacks such as those targeting specific system resources, protocols, and applications can be far more difficult to identify. These types of attacks often go unnoticed by IT teams because they do not exceed thresholds set to identify a volumetric attack. In cases where the DDoS is a smoke screen for another attack, Kentik Detect provides a single tool for identifying and analyzing both the DDoS and the underlying attack.
Kentik’s value proposition is based on the combination of cloud scalability and big-data analytics, which creates agility for detection and defense of network-borne incidents. Kentik Detect can provide customers with effectively unlimited storage for collected data, so that any event can be researched back to the start of service or start of the event, whichever comes first. The query engine has Google-like response times for ad-hoc queries involving multi-dimensional field grouping and filtering across terabyte-sized datasets, removing one of the most common operational frustrations with query tools. Another feature that adds value is the ease with which a query can be converted into an alert. If operations defines a set of conditions that they want to track, a SQL-based query can then be used to create an ongoing alert. This is a fantastic time-saver for numerous operations scenarios.
All in all, Kentik is positioned to offer next-generation network flow analytics with the high performance, scalability, and flexibility needed to support numerous network and security operations use cases.
David Monahan is a senior information security executive with years of experience in physical and information security for Fortune 100 companies, local governments, and small public and private companies.


